mirror of
https://github.com/aquasecurity/trivy.git
synced 2025-12-22 07:10:41 -08:00
docs: restructure docs and add tutorials (#2883)
Co-authored-by: knqyf263 <knqyf263@gmail.com>
This commit is contained in:
4
docs/tutorials/integrations/aws-codepipeline.md
Normal file
4
docs/tutorials/integrations/aws-codepipeline.md
Normal file
@@ -0,0 +1,4 @@
|
||||
# AWS CodePipeline
|
||||
See [this blog post][blog] for an example of using Trivy within AWS CodePipeline.
|
||||
|
||||
[blog]: https://aws.amazon.com/blogs/containers/scanning-images-with-trivy-in-an-aws-codepipeline/
|
||||
51
docs/tutorials/integrations/aws-security-hub.md
Normal file
51
docs/tutorials/integrations/aws-security-hub.md
Normal file
@@ -0,0 +1,51 @@
|
||||
# AWS Security Hub
|
||||
|
||||
## Upload findings to Security Hub
|
||||
|
||||
In the following example using the template `asff.tpl`, [ASFF](https://docs.aws.amazon.com/securityhub/latest/userguide/securityhub-findings-format.html) file can be generated.
|
||||
|
||||
```
|
||||
$ AWS_REGION=us-west-1 AWS_ACCOUNT_ID=123456789012 trivy image --format template --template "@contrib/asff.tpl" -o report.asff golang:1.12-alpine
|
||||
```
|
||||
|
||||
ASFF template needs AWS_REGION and AWS_ACCOUNT_ID from environment variables.
|
||||
|
||||
The Product [ARN](https://docs.aws.amazon.com/general/latest/gr/aws-arns-and-namespaces.html) field follows the pattern below to match what AWS requires for the [product resource type](https://github.com/awsdocs/aws-security-hub-user-guide/blob/master/doc_source/securityhub-partner-providers.md#aqua-security--aqua-cloud-native-security-platform-sends-findings).
|
||||
|
||||
{% raw %}
|
||||
```
|
||||
"ProductArn": "arn:aws:securityhub:{{ env "AWS_REGION" }}::product/aquasecurity/aquasecurity",
|
||||
```
|
||||
{% endraw %}
|
||||
|
||||
In order to upload results you must first run [enable-import-findings-for-product](https://docs.aws.amazon.com/cli/latest/reference/securityhub/enable-import-findings-for-product.html) like:
|
||||
|
||||
```
|
||||
aws securityhub enable-import-findings-for-product --product-arn arn:aws:securityhub:<AWS_REGION>::product/aquasecurity/aquasecurity
