mirror of
https://github.com/HackTricks-wiki/hacktricks-cloud.git
synced 2025-12-28 05:33:10 -08:00
Migrate to using mdbook
This commit is contained in:
182
src/pentesting-cloud/workspace-security/gws-persistence.md
Normal file
182
src/pentesting-cloud/workspace-security/gws-persistence.md
Normal file
@@ -0,0 +1,182 @@
|
||||
# GWS - Persistence
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
> [!CAUTION]
|
||||
> All the actions mentioned in this section that change setting will generate a **security alert to the email and even a push notification to any mobile synced** with the account.
|
||||
|
||||
## **Persistence in Gmail**
|
||||
|
||||
- You can create **filters to hide** security notifications from Google
|
||||
- `from: (no-reply@accounts.google.com) "Security Alert"`
|
||||
- This will prevent security emails to reach the email (but won't prevent push notifications to the mobile)
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Steps to create a gmail filter</summary>
|
||||
|
||||
(Instructions from [**here**](https://support.google.com/mail/answer/6579))
|
||||
|
||||
1. Open [Gmail](https://mail.google.com/).
|
||||
2. In the search box at the top, click Show search options  .
|
||||
3. Enter your search criteria. If you want to check that your search worked correctly, see what emails show up by clicking **Search**.
|
||||
4. At the bottom of the search window, click **Create filter**.
|
||||
5. Choose what you’d like the filter to do.
|
||||
6. Click **Create filter**.
|
||||
|
||||
Check your current filter (to delete them) in [https://mail.google.com/mail/u/0/#settings/filters](https://mail.google.com/mail/u/0/#settings/filters)
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../images/image (331).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
- Create **forwarding address to forward sensitive information** (or everything) - You need manual access.
|
||||
- Create a forwarding address in [https://mail.google.com/mail/u/2/#settings/fwdandpop](https://mail.google.com/mail/u/2/#settings/fwdandpop)
|
||||
- The receiving address will need to confirm this
|
||||
- Then, set to forward all the emails while keeping a copy (remember to click on save changes):
|
||||
|
||||
<figure><img src="../../images/image (332).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
It's also possible create filters and forward only specific emails to the other email address.
|
||||
|
||||
## App passwords
|
||||
|
||||
If you managed to **compromise a google user session** and the user had **2FA**, you can **generate** an [**app password**](https://support.google.com/accounts/answer/185833?hl=en) (follow the link to see the steps). Note that **App passwords are no longer recommended by Google and are revoked** when the user **changes his Google Account password.**
|
||||
|
||||
**Even if you have an open session you will need to know the password of the user to create an app password.**
|
||||
|
||||
> [!NOTE]
|
||||
> App passwords can **only be used with accounts that have 2-Step Verification** turned on.
|
||||
|
||||
## Change 2-FA and similar
|
||||
|
||||
It's also possible to **turn off 2-FA or to enrol a new device** (or phone number) in this page [**https://myaccount.google.com/security**](https://myaccount.google.com/security)**.**\
|
||||
**It's also possible to generate passkeys (add your own device), change the password, add mobile numbers for verification phones and recovery, change the recovery email and change the security questions).**
|
||||
|
||||
> [!CAUTION]
|
||||
> To **prevent security push notifications** to reach the phone of the user, you could **sign his smartphone out** (although that would be weird) because you cannot sign him in again from here.
|
||||
>
|
||||
> It's also possible to **locate the device.**
|
||||
|
||||
**Even if you have an open session you will need to know the password of the user to change these settings.**
|
||||
|
||||
## Persistence via OAuth Apps
|
||||
|
||||
If you have **compromised the account of a user,** you can just **accept** to grant all the possible permissions to an **OAuth App**. The only problem is that Workspace can be configure to **disallow unreviewed external and/or internal OAuth apps.**\
|
||||
It is pretty common for Workspace Organizations to not trust by default external OAuth apps but trust internal ones, so if you have **enough permissions to generate a new OAuth application** inside the organization and external apps are disallowed, generate it and **use that new internal OAuth app to maintain persistence**.
