mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2026-01-19 16:10:27 -08:00
Command injection rewritten
This commit is contained in:
|
Before Width: | Height: | Size: 175 KiB After Width: | Height: | Size: 175 KiB |
@@ -2,7 +2,14 @@
|
||||
|
||||
> Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files. - OWASP
|
||||
|
||||
Tools :
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
* [Exploit](#exploit)
|
||||
* [Examples](#examples)
|
||||
* [References](#references)
|
||||
|
||||
## Tools
|
||||
|
||||
- Burp Suite plugin Authz
|
||||
- Burp Suite plugin AuthMatrix
|
||||
@@ -10,7 +17,7 @@ Tools :
|
||||
|
||||
## Exploit
|
||||
|
||||

|
||||
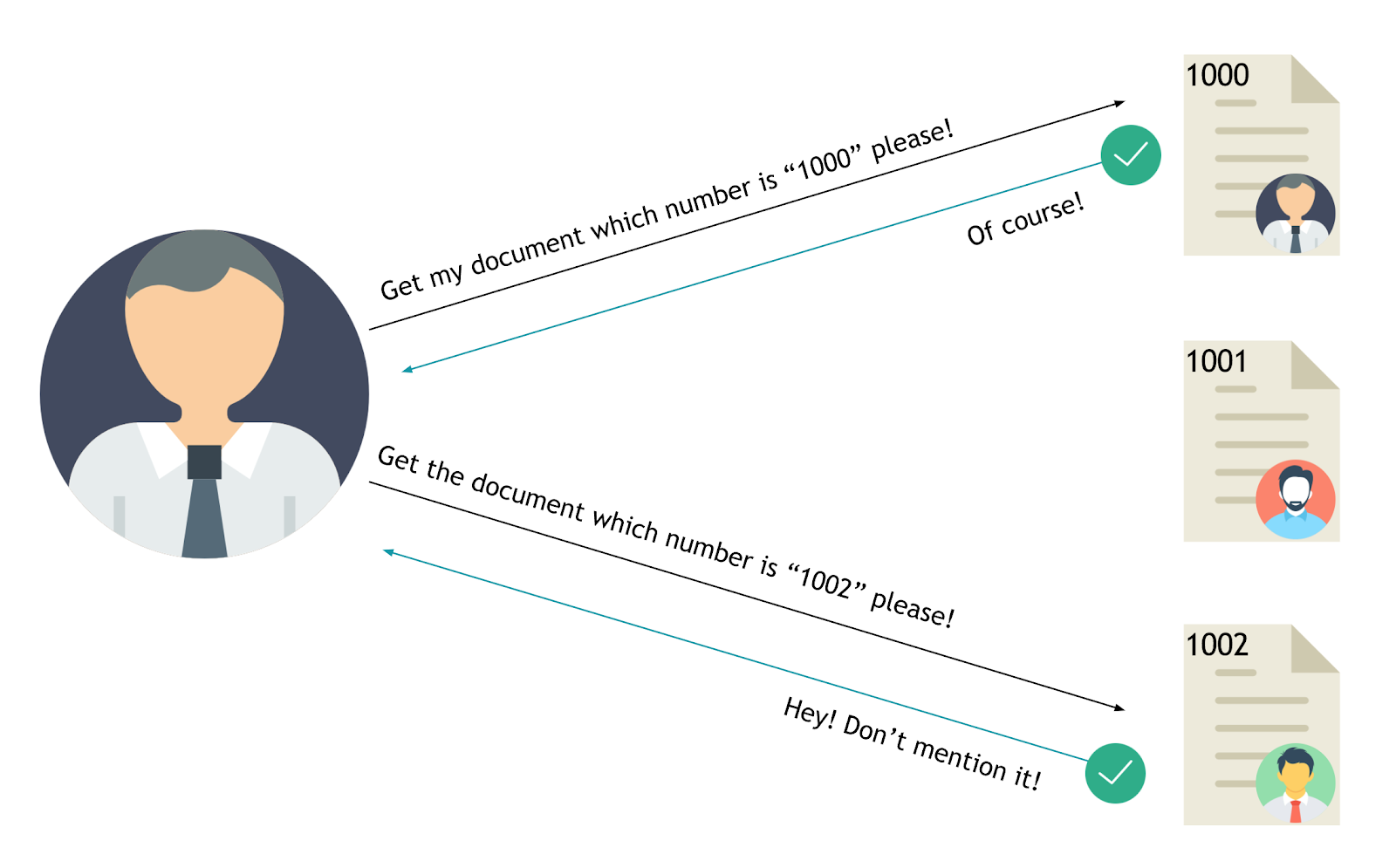
|
||||
|
||||
The value of a parameter is used directly to retrieve a database record.
|
||||
|
||||
@@ -49,3 +56,4 @@ http://foo.bar/accessPage?menuitem=12
|
||||
* [IDOR tweet as any user](http://kedrisec.com/twitter-publish-by-any-user/) by kedrisec
|
||||
* [Manipulation of ETH balance](https://www.vicompany.nl/magazine/from-christmas-present-in-the-blockchain-to-massive-bug-bounty)
|
||||
* [Viewing private Airbnb Messages](http://buer.haus/2017/03/31/airbnb-web-to-app-phone-notification-idor-to-view-everyones-airbnb-messages/)
|
||||
* [Hunting Insecure Direct Object Reference Vulnerabilities for Fun and Profit (PART-1) - Mohammed Abdul Raheem - Feb 2, 2018](https://codeburst.io/hunting-insecure-direct-object-reference-vulnerabilities-for-fun-and-profit-part-1-f338c6a52782)
|
||||
Reference in New Issue
Block a user