|
||||
```
|
||||
|
||||
Then, you can upload it with AWS CLI.
|
||||
|
||||
```
|
||||
$ aws securityhub batch-import-findings --findings file://report.asff
|
||||
```
|
||||
|
||||
### Note
|
||||
|
||||
The [batch-import-findings](https://docs.aws.amazon.com/cli/latest/reference/securityhub/batch-import-findings.html#options) command limits the number of findings uploaded to 100 per request. The best known workaround to this problem is using [jq](https://stedolan.github.io/jq/) to run the following command
|
||||
|
||||
```
|
||||
jq '.[:100]' report.asff 1> short_report.asff
|
||||
```
|
||||
|
||||
## Customize
|
||||
You can customize [asff.tpl](https://github.com/aquasecurity/trivy/blob/main/contrib/asff.tpl)
|
||||
|
||||
```
|
||||
$ export AWS_REGION=us-west-1
|
||||
$ export AWS_ACCOUNT_ID=123456789012
|
||||
$ trivy image --format template --template "@your-asff.tpl" -o report.asff golang:1.12-alpine
|
||||
```
|
||||
|
||||
## Reference
|
||||
https://aws.amazon.com/blogs/security/how-to-build-ci-cd-pipeline-container-vulnerability-scanning-trivy-and-aws-security-hub/
|
||||
22
docs/tutorials/integrations/azure-devops.md
Normal file
22
docs/tutorials/integrations/azure-devops.md
Normal file
@@ -0,0 +1,22 @@
|
||||
# Azure Devops
|
||||
|
||||
- Here is the [Azure DevOps Pipelines Task for Trivy][action]
|
||||
|
||||
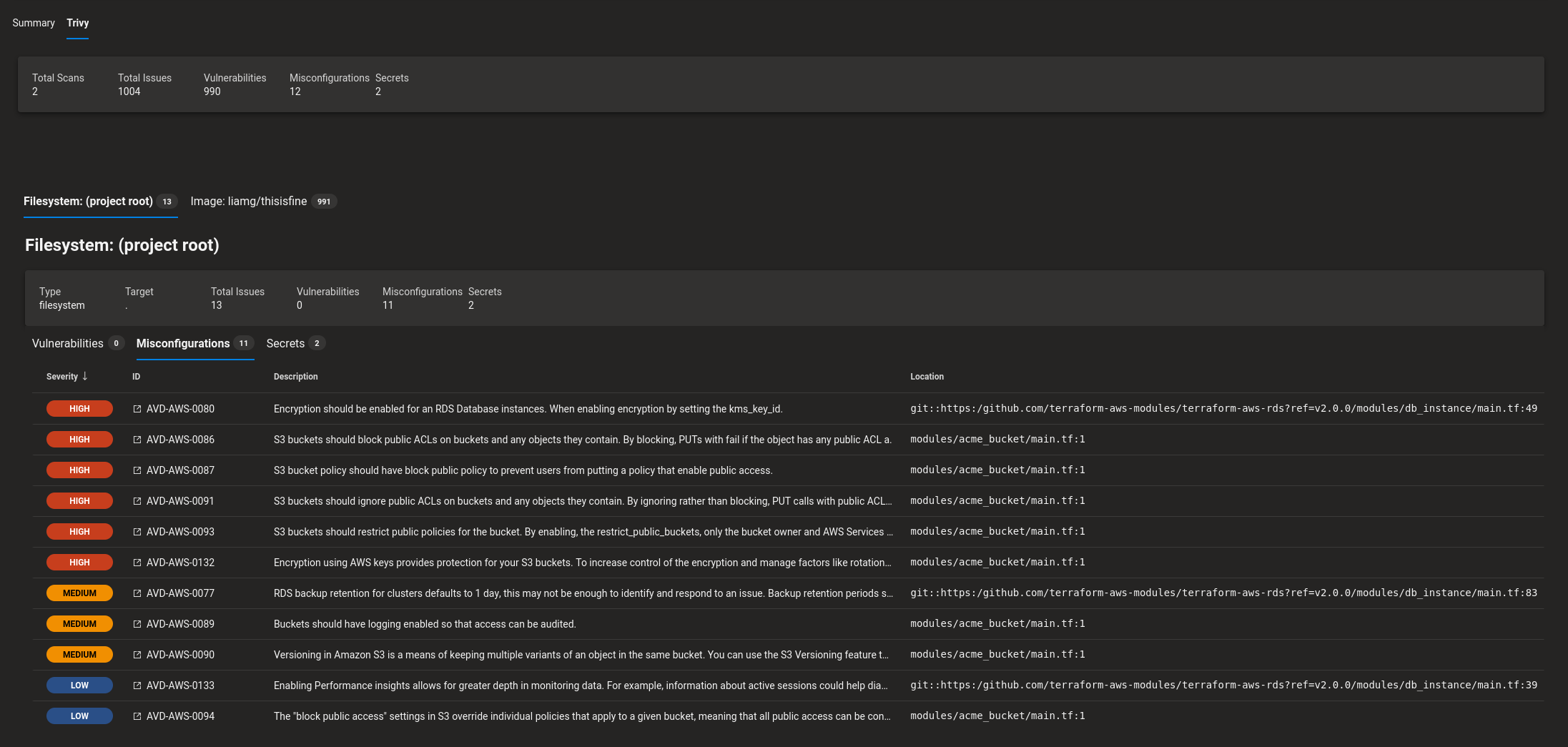
|
||||
|
||||
### [Use ImageCleaner to clean up stale images on your Azure Kubernetes Service cluster][azure2]
|
||||
|
||||
It's common to use pipelines to build and deploy images on Azure Kubernetes Service (AKS) clusters. While great for image creation, this process often doesn't account for the stale images left behind and can lead to image bloat on cluster nodes. These images can present security issues as they may contain vulnerabilities. By cleaning these unreferenced images, you can remove an area of risk in your clusters. When done manually, this process can be time intensive, which ImageCleaner can mitigate via automatic image identification and removal.