|
||||
|
||||
Check the following page for more information about OAuth Apps:
|
||||
|
||||
{{#ref}}
|
||||
gws-google-platforms-phishing/
|
||||
{{#endref}}
|
||||
|
||||
## Persistence via delegation
|
||||
|
||||
You can just **delegate the account** to a different account controlled by the attacker (if you are allowed to do this). In Workspace **Organizations** this option must be **enabled**. It can be disabled for everyone, enabled from some users/groups or for everyone (usually it's only enabled for some users/groups or completely disabled).
|
||||
|
||||
<details>
|
||||
|
||||
<summary>If you are a Workspace admin check this to enable the feature</summary>
|
||||
|
||||
(Information [copied form the docs](https://support.google.com/a/answer/7223765))
|
||||
|
||||
As an administrator for your organization (for example, your work or school), you control whether users can delegate access to their Gmail account. You can let everyone have the option to delegate their account. Or, only let people in certain departments set up delegation. For example, you can:
|
||||
|
||||
- Add an administrative assistant as a delegate on your Gmail account so they can read and send email on your behalf.
|
||||
- Add a group, such as your sales department, in Groups as a delegate to give everyone access to one Gmail account.
|
||||
|
||||
Users can only delegate access to another user in the same organization, regardless of their domain or their organizational unit.
|
||||
|
||||
#### Delegation limits & restrictions
|
||||
|
||||
- **Allow users to grant their mailbox access to a Google group** option: To use this option, it must be enabled for the OU of the delegated account and for each group member's OU. Group members that belong to an OU without this option enabled can't access the delegated account.
|
||||
- With typical use, 40 delegated users can access a Gmail account at the same time. Above-average use by one or more delegates might reduce this number.
|
||||
- Automated processes that frequently access Gmail might also reduce the number of delegates who can access an account at the same time. These processes include APIs or browser extensions that access Gmail frequently.
|
||||
- A single Gmail account supports up to 1,000 unique delegates. A group in Groups counts as one delegate toward the limit.
|
||||
- Delegation does not increase the limits for a Gmail account. Gmail accounts with delegated users have the standard Gmail account limits and policies. For details, visit [Gmail limits and policies](https://support.google.com/a/topic/28609).
|
||||
|
||||
#### Step 1: Turn on Gmail delegation for your users
|
||||
|
||||
**Before you begin:** To apply the setting for certain users, put their accounts in an [organizational unit](https://support.google.com/a/topic/1227584).
|
||||
|
||||
1. [Sign in](https://admin.google.com/) to your [Google Admin console](https://support.google.com/a/answer/182076).
|
||||
|
||||
Sign in using an _administrator account_, not your current account CarlosPolop@gmail.com
|
||||
|
||||
2. In the Admin console, go to Menu  **Apps****Google Workspace****Gmail****User settings**.
|
||||
3. To apply the setting to everyone, leave the top organizational unit selected. Otherwise, select a child [organizational unit](https://support.google.com/a/topic/1227584).
|
||||
4. Click **Mail delegation**.
|
||||
5. Check the **Let users delegate access to their mailbox to other users in the domain** box.
|
||||
6. (Optional) To let users specify what sender information is included in delegated messages sent from their account, check the **Allow users to customize this setting** box.
|
||||
7. Select an option for the default sender information that's included in messages sent by delegates:
|
||||
- **Show the account owner and the delegate who sent the email**—Messages include the email addresses of the Gmail account owner and the delegate.
|
||||
- **Show the account owner only**—Messages include the email address of only the Gmail account owner. The delegate email address is not included.
|
||||
8. (Optional) To let users add a group in Groups as a delegate, check the **Allow users to grant their mailbox access to a Google group** box.
|
||||
9. Click **Save**. If you configured a child organizational unit, you might be able to **Inherit** or **Override** a parent organizational unit's settings.