|
||||
|
||||
Vulnerability is determined based on a trivy scan, after which images with a LOW, MEDIUM, HIGH, or CRITICAL classification are flagged. An updated ImageList will be automatically generated by ImageCleaner based on a set time interval, and can also be supplied manually.
|
||||
### [Microsoft Defender for container registries and Trivy][azure]
|
||||
|
||||
This blog explains how to scan your Azure Container Registry-based container images with the integrated vulnerability scanner when they're built as part of your GitHub workflows.
|
||||
|
||||
To set up the scanner, you'll need to enable Microsoft Defender for Containers and the CI/CD integration. When your CI/CD workflows push images to your registries, you can view registry scan results and a summary of CI/CD scan results.
|
||||
|
||||
The findings of the CI/CD scans are an enrichment to the existing registry scan findings by Qualys. Defender for Cloud's CI/CD scanning is powered by Aqua Trivy
|
||||
|
||||
[action]: https://github.com/aquasecurity/trivy-azure-pipelines-task
|
||||
[azure]: https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-containers-cicd
|
||||
[azure2]: https://docs.microsoft.com/en-us/azure/aks/image-cleaner?tabs=azure-cli
|
||||
5
docs/tutorials/integrations/bitbucket.md
Normal file
5
docs/tutorials/integrations/bitbucket.md
Normal file
@@ -0,0 +1,5 @@
|
||||
# Bitbucket Pipelines
|
||||
|
||||
See [trivy-pipe][trivy-pipe] for the details.
|
||||
|
||||
[trivy-pipe]: https://github.com/aquasecurity/trivy-pipe
|
||||
34
docs/tutorials/integrations/circleci.md
Normal file
34
docs/tutorials/integrations/circleci.md
Normal file
@@ -0,0 +1,34 @@
|
||||
# CircleCI
|
||||
|
||||
```
|
||||
$ cat .circleci/config.yml
|
||||
jobs:
|
||||
build:
|
||||
docker:
|
||||
- image: docker:stable-git
|
||||
steps:
|
||||
- checkout
|
||||
- setup_remote_docker
|
||||
- run:
|
||||
name: Build image
|
||||
command: docker build -t trivy-ci-test:${CIRCLE_SHA1} .
|
||||
- run:
|
||||
name: Install trivy
|
||||
command: |
|
||||
apk add --update-cache --upgrade curl
|
||||
curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/main/contrib/install.sh | sh -s -- -b /usr/local/bin
|
||||
- run:
|
||||
name: Scan the local image with trivy
|
||||
command: trivy image --exit-code 0 --no-progress trivy-ci-test:${CIRCLE_SHA1}
|
||||
workflows:
|
||||
version: 2
|
||||
release:
|
||||
jobs:
|
||||
- build
|
||||
```
|
||||
|
||||
[Example][example]
|
||||
[Repository][repository]
|
||||
|
||||
[example]: https://circleci.com/gh/aquasecurity/trivy-ci-test
|
||||
[repository]: https://github.com/aquasecurity/trivy-ci-test
|
||||
9
docs/tutorials/integrations/github-actions.md
Normal file
9
docs/tutorials/integrations/github-actions.md
Normal file
@@ -0,0 +1,9 @@
|
||||
# GitHub Actions
|
||||
|
||||
- Here is the [Trivy GitHub Action][action]
|
||||
- The Microsoft Azure team have written a [container-scan action][azure] that uses Trivy and Dockle
|
||||
- For full control over the options specified to Trivy, this [blog post][blog] describes adding Trivy into your own GitHub action workflows
|
||||
|
||||
[action]: https://github.com/aquasecurity/trivy-action
|
||||
[azure]: https://github.com/Azure/container-scan
|
||||
[blog]: https://blog.aquasec.com/devsecops-with-trivy-github-actions
|
||||
181
docs/tutorials/integrations/gitlab-ci.md
Normal file
181
docs/tutorials/integrations/gitlab-ci.md
Normal file
@@ -0,0 +1,181 @@
|
||||
# GitLab CI
|
||||
|
||||
GitLab 15.0 includes [free](https://gitlab.com/groups/gitlab-org/-/epics/2233) integration with Trivy.
|
||||
|
||||
To [configure container scanning with Trivy in GitLab](https://docs.gitlab.com/ee/user/application_security/container_scanning/#configuration), simply include the CI template in your `.gitlab-ci.yml` file:
|
||||
|
||||
```yaml
|
||||
include:
|
||||
- template: Security/Container-Scanning.gitlab-ci.yml
|
||||
```
|
||||
|
||||
If you're a GitLab 14.x Ultimate customer, you can use the same configuration above.
|
||||
|
||||
Alternatively, you can always use the example configurations below.
|
||||
|
||||
```yaml
|
||||
stages:
|
||||
- test
|
||||
|
||||
trivy:
|
||||
stage: test
|
||||
image: docker:stable
|
||||
services:
|
||||
- name: docker:dind
|
||||
entrypoint: ["env", "-u", "DOCKER_HOST"]
|
||||
command: ["dockerd-entrypoint.sh"]
|
||||
variables:
|
||||
DOCKER_HOST: tcp://docker:2375/
|
||||
DOCKER_DRIVER: overlay2
|
||||
# See https://github.com/docker-library/docker/pull/166
|
||||
DOCKER_TLS_CERTDIR: ""
|
||||
IMAGE: trivy-ci-test:$CI_COMMIT_SHA
|
||||
TRIVY_NO_PROGRESS: "true"
|
||||
TRIVY_CACHE_DIR: ".trivycache/"
|
||||
before_script:
|
||||
- export TRIVY_VERSION=$(wget -qO - "https://api.github.com/repos/aquasecurity/trivy/releases/latest" | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/')
|
||||
- echo $TRIVY_VERSION
|
||||
- wget --no-verbose https://github.com/aquasecurity/trivy/releases/download/v${TRIVY_VERSION}/trivy_${TRIVY_VERSION}_Linux-64bit.tar.gz -O - | tar -zxvf -
|
||||
allow_failure: true
|
||||
script:
|
||||
# Build image
|
||||
- docker build -t $IMAGE .
|
||||
# Build report
|
||||
- ./trivy image --exit-code 0 --format template --template "@contrib/gitlab.tpl" -o gl-container-scanning-report.json $IMAGE
|
||||
# Print report
|
||||
- ./trivy image --exit-code 0 --severity HIGH $IMAGE
|
||||
# Fail on severe vulnerabilities
|
||||
- ./trivy image --exit-code 1 --severity CRITICAL $IMAGE
|
||||
cache:
|
||||
paths:
|
||||
- .trivycache/
|
||||
# Enables https://docs.gitlab.com/ee/user/application_security/container_scanning/ (Container Scanning report is available on GitLab EE Ultimate or GitLab.com Gold)
|
||||
artifacts:
|
||||
reports:
|
||||
container_scanning: gl-container-scanning-report.json
|
||||
```
|
||||
|
||||
[Example][example]
|
||||
[Repository][repository]
|
||||
|
||||
### GitLab CI using Trivy container
|
||||
|
||||
To scan a previously built image that has already been pushed into the
|
||||
GitLab container registry the following CI job manifest can be used.
|
||||
Note that `entrypoint` needs to be unset for the `script` section to work.
|
||||
In case of a non-public GitLab project Trivy additionally needs to
|
||||
authenticate to the registry to be able to pull your application image.
|
||||
Finally, it is not necessary to clone the project repo as we only work
|
||||
with the container image.