|
||||
10. (Optional) To turn on Gmail delegation for other organizational units, repeat steps 3–9.
|
||||
|
||||
Changes can take up to 24 hours but typically happen more quickly. [Learn more](https://support.google.com/a/answer/7514107)
|
||||
|
||||
#### Step 2: Have users set up delegates for their accounts
|
||||
|
||||
After you turn on delegation, your users go to their Gmail settings to assign delegates. Delegates can then read, send, and receive messages on behalf of the user.
|
||||
|
||||
For details, direct users to [Delegate and collaborate on email](https://support.google.com/a/users/answer/138350).
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>From a regular suer, check here the instructions to try to delegate your access</summary>
|
||||
|
||||
(Info copied [**from the docs**](https://support.google.com/mail/answer/138350))
|
||||
|
||||
You can add up to 10 delegates.
|
||||
|
||||
If you're using Gmail through your work, school, or other organization:
|
||||
|
||||
- You can add up to 1000 delegates within your organization.
|
||||
- With typical use, 40 delegates can access a Gmail account at the same time.
|
||||
- If you use automated processes, such as APIs or browser extensions, a few delegates can access a Gmail account at the same time.
|
||||
|
||||
1. On your computer, open [Gmail](https://mail.google.com/). You can't add delegates from the Gmail app.
|
||||
2. In the top right, click Settings  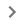 **See all settings**.
|
||||
3. Click the **Accounts and Import** or **Accounts** tab.
|
||||
4. In the "Grant access to your account" section, click **Add another account**. If you’re using Gmail through your work or school, your organization may restrict email delegation. If you don’t see this setting, contact your admin.
|
||||
- If you don't see Grant access to your account, then it's restricted.
|
||||
5. Enter the email address of the person you want to add. If you’re using Gmail through your work, school, or other organization, and your admin allows it, you can enter the email address of a group. This group must have the same domain as your organization. External members of the group are denied delegation access.\
|
||||
\
|
||||
**Important:** If the account you delegate is a new account or the password was reset, the Admin must turn off the requirement to change password when you first sign in.
|
||||
|
||||
- [Learn how an Admin can create a user](https://support.google.com/a/answer/33310).
|
||||
- [Learn how an Admin can reset passwords](https://support.google.com/a/answer/33319).
|
||||
|
||||
6\. Click **Next Step** 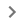 **Send email to grant access**.
|
||||
|
||||
The person you added will get an email asking them to confirm. The invitation expires after a week.
|
||||
|
||||
If you added a group, all group members will become delegates without having to confirm.
|
||||
|
||||
Note: It may take up to 24 hours for the delegation to start taking effect.
|
||||
|
||||
</details>
|
||||
|
||||
## Persistence via Android App
|
||||
|
||||
If you have a **session inside victims google account** you can browse to the **Play Store** and might be able to **install malware** you have already uploaded to the store directly **to the phone** to maintain persistence and access the victims phone.
|
||||
|
||||
## **Persistence via** App Scripts
|
||||
|
||||
You can create **time-based triggers** in App Scripts, so if the App Script is accepted by the user, it will be **triggered** even **without the user accessing it**. For more information about how to do this check:
|
||||
|
||||
{{#ref}}
|
||||
gws-google-platforms-phishing/gws-app-scripts.md
|
||||
{{#endref}}
|
||||
|
||||
## References
|
||||
|
||||
- [https://www.youtube-nocookie.com/embed/6AsVUS79gLw](https://www.youtube-nocookie.com/embed/6AsVUS79gLw) - Matthew Bryant - Hacking G Suite: The Power of Dark Apps Script Magic
|
||||
- [https://www.youtube.com/watch?v=KTVHLolz6cE](https://www.youtube.com/watch?v=KTVHLolz6cE) - Mike Felch and Beau Bullock - OK Google, How do I Red Team GSuite?
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
Reference in New Issue
Block a user