|
||||
|
||||
```yaml
|
||||
container_scanning:
|
||||
image:
|
||||
name: docker.io/aquasec/trivy:latest
|
||||
entrypoint: [""]
|
||||
variables:
|
||||
# No need to clone the repo, we exclusively work on artifacts. See
|
||||
# https://docs.gitlab.com/ee/ci/runners/README.html#git-strategy
|
||||
GIT_STRATEGY: none
|
||||
TRIVY_USERNAME: "$CI_REGISTRY_USER"
|
||||
TRIVY_PASSWORD: "$CI_REGISTRY_PASSWORD"
|
||||
TRIVY_AUTH_URL: "$CI_REGISTRY"
|
||||
TRIVY_NO_PROGRESS: "true"
|
||||
TRIVY_CACHE_DIR: ".trivycache/"
|
||||
FULL_IMAGE_NAME: $CI_REGISTRY_IMAGE:$CI_COMMIT_REF_SLUG
|
||||
script:
|
||||
- trivy --version
|
||||
# cache cleanup is needed when scanning images with the same tags, it does not remove the database
|
||||
- time trivy image --clear-cache
|
||||
# update vulnerabilities db
|
||||
- time trivy image --download-db-only
|
||||
# Builds report and puts it in the default workdir $CI_PROJECT_DIR, so `artifacts:` can take it from there
|
||||
- time trivy image --exit-code 0 --format template --template "@/contrib/gitlab.tpl"
|
||||
--output "$CI_PROJECT_DIR/gl-container-scanning-report.json" "$FULL_IMAGE_NAME"
|
||||
# Prints full report
|
||||
- time trivy image --exit-code 0 "$FULL_IMAGE_NAME"
|
||||
# Fail on critical vulnerabilities
|
||||
- time trivy image --exit-code 1 --severity CRITICAL "$FULL_IMAGE_NAME"
|
||||
cache:
|
||||
paths:
|
||||
- .trivycache/
|
||||
# Enables https://docs.gitlab.com/ee/user/application_security/container_scanning/ (Container Scanning report is available on GitLab EE Ultimate or GitLab.com Gold)
|
||||
artifacts:
|
||||
when: always
|
||||
reports:
|
||||
container_scanning: gl-container-scanning-report.json
|
||||
tags:
|
||||
- docker-runner
|
||||
```
|
||||
|
||||
[example]: https://gitlab.com/aquasecurity/trivy-ci-test/pipelines
|
||||
[repository]: https://github.com/aquasecurity/trivy-ci-test
|
||||
|
||||
### GitLab CI alternative template
|
||||
|
||||
Depending on the edition of gitlab you have or your desired workflow, the
|
||||
container scanning template may not meet your needs. As an addition to the
|
||||
above container scanning template, a template for
|
||||
[code climate](https://docs.gitlab.com/ee/user/project/merge_requests/code_quality.html)
|
||||
has been included. The key things to update from the above examples are
|
||||
the `template` and `report` type. An updated example is below.
|
||||
|
||||
```yaml
|
||||
stages:
|
||||
- test
|
||||
|
||||
trivy:
|
||||
stage: test
|
||||
image: docker:stable
|
||||
services:
|
||||
- name: docker:dind
|
||||
entrypoint: ["env", "-u", "DOCKER_HOST"]
|
||||
command: ["dockerd-entrypoint.sh"]
|
||||
variables:
|
||||
DOCKER_HOST: tcp://docker:2375/
|
||||
DOCKER_DRIVER: overlay2
|
||||
# See https://github.com/docker-library/docker/pull/166
|
||||
DOCKER_TLS_CERTDIR: ""
|
||||
IMAGE: trivy-ci-test:$CI_COMMIT_SHA
|
||||
TRIVY_NO_PROGRESS: "true"
|
||||
TRIVY_CACHE_DIR: ".trivycache/"
|
||||
before_script:
|
||||
- export TRIVY_VERSION=$(wget -qO - "https://api.github.com/repos/aquasecurity/trivy/releases/latest" | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/')
|
||||
- echo $TRIVY_VERSION
|
||||
- wget --no-verbose https://github.com/aquasecurity/trivy/releases/download/v${TRIVY_VERSION}/trivy_${TRIVY_VERSION}_Linux-64bit.tar.gz -O - | tar -zxvf -
|
||||
allow_failure: true
|
||||
script:
|
||||
# Build image
|
||||
- docker build -t $IMAGE .
|
||||
# Image report
|
||||
- ./trivy image --exit-code 0 --format template --template "@contrib/gitlab-codequality.tpl" -o gl-codeclimate-image.json $IMAGE
|
||||
# Filesystem report
|
||||
- ./trivy filesystem --security-checks config,vuln --exit-code 0 --format template --template "@contrib/gitlab-codequality.tpl" -o gl-codeclimate-fs.json .
|
||||
# Combine report
|
||||
- apk update && apk add jq
|
||||
- jq -s 'add' gl-codeclimate-image.json gl-codeclimate-fs.json > gl-codeclimate.json
|
||||
cache:
|
||||
paths:
|
||||
- .trivycache/
|
||||
# Enables https://docs.gitlab.com/ee/user/application_security/container_scanning/ (Container Scanning report is available on GitLab EE Ultimate or GitLab.com Gold)
|
||||
artifacts:
|
||||
paths:
|
||||
- gl-codeclimate.json
|
||||
reports:
|
||||
codequality: gl-codeclimate.json
|
||||
```
|
||||
|
||||
Currently gitlab only supports a single code quality report. There is an
|
||||
open [feature request](https://gitlab.com/gitlab-org/gitlab/-/issues/9014)
|
||||
to support multiple reports. Until this has been implemented, if you
|
||||
already have a code quality report in your pipeline, you can use
|
||||
`jq` to combine reports. Depending on how you name your artifacts, it may
|
||||
be necessary to rename the artifact if you want to reuse the name. To then
|
||||
combine the previous artifact with the output of trivy, the following `jq`
|
||||
command can be used, `jq -s 'add' prev-codeclimate.json trivy-codeclimate.json > gl-codeclimate.json`.
|
||||
|
||||
### GitLab CI alternative template example report
|
||||
|
||||
You'll be able to see a full report in the GitLab pipeline code quality UI, where filesystem vulnerabilities and misconfigurations include links to the flagged files and image vulnerabilities report the image/os or runtime/library that the vulnerability originates from instead.
|
||||
|
||||

|
||||
2
docs/tutorials/integrations/index.md
Normal file
2
docs/tutorials/integrations/index.md
Normal file
@@ -0,0 +1,2 @@
|
||||
# Integrations
|
||||
Scan your image automatically as part of your CI workflow, failing the workflow if a vulnerability is found. When you don't want to fail the test, specify `--exit-code 0`.
|
||||
29
docs/tutorials/integrations/travis-ci.md
Normal file
29
docs/tutorials/integrations/travis-ci.md
Normal file
@@ -0,0 +1,29 @@
|
||||
# Travis CI
|
||||
|
||||
```
|
||||
$ cat .travis.yml
|
||||
services:
|
||||
- docker
|
||||
|
||||
env:
|
||||
global:
|
||||
- COMMIT=${TRAVIS_COMMIT::8}
|
||||
|
||||
before_install:
|
||||
- docker build -t trivy-ci-test:${COMMIT} .
|
||||
- export VERSION=$(curl --silent "https://api.github.com/repos/aquasecurity/trivy/releases/latest" | grep '"tag_name":' | sed -E 's/.*"v([^"]+)".*/\1/')
|
||||
- wget https://github.com/aquasecurity/trivy/releases/download/v${VERSION}/trivy_${VERSION}_Linux-64bit.tar.gz
|
||||
- tar zxvf trivy_${VERSION}_Linux-64bit.tar.gz
|
||||
script:
|
||||
- ./trivy image --exit-code 0 --severity HIGH --no-progress trivy-ci-test:${COMMIT}
|
||||
- ./trivy image --exit-code 1 --severity CRITICAL --no-progress trivy-ci-test:${COMMIT}
|
||||
cache:
|
||||
directories:
|
||||
- $HOME/.cache/trivy
|
||||
```
|
||||
|
||||
[Example][example]
|
||||
[Repository][repository]
|
||||
|
||||
[example]: https://travis-ci.org/aquasecurity/trivy-ci-test
|
||||
[repository]: https://github.com/aquasecurity/trivy-ci-test
|
||||
Reference in New Issue
Block a user